A service is a program that runs in the background without any user interface, and it provides core operating system features such as event logging, printing, error reporting, and so on. An adversary with Administrator privilege can persist on the system by installing the malicious program as a service or by modifying an existing service. For an adversary, the advantage of using the service is that it can be set to start automatically when the operating system starts, and it mostly runs with a privileged account such as SYSTEM; this allows an attacker to elevate privileges. An attacker may implement the malicious program as an EXE, DLL, or kernel driver and run it as a service. Windows supports various service types, and the following outlines some of the common service types used by the malicious programs:
- Win32OwnProcess: The code for the service is implemented as an executable, and it runs as an individual process
- Win32ShareProcess: The code for the service is implemented as a DLL, and it runs from a shared host process (svchost.exe)
- Kernel Driver Service: This type of service is implemented in a driver (.sys), and it is used to execute the code in kernel space
Windows stores the list of installed services and their configuration in the registry under the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservices key. Each service has its own subkey consisting of values that specify how, when, and whether the service is implemented in an EXE, DLL, or kernel driver. For example, the service name for the Windows installer service is msiserver, and in the following screenshot, a subkey is present with the same name as the service name under HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservices. The ImagePath value specifies that the code for this service is implemented in msiexec.exe, the Type value of 0x10(16) tells us that it is Win32OwnProcess, and the Start value 0x3 represents SERVICE_DEMAND_START, which means that this service needs to be started manually:
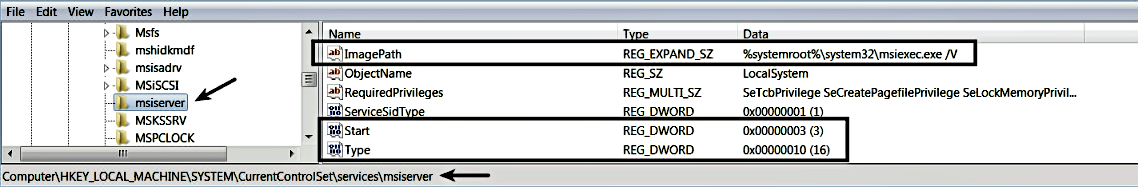
To determine the symbolic name associated with the constant values, you can refer to the MSDN documentation for the CreateService() API (https://msdn.microsoft.com/en-us/library/windows/desktop/ms682450(v=vs.85).aspx), or you can query the service configuration using the sc utility by providing the service name, as shown here. This will display similar information that is found in the registry subkey:
C:>sc qc "msiserver"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: msiserver
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:Windowssystem32msiexec.exe /V
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Windows Installer
DEPENDENCIES : rpcss
SERVICE_START_NAME : LocalSystem
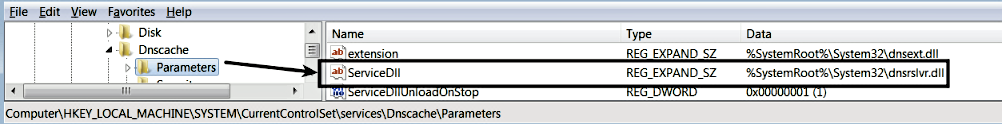
Let's now look at an example of the Win32ShareProcess service. The Dnsclient service has a service name of Dnscache, and code for the service is implemented in the DLL. When a service is implemented as a DLL (service DLL), the ImagePath registry value will typically contain the path to the svchost.exe (because that is the process that loads the Service DLL). To determine the DLL that is associated with the service, you will have to look at the ServiceDLL value, which is present under the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservices<service name>Parameters subkey. The following screenshot shows the DLL (dnsrslvr.dll) associated with the Dnsclient service; this DLL gets loaded by the generic host process svchost.exe:
An attacker can create services in many ways. The following outlines some of the common methods:
- sc utility: A malware can invoke cmd.exe and run an sc command such as sc create and sc start (or net start) to create and start the service, respectively. In the following example, malware executes the sc command (via cmd.exe) to create and start a service named update:
[CreateProcess] update.exe:3948 > "%WinDir%System32cmd.exe /c sc create update binPath= C:malwareupdate.exe start= auto && sc start update "
- Batch script: A malware can drop a batch script and execute the previously mentioned commands to create and start the service. In the following example, the malware (Trojan:Win32/Skeeyah) drops a batch script (SACI_W732.bat) and executes the batch script (via cmd.exe), which in turn creates and starts a service named Saci:
[CreateProcess] W732.exe:2836 > "%WinDir%system32cmd.exe /c %LocalAppData%Temp6DF8.tmpSACI_W732.bat "
[CreateProcess] cmd.exe:2832 > "sc create Saci binPath= %WinDir%System32Saci.exe type= own start= auto"
[CreateProcess] cmd.exe:2832 > "sc start Saci"
- Windows API: The malware can use Windows API, such as CreateService() and StartService() to create and start the service. When you run sc utility in the background, it uses these API calls to create and start the service. Consider the following example of the NetTraveler malware. Upon execution, it first drops a dll:
[CreateFile] d3a.exe:2904 > %WinDir%System32FastUserSwitchingCompatibilityex.dll
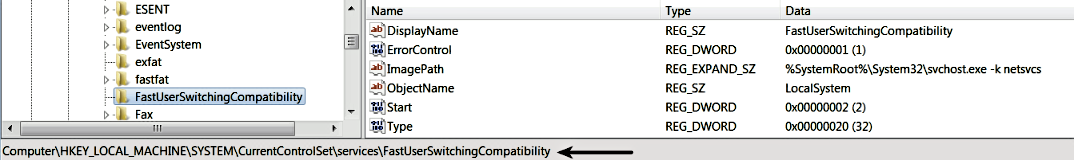
It then opens a handle to the service control manager using the OpenScManager() API and creates a service of type Win32ShareProcess by calling the CreateService() API. The second argument specifies the name of the service, which in this case is FastUserSwitchingCompatiblity:

After the call to CreateService(), the service gets created, and the following registry key is added with service configuration information:
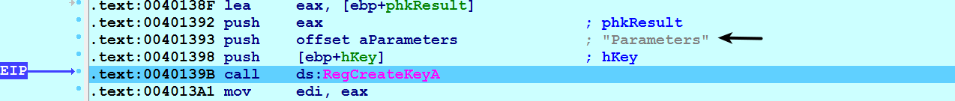
It then creates a Parameters subkey under the registry key created in the previous step:
After that, it drops and executes a batch script, which sets the registry value (ServiceDll) to associate the DLL with the created service. The content of the batch script is shown here:
@echo off
@reg add "HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesFastUserSwitchingCompatibilityParameters" /v ServiceDll /t REG_EXPAND_SZ /d C:Windowssystem32FastUserSwitchingCompatibilityex.dll
As a result of creating a Win32ShareProcess service, when the system boots, the service control manager (services.exe) starts the svchost.exe process, which in turn loads the malicious ServiceDLL FastUserSwitchingCompatibilityex.dll.
- PowerShell and WMI: A service can also be created using management tools such as PowerShell (https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/new-service?view=powershell-5.1) and Window Management Instrumentation (WMI) high-level interfaces (https://msdn.microsoft.com/en-us/library/aa394418(v=vs.85).aspx).
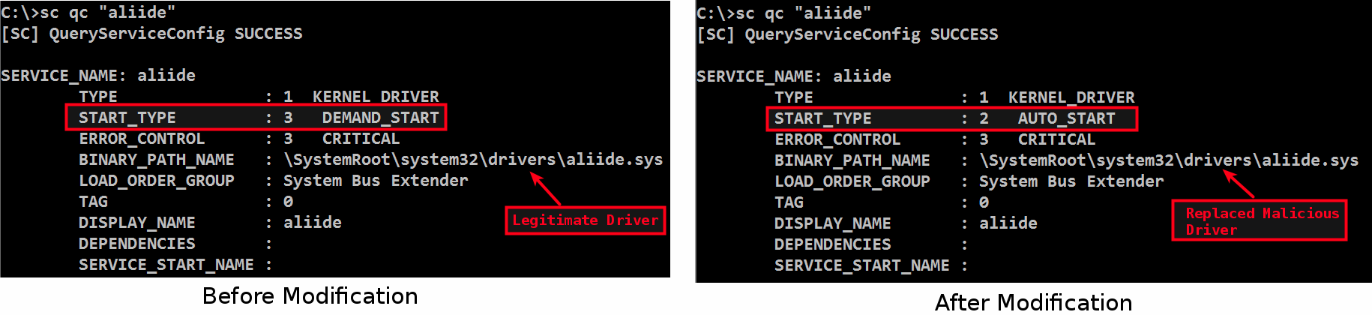
Instead of creating a new service, an adversary can modify (hijack) the existing service. Normally, an attacker hijacks a service that is unused or disabled. This makes detection slightly harder because, if you are trying to find the nonstandard or unrecognized service, you will miss this type of attack. Consider the example of the BlackEnergy malware dropper, which Hijacks the existing service to persist on the system. Upon execution, BlackEnergy replaces a legitimate driver called aliide.sys (associated with the service named aliide) residing in the system32drivers directory with the malicious aliide.sys driver. After replacing the driver, it modifies the registry entry associated with the aliide service and sets it to autostart (the service starts automatically when the system starts), as shown in the following events:
[CreateFile] big.exe:4004 > %WinDir%System32driversaliide.sys
[RegSetValue] services.exe:504 > HKLMSystemCurrentControlSetservicesaliideStart = 2
The following screenshot shows the service configuration of the aliide service before and after modification. For a detailed analysis of the BlackEnergy3 big dropper, read the author's blog post here at: https://cysinfo.com/blackout-memory-analysis-of-blackenergy-big-dropper/:
To detect such attacks, monitor the changes to service registry entries that are not associated with the legitimate program. Look for the modification to the binary path associated with the service, and changes to the service startup type (from manual to automatic). You should also consider monitoring and logging the usage of tools such as sc, PowerShell, and WMI, which can be used to interact with the service. The Sysinternals AutoRuns utility can also be used to inspect the use of service for persistence.
