Whenever a DLL is loaded, its entry point function gets called (which in turn calls its DLLMain function). An attacker can implement malicious functionality (such as keylogging, information stealing, and so on) in the DLLMain function without exporting any functions.
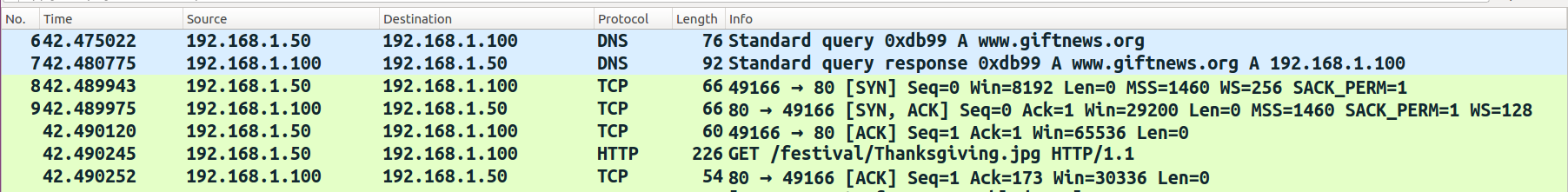
In the following example, the malicious DLL (aa.dll) does not contain any exports, which tells you that, all the malicious functionality may be implemented in its DLLmain function, which will be executed (called from the DLL entry point) when the DLL gets loaded. From the following screenshot, it can be seen that the malware imports functions from wininet.dll (which exports the function related to HTTP or FTP). This indicates that the malware probably calls these network functions within the DLLMain function, to interact with the C2 server using HTTP or FTP protocol:
You might assume that, because there is no export, a DLL can be executed using the following syntax:
C:>rundll32.exe C:samplesaa.dll
When you run a DLL with the preceding syntax, the DLL will not execute successfully; at the same time, you will not receive any error. The reason for this is that when rundll32.exe validates the command-line syntax (step 1 mentioned in the Section 6.2.1 Working of rundll32.exe), it fails the syntax check. As a result, rundll32.exe exits without loading the DLL.
You need to make sure that the command-line syntax is correct to load a DLL successfully. The command shown in the following output should run the DLL successfully. In the following command, test is a dummy name, and there is no such export function, it is just used to make sure the command-line syntax is correct. Before running the following command, the various monitoring tools that we covered in this chapter (Process Hacker, Noriben, Wireshark, Inetsim) were started:
C:>rundll32.exe C:samplesaa.dll,test
After running the command, the following error was received, but the DLL was successfully executed. In this case, because the syntax is correct, rundll32.exe loaded the DLL (step 2, mentioned in the Section 6.2.1 Working of rundll32.exe). As a result, its DLL entry point function was called (which in turn called DLLMain, containing the malicious code). Then rundll32.exe tries to find the address of the export function test (which is step 3, mentioned in the Section 6.2.1 Working of rundll32.exe). Since it cannot find the address of test, the following error was displayed. Even though the error message was displayed, the DLL was successfully loaded (that's exactly what we wanted for monitoring its activity):
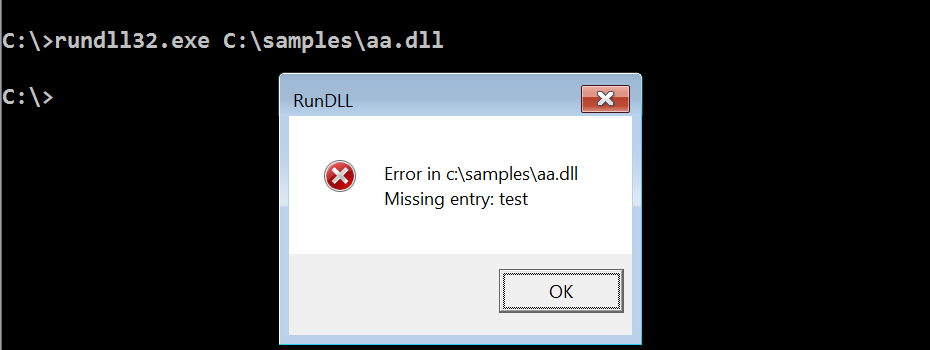
Upon execution, the malware establishes an HTTP connection with the C2 domain and downloads a file (Thanksgiving.jpg), as shown in the following Wireshark output: