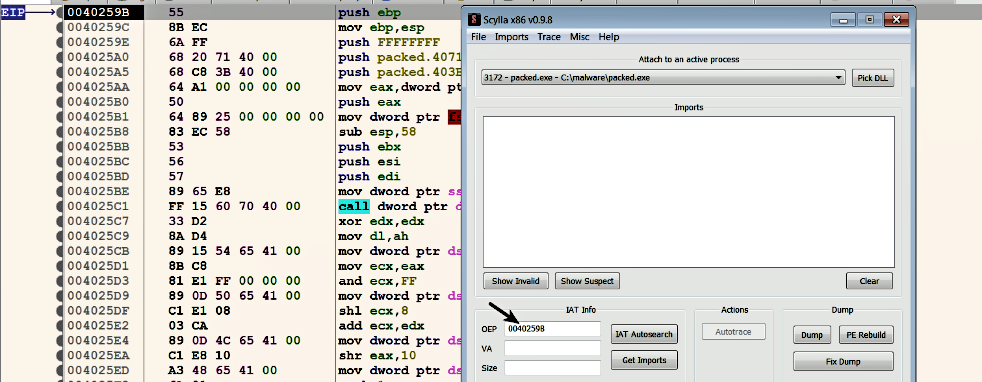
Now that we have located the OEP, the next step is to dump the process memory to disk. To dump the process, we will use a tool named Scylla (https://github.com/NtQuery/Scylla); it is a great tool to dump the process memory and to rebuild the import address table. One of the great features of x64dbg is that it integrates Scylla, and Scylla can be launched by clicking on Plugins | Scylla, (or Ctrl + I). To dump the process memory, while the execution is paused at the OEP, launch Scylla, make sure that the OEP field is set to correct address as follows; if not you need to set it manually and click on the Dump button and save the dumped executable to disk (in this case, it was saved as packed_dump.exe):
Now, when you load the dumped executable into IDA, you will see the entire list of built-in functions (which was not visible in the packed program before), and the function code is no longer obfuscated, but still, the imports are not visible, and the API call displays addresses instead of names. To overcome this problem, you need to rebuild the import table of the packed binary:

