In this technique, the malicious code is injected into the target process memory directly, without dropping the component on the disk. The malicious code can be a shellcode or an executable whose import address table is configured for the target process. The injected malicious code is forced to execute by creating a remote thread via CreateRemoteThread(), and the start of the thread is made to point to the code/function within the injected block of code. The advantage of this method is that the malware process does not have to drop the malicious DLL on the disk; it can extract the code to inject from the resource section of the binary, or get it over the network and perform code injection directly.
The following steps describe how this technique is performed, with an example of a malware sample named nsasr.exe (W32/Fujack), which injects the executable into the Internet Explorer (iexplorer.exe) process:
- The malware process (nsasr.exe) opens a handle to the Internet Explorer process (iexplore.exe) using the OpenProcess() API.
- It allocates memory in the target process (iexplore.exe) at a specific address, 0x13150000, using VirutualAllocEx() with PAGE_EXECUTE_READWRITE protection, instead of PAGE_READWRITE (as compared to the remote DLL injection technique, covered in section 3.1). The protection PAGE_EXECUTE_READWRITE allows the malware process (nsasr.exe) to write the code into the target process, and, after writing the code, this protection allows the target process (iexplore.exe) to read and execute code from this memory.
- It then writes the malicious executable content into the memory allocated in the previous step using WriteProcessMemory(). In the following screenshot, the 1st argument, 0xD4, is the handle to iexplore.exe. The 2nd argument, 0x13150000, is the address in the target process (iexplore.exe) memory, where the content will be written to. The 3rd argument, 0x13150000, is the buffer in the malware (nsasr.exe) process memory; this buffer contains the executable content, which will be written to the target process memory:
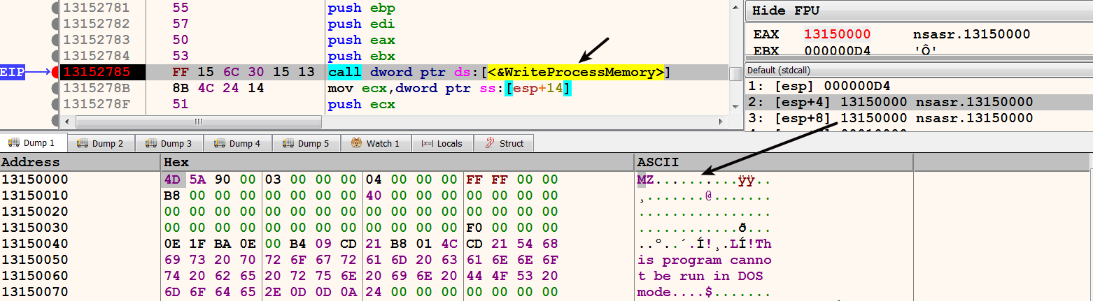
- After the malicious executable content is written (at the address 0x13150000) in the iexplore.exe process memory, it calls the CreateRemoteThread() API to create a remote thread, and the start address of the thread is made to point to the address of entrypoint of the injected executable. In the following screenshot, the 4th argument, 0x13152500, specifies the address in the target process (iexplore.exe) memory where the thread will start executing; this is the entry point address of the injected executable. At this point, the injection is complete, and the thread in the iexplore.exe process starts executing malicious code:

