Component Object Model (COM) is a system that allows the software components to interact and communicate with each other, even if they have no knowledge of each other's code (https://msdn.microsoft.com/en-us/library/ms694363(v=vs.85).aspx). The software components interact with each other through the use of COM objects, and these objects can be within a single process, other processes, or on remote computers. COM is implemented as a client/server framework. A COM client is a program that uses the service from the COM server (COM object), and a COM server is an object which provides service to the COM clients. The COM server implements an interface consisting of various methods (functions), either in a DLL (called in-process server) or in an EXE (called out-of-process server). A COM client can utilize the service provided by COM server by creating an instance of the COM object, acquiring the pointer to the interface, and calling the method implemented in its interface.
The Windows operating system provides various COM objects that can be used by the programs (COM client). The COM objects are identified by a unique number called class identifiers (CLSIDs), and they are typically found in the registry key HKEY_CLASSES_ROOTCLSID< unique clsid>. For example, the COM object for My Computer is {20d04fe0-3aea-1069-a2d8-08002b30309d}, which can be seen in the following screenshot:

For each CLSID key, you also have a subkey called InProcServer32 that specifies the filename of the DLL that implements the COM server functionality. The following screenshot tells you that shell32.dll (COM server) is associated with My computer:

Similar to the My Computer COM object, Microsoft provides various other COM objects (implemented in DLLs) that are used by the legitimate programs. When the legitimate program (COM client) uses the service from a specific COM object (using its CLSID), its associated DLL gets loaded into the process address space of the client program. In the case of COM Hijacking, an attacker modifies the registry entry of a legitimate COM object and associates it with the attacker's malicious DLL. The idea is that when legitimate programs use the hijacked objects, the malicious DLL gets loaded into the address space of the legitimate program. This allows an adversary to persist on the system and execute malicious code.
In the following example, upon executing the malware (Trojan.Compfun), it drops a dll with a ._dl extension, as follows:
[CreateFile] ions.exe:2232 > %WinDir%systemapi-ms-win-downlevel-qgwo-l1-1-0._dl
The malware then sets the following registry value in HKCUSoftwareClassesCLSID. This entry associates the COM object {BCDE0395-E52F-467C-8E3D-C4579291692E} of the MMDeviceEnumerator class with the malicious DLL C:Windowssystemapi-ms-win-downlevel-qgwo-l1-1-0._dl for the current user:
[RegSetValue] ions.exe:2232 > HKCUSoftwareClassesCLSID{BCDE0395-E52F-467C-8E3D-C4579291692E}InprocServer32(Default) = C:Windowssystemapi-ms-win-downlevel-qgwo-l1-1-0._dl
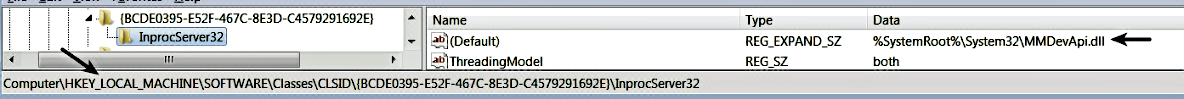
On a clean system, the COM object {BCDE0395-E52F-467C-8E3D-C4579291692E} of the MMDeviceEnumerator Class is associated with the DLL MMDevApi.dll, and its registry entry is typically found in HKEY_LOCAL_MACHINESOFTWAREClassesCLSID, and no corresponding entry is found in HKCUSoftwareClassesCLSID:
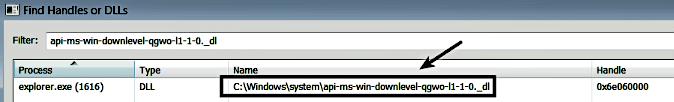
As a result of the malware adding an entry in HKCUSoftwareClassesCLSID{BCDE0395-E52F-467C-8E3D-C4579291692E}, the infected system now contains two registry entries for the same CLSID. Since the user objects from HKCUSoftwareClassesCLSID{BCDE0395-E52F-467C-8E3D-C4579291692E} get loaded before the machine objects located in HKLMSOFTWAREClassesCLSID{BCDE0395-E52F-467C-8E3D-C4579291692E}, the malicious DLL gets loaded, thereby hijacking the COM object of MMDeviceEnumerator. Now, any process that uses the MMDeviceEnumerator object loads the malicious DLL. The following screenshot was taken after restarting the infected system. After the restart, the malicious DLL was loaded by explorer.exe, as shown here:
The COM hijacking technique evades detection from most of the traditional tools. To detect this kind of attack, you can look for the presence of objects in HKCUSoftwareClassesCLSID. Instead of adding an entry in HKCUSoftwareClassesCLSID, malware may modify the existing entry in HKLMSoftwareClassesCLSID to point to a malicious binary, so you should also consider checking for any value pointing to an unknown binary in this registry key.
