In this technique, the target (remote) process is forced to load a malicious DLL into its process memory space via the LoadLibrary() API. The kernel32.dll exports LoadLibrary(), and this function takes a single argument, which is the path to the DLL on the disk, and loads that DLL into the address space of the calling process. In this injection technique, the malware process creates a thread in the target process, and the thread is made to call LoadLibrary() by passing a malicious DLL path as the argument. Since the thread gets created in the target process, the target process loads the malicious DLL into its address space. Once the target process loads the malicious DLL, the operating system automatically calls the DLL's DllMain() function, thus executing the malicious code.
The following steps describe in detail how this technique is performed, with an example of a malware named nps.exe (loader or launcher) that injects a DLL via LoadLibrary() into the legitimate explorer.exe process. Before injecting the malicious DLL component, it is dropped onto the disk, and then the following steps are performed:
- The malware process (nps.exe) identifies the target process (explorer.exe, in this case) and gets its process ID (pid). The idea of getting the pid is to open a handle to the target process so that the malware process can interact with it. To open a handle, the OpenProcess() API is used, and one of the parameters it accepts is the pid of the process. In the following screenshot, the malware calls OpenProcess() by passing the pid of explorer.exe (0x624, which is 1572) as the third parameter. The return value of OpenProcess() is the handle to the explorer.exe process:

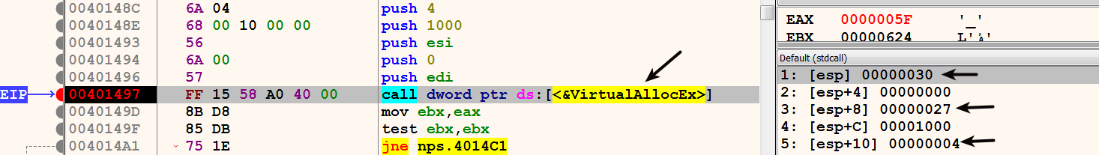
- The malware process then allocates memory in the target process using the VirutualAllocEx() API. In the following screenshot, the 1st argument (0x30) is the handle to explorer.exe (the target process), which it acquired from the previous step. The 3rd argument, 0x27 (39), represents the number of bytes to be allocated in the target process, and the 5th argument (0x4) is a constant value that represents the memory protection of PAGE_READWRITE. The return value of VirtualAllocEx() is the address of the allocated memory in explorer.exe:
- The reason for allocating the memory in the target process is to copy a string that identifies the full path of the malicious DLL on the disk. The malware uses WriteProcessMemory() to copy the DLL pathname to the allocated memory in the target process. In the following screenshot, the 2nd argument, 0x01E30000, is the address of the allocated memory in the target process, and the 3rd argument is the full path to the DLL that will be written to the allocated memory address 0x01E30000 in explorer.exe:

- The idea of copying the DLL pathname to the target process memory is that, later, when the remote thread is created in the target process and when LoadLibrary() is called via a remote thread, the DLL path will be passed as the argument to LoadLibrary(). Before creating a remote thread, malware must determine the address of LoadLibrary() in kernel32.dll; to do that, it calls the GetModuleHandleA() API and passes kernel32.dll as the argument, which will return the base address of Kernel32.dll. Once it gets the base address of kernel32.dll, it determines the address of LoadLibrary() by calling GetProcessAddress().
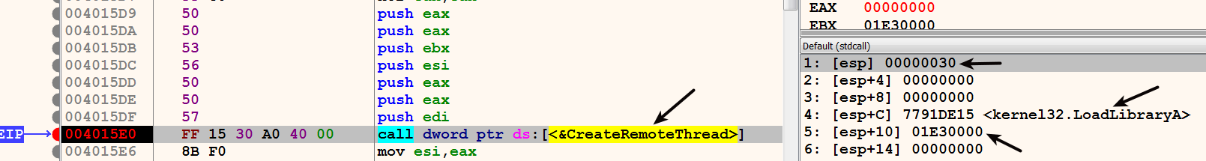
- At this point, the malware has copied the DLL pathname in the target process memory, and it has determined the address of LoadLibrary(). Now, the malware needs to create a thread in the target process (explorer.exe), and this thread must be made to execute LoadLibrary() by passing the copied DLL pathname so that the malicious DLL will be loaded by explorer.exe. To do that, the malware calls CreateRemoteThread() (or the undocumented API NtCreateThreadEx()), which creates a thread in the target process. In the following screenshot, the 1st argument, 0x30, to CreateRemoteThread() is the handle to the explorer.exe process, in which the thread will be created. The 4th argument is the address in the target process memory where the thread will start executing, which is the address of LoadLibrary(), and the 5th argument is the address in the target process memory that contains the full path to the DLL. After calling CreateRemoteThread(), the thread created in explorer.exe invokes LoadLibrary(), which will load the DLL from the disk into the explorer.exe process memory space. As a result of loading the malicious DLL, its DLLMain() function gets called automatically, thereby executing malicious code within the context of explorer.exe:
- Once the injection is complete, the malware calls the VirtualFree() API to free the memory containing the DLL path and closes the handle to the target process (explorer.exe) by using the CloseHandle() API.
