This technique involves querying the state of each key on the keyboard. To do that, keyloggers make use of the GetAsyncKeyState() API function to determine whether the key is pressed or not. From the return value of GetAsyncKeyState(), it can be determined whether the key is up or down at the time the function is called and whether the key was pressed after a previous call to GetAsyncKeyState(). The following is the function prototype of the GetAsyncKeyState() API:
SHORT GetAsyncKeyState(int vKey);
GetAsynKeyState() accepts a single integer argument vKey which specifies one of 256 possible virtual-key codes. To determine the state of a single key on the keyboard, the GetAsyncKeyState() API can be called by passing the virtual-key code associated with the desired key as the argument. To determine the state of all the keys on the keyboard, a keylogger constantly polls the GetAsyncKeyState() API (by passing each virtual-key code as an argument) in a loop to determine which key is pressed.
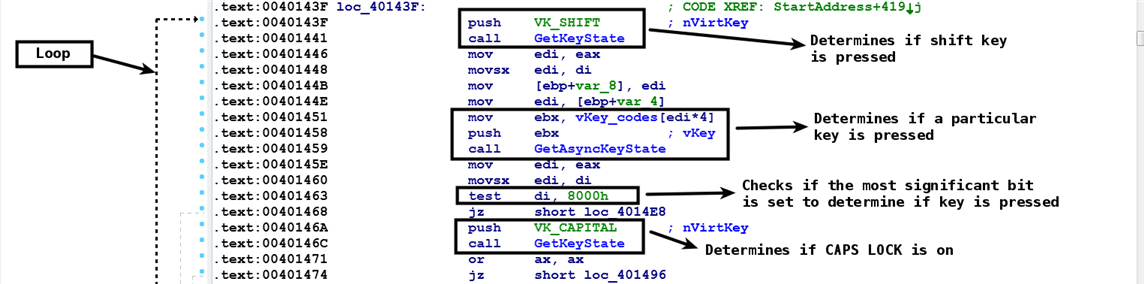
The following screenshot shows a code snippet from a keylogger. The keylogger determines the status of the Shift key (if it is up or down) by calling the GetKeyState() API at address 0x401441. At address 0x401459, the keylogger calls GetAsyncKeyState(), which is part of a loop, and in each iteration of the loop, the virtual-key code (which is read from the array of key codes) is passed as the argument to determine the status of each key. At address 0x401463, a test operation (the same as the AND operation) is performed on the return value of GetAsyncKeyState() to determine if the most significant bit is set. If the most significant bit is set, it is an indication of the key being pressed. If a particular key is pressed, then the keylogger calls GetKeyState() at address 0x40146c to check the status of the Caps Lock key (to check if it is turned on). Using this technique, malware can determine whether the upper case letter, lower case letter, number, or a special character was typed on the keyboard:
The following screenshot shows the end of the loop. From the code, you can tell that the malware iterates through the 0x5c (92) key codes. In other words, it monitors 92 keys. var_4, in this case, acts as an index into an array of key codes to check, and it is incremented at the end of the loop, and as long as the value of var_4 is less than 0x5c(92), the loop is continued:

