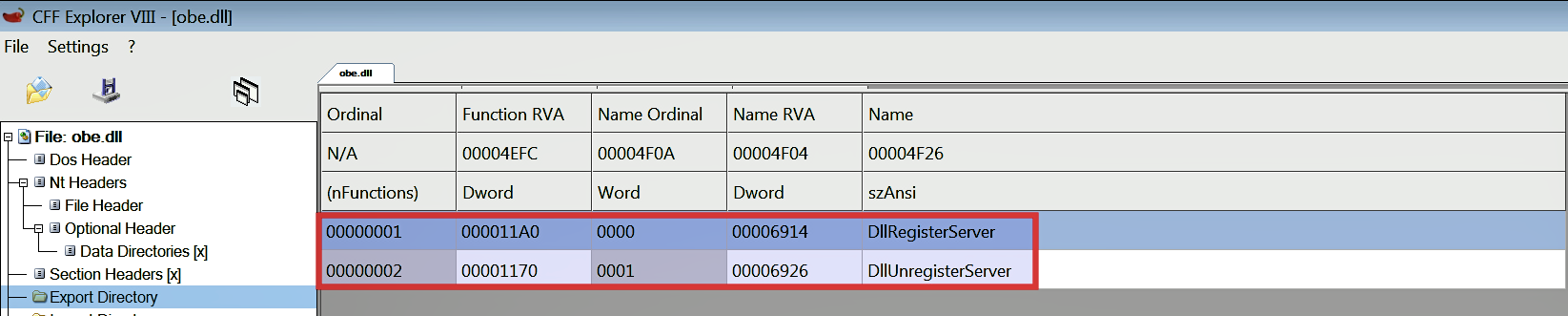
In this example, we will look at another malicious DLL (obe.dll). The following screenshot shows two functions (DllRegisterServer and DllUnRegisterServer) exported by the DLL:
The DLL sample was run with the following command. Even though obe.dll was loaded into the memory of rundll32.exe, it did not trigger any behavior. This is because DLL's entry point function does not implement any functionality:
C:>rundll32.exe c:samplesobe.dll,test
On the other hand, running the sample with the DllRegisterServer function as shown below, triggered an HTTPS communication to the C2 server. From this, it can be deduced that DLLRegisterServer implements the network functionality:
C:>rundll32.exe c:samplesobe.dll,DllRegisterServer
The following screenshot shows the network traffic captured by Wireshark:

You can write a script to determine all the exported functions (as covered in Chapter 2, Static Analysis) in a DLL and call them in sequence while running the monitoring tools. This technique can help in understanding the functionality of each exported function. DLLRunner (https://github.com/Neo23x0/DLLRunner) is a Python script that executes all exported functions in a DLL.
