Even though Process Monitor is a great tool to monitor a malware's interaction with the system, it can be very noisy, and manual effort is required to filter the noise. Noriben (https://github.com/Rurik/Noriben) is a Python script that works in conjunction with Process Monitor and helps in collecting, analyzing, and reporting runtime indicators of the malware. The advantage of using Noriben is that it comes with pre-defined filters that assist in reducing noise and allow you to focus on the malware-related events.
To use Noriben, download it to your Windows VM, extract it to a folder, and copy Process Monitor (Procmon.exe) into the same folder before running the Noriben.py Python script, as shown in the following screenshot:

When you run Noriben, it launches Process Monitor. Once you are done with the monitoring, you can stop Noriben by pressing Ctrl + C, which will terminate Process Monitor. Once terminated, Noriben stores the results in a text file (.txt) and a CSV file (.csv) in the same directory. The text file contains events segregated based on the categories (like process, file, registry, and network activity) in separate sections, as shown in the following screenshot. Also, note that the number of events is much less because it applied predefined filters that reduced most of the unwanted noise:
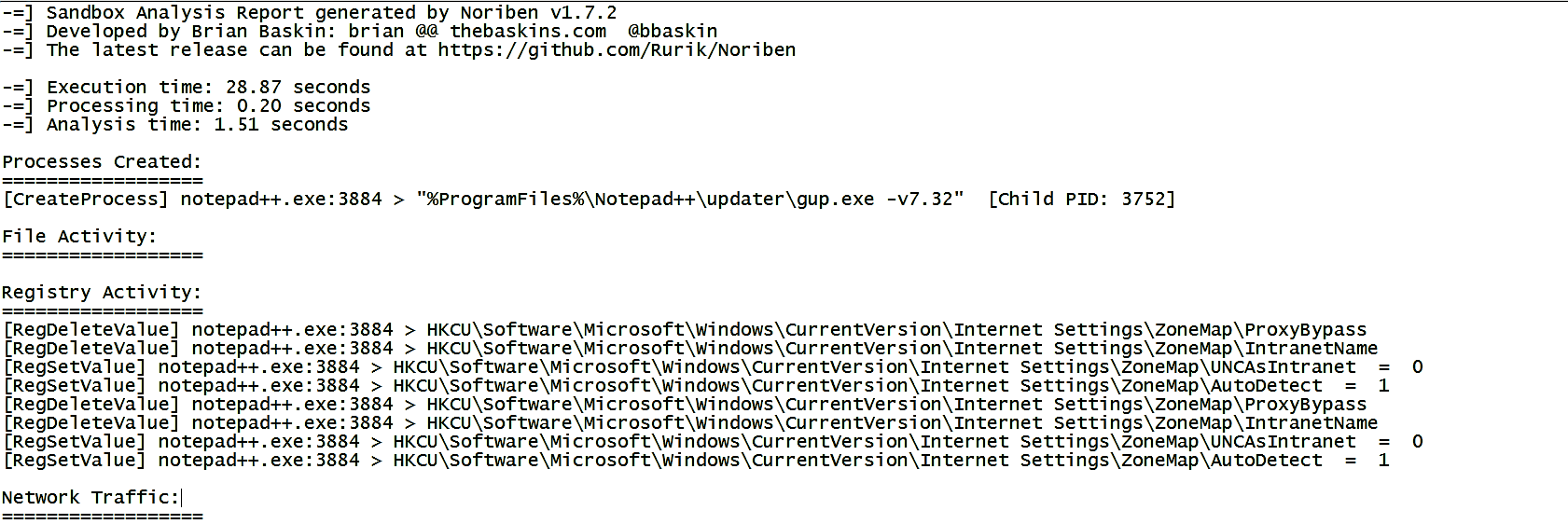
The CSV file contains all the events (process, file, registry, and network activity) sorted by the timeline (the order in which the events occurred), as shown in the following screenshot:

The text file and the CSV file can give different perspectives. If you are interested in the summary of events based on the category then you can look at the text file; if you are interested in the sequence of events in the order in which it occurred then you can view the CSV file.
