There are various tools that allow you to unpack the malware packed with common packers such as UPX, FSG, and AsPack. Automated tools are great for known packers and can save time, but remember, it may not always work; that is when the manual unpacking skills will help. TitanMist by ReversingLabs (https://www.reversinglabs.com/open-source/titanmist.html) is a great tool that consists of various packer signatures and unpacking scripts. After you download and extract it, you can run it against the packed binary using the command shown here; using -i, you specify the input file (packed file), and -o specifies the output filename, and -t specifies the type of unpacker. In the later-mentioned command, TitanMist was run against the binary packed with UPX; note how it automatically identified the packer and performed the unpacking process. The tool automatically identified the OEP and import table, dumped the process, fixed the imports, and applied the patch to the dumped process:
C:TitanMist>TitanMist.exe -i packed.exe -o unpacked.exe -t python
Match found!
│ Name: UPX
│ Version: 0.8x - 3.x
│ Author: Markus and Laszlo
│ Wiki url: http://kbase.reversinglabs.com/index.php/UPX
│ Description:
Unpacker for UPX 1.x - 3.x packed files
ReversingLabs Corporation / www.reversinglabs.com
[x] Debugger initialized.
[x] Hardware breakpoint set.
[x] Import at 00407000.
[x] Import at 00407004.
[x] Import at 00407008.[Removed]
[x] Import at 00407118.
[x] OEP found: 0x0040259B.
[x] Process dumped.
[x] IAT begin at 0x00407000, size 00000118.
[X] Imports fixed.
[x] No overlay found.
[x] File has been realigned.
[x] File has been unpacked to unpacked.exe.
[x] Exit Code: 0.
█ Unpacking succeeded!
Another option is to use the IDA Pro's Universal PE Unpacker plugin. This plugin relies on debugging the malware, to determine when the code jumps to the OEP. For detailed information on this plugin, refer to this article (https://www.hex-rays.com/products/ida/support/tutorials/unpack_pe/unpacking.pdf). To invoke this plugin, load the binary into IDA and select Edit | Plugins | Universal PE unpacker. Running the plugin launches the program in the debugger, and it tries to suspend it, as soon as the packer finishes unpacking. After loading the UPX-packed malware (the same sample used in manual unpacking) in IDA and launching the plugin, the following dialog is displayed. In the following screenshot, IDA set the start address and end address to the range of the UPX0 section; this range is treated as the OEP range. In other words, when the execution reaches this section (from UPX1, which contains decompression stub), IDA will suspend the program execution, giving you a chance to take further action:

In the following screenshot, note how IDA automatically determined the OEP address and then showed the following dialog:

If you click on the Yes button, the execution is stopped, and the process is exited but before that, IDA automatically determines the import address table (IAT) and it creates a new segment to rebuild the import section of the program. At this point, you can analyze the unpacked code. The following screenshot shows the newly rebuilt import address table:
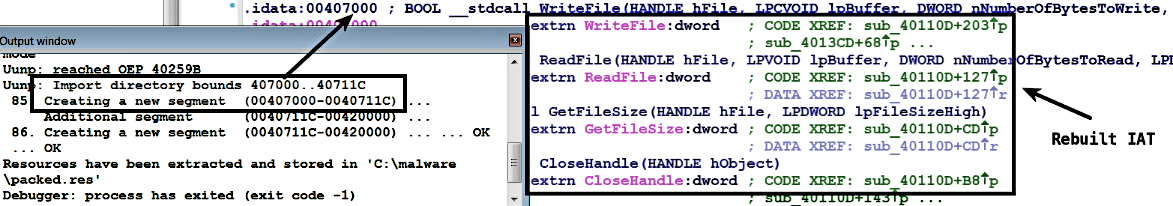
Instead of clicking the YES button, if you click on the No button, then IDA will pause the debugger execution at the OEP, and At this point, you can either debug the unpacked code or manually dump the executable, fix the imports using a tool such as Scylla by entering the proper OEP (as covered in Section 4.1 manual unpacking).
In x64dbg, you can perform automated unpacking using unpacking scripts, which can be downloaded from https://github.com/x64dbg/Scripts. To unpack, make sure that the binary is loaded and paused at the entry point. Depending on the packer you are dealing with, you need to load the appropriate unpacker script by right-clicking on the script pane and then by selecting Load Script | Open (or Ctrl + O). The following screenshot shows the contents of the UPX unpacker script:

After loading the script, run the script by right-clicking on the script pane and by selecting Run. If the script successfully unpacks it, a message box pops up saying Script Finished and the execution will be paused at the OEP. The following screenshot shows the breakpoint (In the CPU pane) automatically set at the OEP as a result of running the UPX unpacker script. Now, you can start debugging the unpacked code or you can use Scylla to dump the process and fix the imports (as described in section 4.1 manual unpacking):

