The resources required by the executable file such as icons, menu, dialog, and strings are stored in the resource section (.rsrc) of an executable file. Often, attackers store information such as additional binary, and decoy documents, configuration data in the resource section, so examining the resource can reveal valuable information about a binary. The resource section also contains version information that can reveal information about the origin, company name, program author details, and copyright information.
Resource Hacker (http://www.angusj.com/resourcehacker/) is a great tool to examine, view, and extract the resource from a suspect binary. Let's take an example of binary that looks like an Excel file on the disk (notice how the file extension is changed to .xls.exe), as shown here:

Loading a malicious binary in resource hacker shows three resources (Icon, Binary, and Icon Group). The malware specimen uses the icon of Microsoft Excel (to give the appearance of an excel sheet):

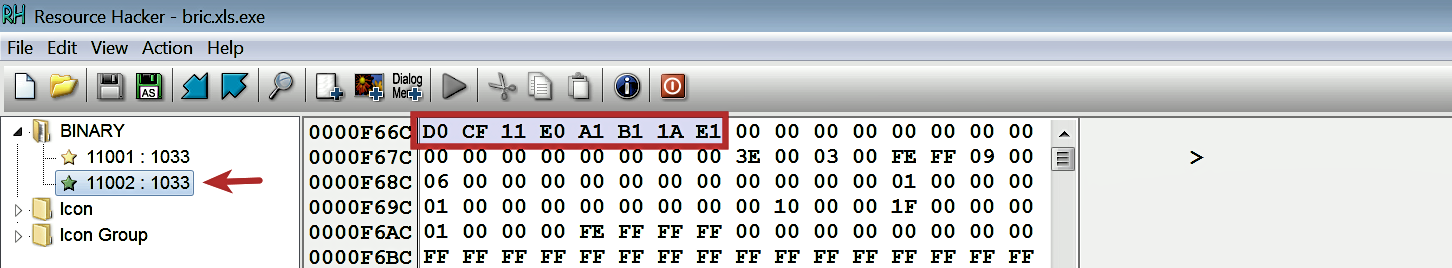
The executable also contains binary data; one of them has a file signature of D0 CF 11 E0 A1 B1 1A E1. This sequence of bytes represents the file signature for a Microsoft Office document file. The attackers, in this case, stored a decoy excel sheet in the resource section. Upon execution, the malware is executed in the background, and this decoy excel sheet is displayed to the user as a diversion:
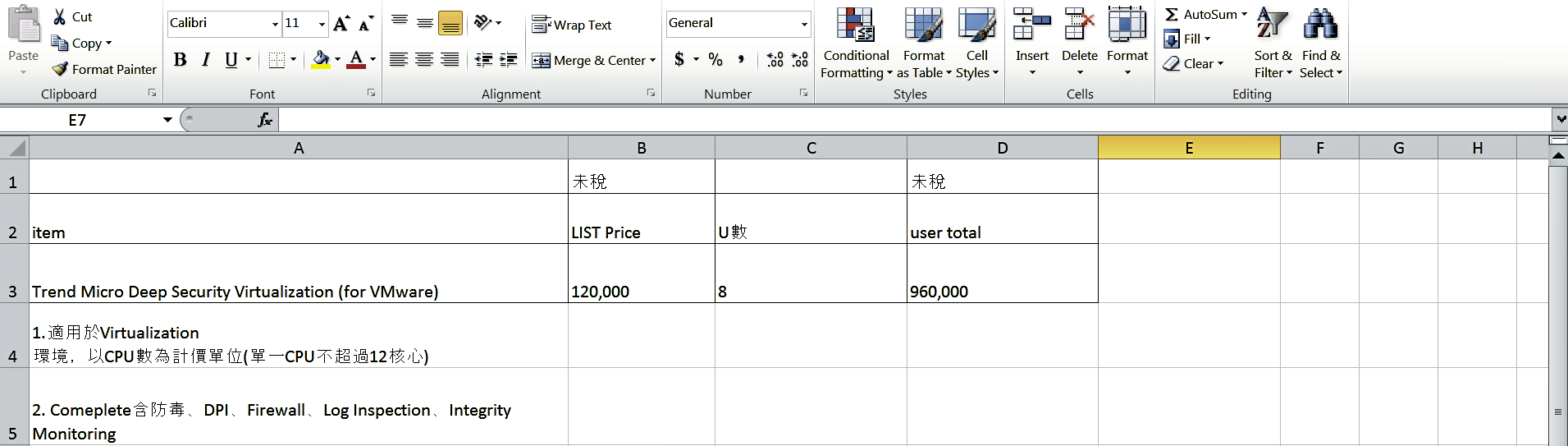
To save the binary to disk, right-click on the resource that you want to extract and click on Save Resource to a *.bin file as shown in the following screenshot. In this case, the resource was saved as sample.xls. The following screenshot shows the decoy excel sheet that will be displayed to the user:
Just by exploring the contents of the resource section, a lot can be learned about the malware characteristics.
