The following steps describe how malware normally performs process hollowing. Let’s assume that there are two processes, A and B. In this case, process A is the malicious process and process B is the legitimate process (also known as a remote process) such as explorer.exe:
- Process A starts a legitimate process, B, in the suspended mode. As a result of that, the executable section of process B is loaded in the memory, and the PEB (Process Environment Block) identifies the full path to the legitimate process. The PEB structure's ImageBaseAddress field points to the base address where the legitimate process executable is loaded.
- Process A gets the malicious executable that will be injected into the remote process. This executable can come from the resource section of the malware process or from the file on the disk.
- Process A determines the base address of the legitimate process B so that it can unmap the executable section of the legitimate process. Malware can determine the base address by reading the PEB (in our case, PEB.ImageBaseAddress).
- Process A then deallocates the executable section of the legitimate process.
- Process A then allocates the memory in the legitimate process B with read, write, and execute permission. This memory allocation is normally done at the same address where the executable was previously loaded.
- Process A then writes the PE header and PE sections of the malicious executable to be injected into the allocated memory.
- Process A then changes the start address of the suspended thread to the address of the entry point of the injected executable and resumes the suspended thread of the legitimate process. As a result of that, the legitimate process now starts executing malicious code.
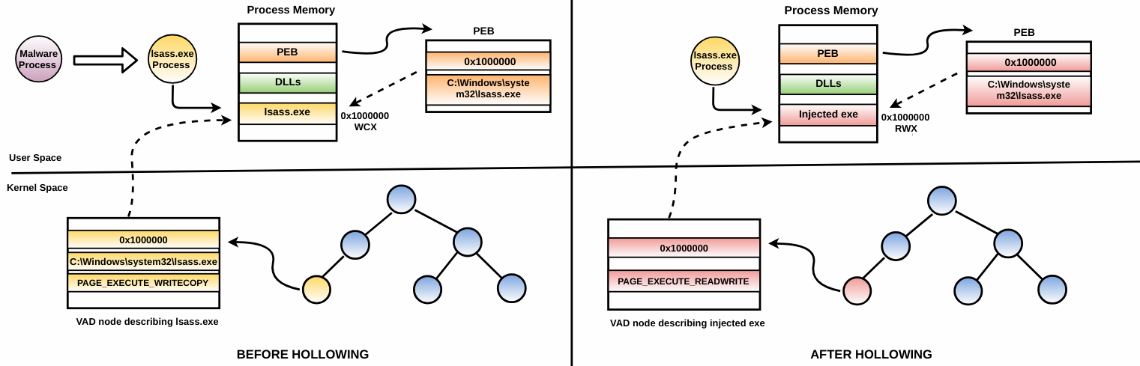
Stuxnet is one such malware that performs hollow process injection using the preceding steps. To be specific, Stuxnet creates the legitimate lsass.exe process in the suspended mode. As a result, lsass.exe is loaded into memory with PAGE_EXECUTE_WRITECOPY(WCX) protection. At this point (before hollowing), both PEB and VAD contain the same metadata information about lsass.exe's memory protection, base address, and the full path. Stuxnet then hollows out the legitimate process executable (lsass.exe) and allocates a new memory with PAGE_EXECUTE_READWRITE (RWX) protection in the same region where the lsass.exe was previously loaded, before injecting the malicious executable in the allocated memory and resuming the suspended thread. As a result of hollowing out the process executable, it creates a discrepancy in the process path information between the VAD and PEB, that is, the process path in PEB still contains the full path to lsass.exe, whereas VAD doesn't show the full path. Also, there is memory protection discrepancy before hollowing (WCX) and after hollowing (RWX). The following diagram should help you visualize what happens before hollowing, and the discrepancy it creates in PEB and VAD after hollowing the process: