In the previous technique, after writing the DLL pathname, CreateRemoteThread() was invoked to create a thread in the target process, which in turn called LoadLibrary() to load the malicious DLL. The APC injection technique is similar to remote DLL injection, but instead of using CreateRemoteThread(), a malware makes use of Asynchronous Procedure Calls (APCs) to force the thread of a target process to load the malicious DLL.
An APC is a function that executes asynchronously in the context of a particular thread. Each thread contains a queue of APCs that will be executed when the target thread enters an alertable state. As per Microsoft documentation (https://msdn.microsoft.com/en-us/library/windows/desktop/ms681951(v=vs.85).aspx), a thread enters an alertable state if it calls one of the following functions:
SleepEx(),
SignalObjectAndWait()
MsgWaitForMultipleObjectsEx()
WaitForMultipleObjectsEx()
WaitForSingleObjectEx()
The way the APC injection technique works is, a malware process identifies the thread in the target process (the process into which the code will be injected) that is in an alertable state, or likely to go into an alertable state. It then places the custom code in that thread's APC queue by using the QueueUserAPC() function. The idea of queuing the custom code is that, when the thread enters the alertable state, the custom code gets picked up from the APC queue, and it gets executed by the thread of the target process.
The following steps describe a malware sample using APC injection to load a malicious DLL into the Internet Explorer (iexplore.exe) process. This technique starts with the same four steps as remote DLL injection (in other words, it opens a handle to iexplore.exe, allocates memory in the target process, copies the malicious DLL pathname into the allocated memory, and determines the address of Loadlibrary()). It then follows these steps to force the remote thread to load the malicious DLL:
- It opens a handle to the thread of the target process using the OpenThread() API. In the following screenshot, the 3rd argument, 0xBEC(3052), is the thread ID (TID) of the iexplore.exe process. The return value of OpenThread() is the handle to the thread of iexplore.exe:

- The malware process then calls QueueUserAPC() to queue the APC function in the Internet Explorer thread's APC queue. In the following screenshot, the 1st argument to QueueUserAPC() is the pointer to the APC function that the malware wants the target thread to execute. In this case, the APC function is the LoadLibrary() whose address was determined previously. The 2nd argument, 0x22c, is the handle to the target thread of iexplore.exe. The 3rd argument, 0x2270000, is the address in the target process (iexplore.exe) memory containing the full path to the malicious DLL; this argument will automatically be passed as the parameter to the APC function (LoadLibrary()) when the thread executes it:

The following screenshot shows the content of the address 0x2270000 in Internet Explorer's process memory (this was passed as the 3rd argument to QueueUserAPC()); this address contains the full path to the DLL that was previously written by the malware:
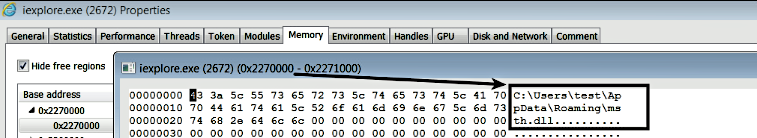
At this point, the injection is complete, and when the thread of the target process enters an alertable state, the thread executes LoadLibrary() from the APC queue, and the full path to the DLL is passed as an argument to LoadLibrary(). As a result, the malicious DLL gets loaded into the target process address space, which in turn invokes the DLLMain() function containing the malicious code.
