In the following example, we will look at a malware named Skeeyah, which performs hollow process injection in a slightly different way. This is the same sample which was covered in Chapter 8, Code Injection and Hooking (section 3.6 Hollow Process Injection). The following are the steps performed by Skeeyah:
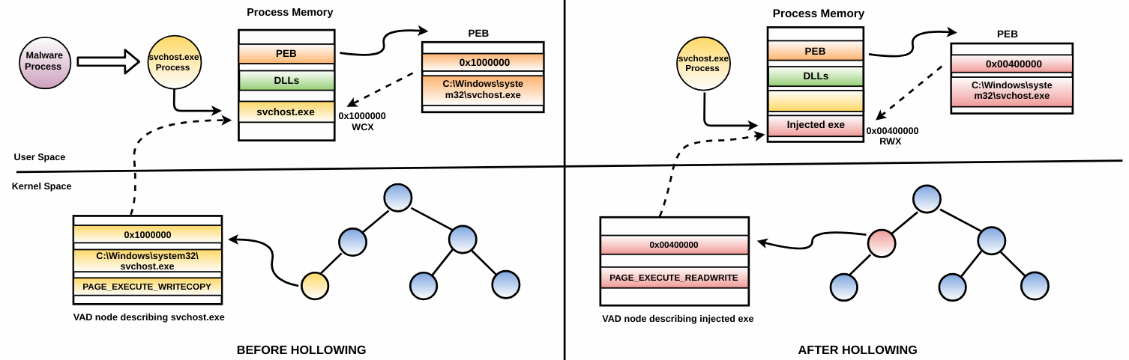
- It starts the svchost.exe process in the suspended mode. As a result, svchost.exe is loaded into the memory (in this case, at address 0x1000000).
- It determines the base address of svchost.exe by reading PEB.ImageBaseAddress and then deallocates the executable section of svchost.exe.
- Instead of allocating memory in the same region where the svchost.exe was previously loaded (0x1000000), it allocates memory in a different address, 0x00400000, with read, write, and execute permission.
- It then overwrites the PEB.ImageBaseAdress of the svchost.exe process with the newly allocated address, 0x00400000. This changes the base address of svchost.exe in the PEB from 0x1000000 to 0x00400000 (which contains injected executables).
- It then changes the start address of the suspended thread to the address of the entry point of the injected executable and resumes the thread.
The following screenshot shows the discrepancy before and after hollowing. To be specific, the PEB after hollowing thinks that svchost.exe is loaded at 0x00400000. The VAD node that previously represented svchost.exe (loaded at 0x1000000) is no longer present, because when the malware hollowed out the svchost.exe process executable, the entry for that was removed from the VAD tree:
To detect this variation of hollow process injection, you can follow the same methodology. Depending on how the hollow process injection is performed, the results will vary. The process listing shows multiple instances of the svchost.exe process, which is normal. All the svchost.exe processes except the last svchost.exe (pid 1824) have a parent process of services.exe (pid 696). On a clean system, all the svchost.exe process are started by services.exe. When you look at the parent process of svchost.exe (pid 1824) you can see that its parent process is terminated. Based on the process information, you can tell that the last svchost.exe (pid 1824) is suspicious:
$ python vol.py -f skeeyah.vmem --profile=WinXPSP3x86 pslist | grep -i svchost
Volatility Foundation Volatility Framework 2.6
0x815cfaa0 svchost.exe 876 696 20 202 0 0 2016-05-10 06:47:25
0x818c5a78 svchost.exe 960 696 9 227 0 0 2016-05-10 06:47:25
0x8181e558 svchost.exe 1044 696 68 1227 0 0 2016-05-10 06:47:25
0x818c7230 svchost.exe 1104 696 5 59 0 0 2016-05-10 06:47:25
0x81743da0 svchost.exe 1144 696 15 210 0 0 2016-05-10 06:47:25
0x817ba390 svchost.exe 1824 1768 1 26 0 0 2016-05-12 14:43:43
$ python vol.py -f skeeyah.vmem --profile=WinXPSP3x86 pslist -p 696
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start
---------- ------------ --- ---- ---- ---- ---- ------ --------------------
0x8186c980 services.exe 696 652 16 264 0 0 2016-05-10 06:47:24
$ python vol.py -f skeeyah.vmem --profile=WinXPSP3x86 pslist -p 1768
Volatility Foundation Volatility Framework 2.6
ERROR : volatility.debug : Cannot find PID 1768. If its terminated or unlinked, use psscan and then supply --offset=OFFSET
The dlllist plugin (which relies on PEB) shows the full path to svchost.exe (pid 1824) and reports the base address as 0x00400000.
$ python vol.py -f skeeyah.vmem --profile=WinXPSP3x86 dlllist -p 1824
Volatility Foundation Volatility Framework 2.6
************************************************************************
svchost.exe pid: 1824
Command line : "C:WINDOWSsystem32svchost.exe"
Service Pack 3
Base Size LoadCount Path
---------- ------- ---------- ----------------------------------
0x00400000 0x7000 0xffff C:WINDOWSsystem32svchost.exe
0x7c900000 0xaf000 0xffff C:WINDOWSsystem32 tdll.dll
0x7c800000 0xf6000 0xffff C:WINDOWSsystem32kernel32.dll
[REMOVED]
On the other hand, the ldrmodules plugin (which relies on VAD in the kernel) does not show any entry for svchost.exe, as shown in the following screenshot:

malfind shows the presence of a PE file at address 0x00400000 with a suspicious memory protection of PAGE_EXECUTE_READWRITE, indicating that this executable was injected and not normally loaded:
$ python vol.py -f skeeyah.vmem --profile=WinXPSP3x86 malfind -p 1824
Volatility Foundation Volatility Framework 2.6
Process: svchost.exe Pid: 1824 Address: 0x400000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 7, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00400000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x00400010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x00400020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00400030 00 00 00 00 00 00 00 00 00 00 00 00 e0 00 00 00 ................
0x00400000 4d DEC EBP
0x00400001 5a POP EDX
[REMOVED]
