Most malware, when executed, reach out to the internet (command and control server), and it is not a good idea to allow the malware to connect to its C2 server, and also sometimes these servers may be unavailable. During malware analysis, you need to determine the behavior of the malware without allowing it to contact the actual command and control (C2) server, but at the same time, you need to provide all the services required by the malware so that it can continue its operation.
INetSim is a free Linux-based software suite for simulating standard internet services (such as DNS, HTTP/HTTPS, and so on). The steps to install and configure INetSim on the Linux VM were covered in Chapter 1, Introduction to Malware Analysis. Once INetSim is launched, it simulates various services, as shown in the following output, and it also runs a dummy service that handles connections directed at nonstandard ports:
$ sudo inetsim
INetSim 1.2.6 (2016-08-29) by Matthias Eckert & Thomas Hungenberg
Using log directory: /var/log/inetsim/
Using data directory: /var/lib/inetsim/
Using report directory: /var/log/inetsim/report/
Using configuration file: /etc/inetsim/inetsim.conf
Parsing configuration file.
Configuration file parsed successfully.
=== INetSim main process started (PID 2758) ===
Session ID: 2758
Listening on: 192.168.1.100
Real Date/Time: 2017-07-09 20:56:44
Fake Date/Time: 2017-07-09 20:56:44 (Delta: 0 seconds)
Forking services...
* irc_6667_tcp - started (PID 2770)
* dns_53_tcp_udp - started (PID 2760)
* time_37_udp - started (PID 2776)
* time_37_tcp - started (PID 2775)
* dummy_1_udp - started (PID 2788)
* smtps_465_tcp - started (PID 2764)
* dummy_1_tcp - started (PID 2787)
* pop3s_995_tcp - started (PID 2766)
* ftp_21_tcp - started (PID 2767)
* smtp_25_tcp - started (PID 2763)
* ftps_990_tcp - started (PID 2768)
* pop3_110_tcp - started (PID 2765)
[...............REMOVED.
..............]
* http_80_tcp - started (PID 2761)
* https_443_tcp - started (PID 2762)
done.
Simulation running.
Apart from simulating services, INetSim can log communications, and it can also be configured to respond to HTTP/HTTPS requests and return any files based on the extensions. For example, if malware requests an executable (.exe) file from the C2 server, INetSim can return a dummy executable file to the malware. That way, you get to know what malware does with the executable file after downloading it from the C2 server.
The following example demonstrates the use of INetSim. In this example, a malware sample was executed on the Windows VM, and the network traffic was captured using Wireshark on the Linux VM without invoking INetSim. The following screenshot displays the traffic captured by Wireshark. It shows that the infected Windows system (192.168.1.50) is trying to communicate with the C2 server by first resolving the C2 domain, but because our Linux VM does not have a DNS server running, that domain could not be resolved (as indicated by the Port Unreachable message):

This time, the malware was executed, and the network traffic was captured on the Linux VM with INetSim running (simulating services). From the following screenshot, it can be seen that the malware first resolves the C2 domain, which is resolved to the Linux VM's IP address of 192.168.1.100. Once resolved, it then makes an HTTP communication to download a file (settings.ini):
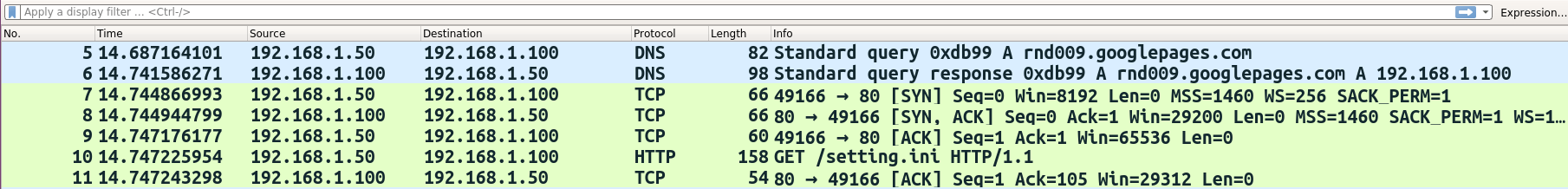
From the following screenshot, it can be seen that the HTTP response was given by the HTTP server simulated by INetSim. In this case, the User-Agent field in the HTTP request suggests that the standard browser did not initiate the communication and such an indicator can be used to create network signatures:

By simulating the services, it was possible to determine that the malware downloads a file from the C2 server after execution. A tool such as INetSim allows a security analyst to quickly determine the malware's behavior and capture its network traffic without having to manually configure all the services (such as DNS, HTTP and so on).
