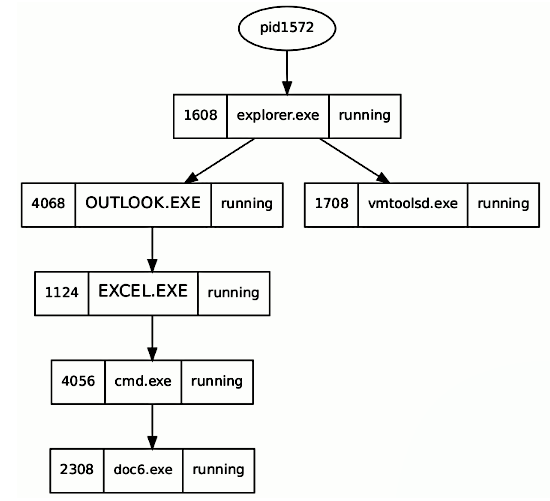
When examining processes, it can be useful to determine the parent/child relationships between the processes. During malware investigation, this will help you understand which other processes are related to the malicious process. The pstree plugin displays the parent-child process relationships by using the output from the pslist and formatting it in a tree view. In the following example, running the pstree plugin against an infected memory image displays a process relationship; a child process is indented to the right and prepended with periods. From the output, you can see that OUTLOOK.EXE was started by the explorer.exe process. This is normal because whenever you launch an application by double-clicking, it is the explorer that launches the application. OUTLOOK.EXE (pid 4068) launched EXCEL.EXE (pid 1124), which in turn invoked cmd.exe (pid 4056) to execute the malware process doc6.exe (pid 2308). By looking at the events, you can assume that the user opened a malicious Excel document sent via email, which probably exploited a vulnerability or executed a macro code to drop the malware and executed it via cmd.exe:
$ python vol.py -f infected.raw --profile=Win7SP1x86 pstree
Volatility Foundation Volatility Framework 2.6
Name Pid PPid Thds Hnds Time
------------------------ ---- ----- ---- ---- -------------------
[REMOVED]
0x86eb4780:explorer.exe 1608 1572 35 936 2016-05-11 12:15:10
. 0x86eef030:vmtoolsd.exe 1708 1608 5 160 2016-05-11 12:15:10
. 0x851ee2b8:OUTLOOK.EXE 4068 1608 17 1433 2018-04-15 02:14:23
.. 0x8580a3f0:EXCEL.EXE 1124 4068 11 377 2018-04-15 02:14:35
... 0x869d1030:cmd.exe 4056 1124 5 117 2018-04-15 02:14:41
.... 0x85b02d40:doc6.exe 2308 4056 1 50 2018-04-15 02:14:59
Since the pstree plugin relies on the pslist plugin, it cannot list the hidden or terminated processes. Another method to determine the process relationship is to use the psscan plugin to generate a visual representation of the parent/child relationships. The following psscan command prints the output in the dot format, which can then be opened with Graph Visualization Software such as Graphviz (https://www.graphviz.org/) or XDot (which can be installed on a Linux system using sudo apt install xdot):
$ python vol.py -f infected.vmem --profile=Win7SP1x86 psscan --output=dot --output-file=infected.dot
Opening the infected.dot file with XDot displays the relationship between the processes discussed previously: