The PE header contains information that specifies when the binary was compiled; examining this field can give an idea of when the malware was first created. This information can be useful in building a timeline of the attack campaign. It is also possible that an attacker modifies the timestamp to prevent an analyst from knowing the actual timestamp. A compile timestamp can sometimes be used to classify suspicious samples. The following example shows a malware binary whose timestamp was modified to a future date in 2020. In this case, even though the actual compilation timestamp could not be detected, such characteristics can help you identify anomalous behavior:
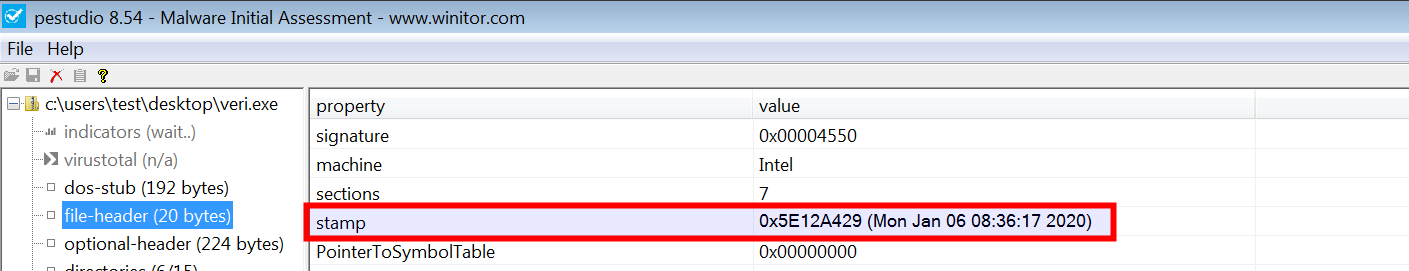
In Python, you can determine the compile timestamp using the following Python commands:
>>> import pefile
>>> import time
>>> pe = pefile.PE("veri.exe")
>>> timestamp = pe.FILE_HEADER.TimeDateStamp
>>> print time.strftime("%Y-%m-%d %H:%M:%S",time.localtime(timestamp))
2020-01-06 08:36:17
