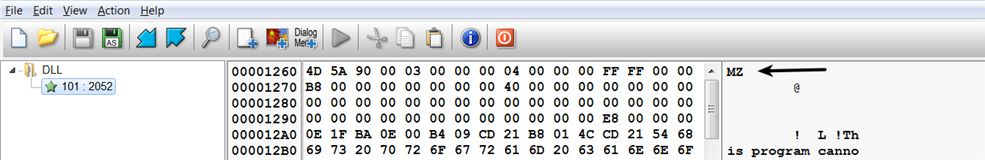
A Dropper is a program that embeds the additional malware component within itself. When executed, the dropper extracts the malware component and drops it to disk. A dropper normally embeds the additional binary in the resource section. To extract the embedded executable, a dropper uses the FindResource(), LoadResource(), LockResource() and SizeOfResource() API calls. In the following screenshot, the Resource Hacker tool (covered in Chapter 2, Static Analysis) shows the presence of a PE file in the resource section of a malware sample. In this case, the resource type is a DLL:
Loading the malicious binary in the x64dbg and looking at the references to the API calls (covered in the previous chapter) displays references to the resource-related API calls. This is an indication of malware extracting the content from the resource section. At this point, you can set a breakpoint on the address where the FindResourceA() API is called, as shown here:

In the following screenshot, after running the program, the execution is paused at the FindResourceA() API, due to the breakpoint set in the previous step. The second and third parameters passed to the FindResourceA() API tell you that the malware is trying to find the DLL/101 resource, as follows:

After executing FindResourceA(), its return value (stored in EAX), which is the handle to the specified resource's information block, is passed as the second argument to the LoadResource() API. The LoadResource() retrieves the handle to the data associated with the resource. The return value of LoadResource(), which contains the retrieved handle, is then passed as the argument to the LockResource() API, which obtains the pointer to the actual resource. In the following screenshot, the execution is paused immediately after the call to LockResource(). Examining the return value (stored in EAX) in the dump window shows the PE executable content that was retrieved from the resource section:
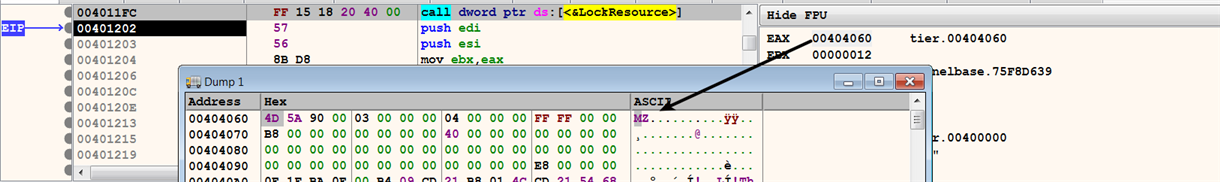
Once it retrieves the resource, the malware determines the size of the resource (PE file) using the SizofResource() API. Next, the malware drops a DLL on the disk using CreateFileA, as follows:

The extracted PE content is then written to the DLL using the WriteFile() API. In the following screenshot, the first argument 0x5c is the handle to the DLL, the second argument 0x00404060 is the address of the retrieved resource (PE File), and the third argument 0x1c00 is the size of the resource, which was determined using the call to SizeOfResource():

