A useful tool to search for the cryptographic signatures in a file or process is Signsrch, which can be downloaded from http://aluigi.altervista.org/mytoolz.htm. This tool relies on cryptographic signatures to detect encryption algorithms. The cryptographic signatures are located in a text file, signsrch.sig. In the following output, when signsrch is run with the -e option, it displays the relative virtual addresses where the DES signatures were detected in the binary:
C:signsrch>signsrch.exe -e kav.exe
Signsrch 0.2.4
by Luigi Auriemma
e-mail: [email protected]
web: aluigi.org
optimized search function by Andrew http://www.team5150.com/~andrew/
disassembler engine by Oleh Yuschuk
- open file "kav.exe"
- 91712 bytes allocated
- load signatures
- open file C:signsrchsignsrch.sig
- 3075 signatures in the database
- start 1 threads
- start signatures scanning:
offset num description [bits.endian.size]
--------------------------------------------
00410438 1918 DES initial permutation IP [..64]
00410478 2330 DES_fp [..64]
004104b8 2331 DES_ei [..48]
004104e8 2332 DES_p32i [..32]
00410508 1920 DES permuted choice table (key) [..56]
00410540 1921 DES permuted choice key (table) [..48]
00410580 1922 DES S-boxes [..512]
[Removed]
Once you know the address where the cryptographic indicators are found, you can use IDA to navigate to the address. For example, if you want to navigate to the address 00410438 (DES initial permutation IP), load the binary in IDA and select Jump | Jump to address (or G hotkey) and enter the address as shown here:

Once you click on OK, you will reach the address containing the indicator (in this case, DES initial permutation IP, labeled as DES_ip) as shown in the following screenshot:

Now, to know where and how this crypto indicator is used in the code, you can use the cross-references (Xrefs-to) feature. Using the cross-references (Xrefs to) feature shows that DES_ip is referenced within a function sub_4032B0 at address 0x4032E0 (loc_4032E0):
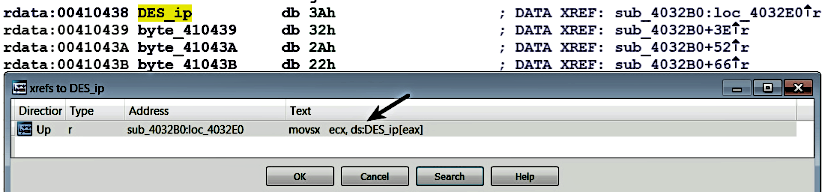
Now, navigating to the address 0x4032E0 directly lands you inside the DES encryption function, as shown in the following screenshot. Once the encryption function is found, you can use cross-references to examine it further to understand in what context the encryption function gets called and the key that is used to encrypt the data:

Instead of using the -e option to locate the signature and then manually navigating to the code where the signature is used, you can use the -F option, which will give you the address of the first instruction where the crypto indicator is used. In the following output, running signsrch with the -F option directly displays the address 0x4032E0 where the crypto indicator DES initial permutation IP (DES_ip) is used in the code:
C:signsrch>signsrch.exe -F kav.exe
[removed]
offset num description [bits.endian.size]
--------------------------------------------
[removed]
004032e0 1918 DES initial permutation IP [..64]
00403490 2330 DES_fp [..64]
The -e and -F options display the addresses relative to the preferred base address specified in the PE header. For instance, if the preferred base address of the binary is 0x00400000, then the addresses returned by the -e and -F options are determined by adding the relative virtual address with the preferred base address 0x00400000. When you run (or debug) the binary, it can be loaded at any address other than the preferred base address (for example, 0x01350000). If you wish to locate the address of the crypto indicator in a running process or while you are debugging a binary (in IDA or x64dbg), then you can run the signsrch with the -P <pid or process name> option. The -P option automatically determines the base address where the executable is loaded, and then calculates the virtual address of crypto signatures, as shown here:
C:signsrch>signsrch.exe -P kav.exe
[removed]
- 01350000 0001b000 C:Users estDesktopkav.exe
- pid 3068
- base address 0x01350000
- offset 01350000 size 0001b000
- 110592 bytes allocated
- load signatures
- open file C:signsrchsignsrch.sig
- 3075 signatures in the database
- start 1 threads
- start signatures scanning:
offset num description [bits.endian.size]
--------------------------------------------
01360438 1918 DES initial permutation IP [..64]
01360478 2330 DES_fp [..64]
013604b8 2331 DES_ei [..48]
