The following example shows how you can analyze a DLL that accepts export arguments. The DLL used in this example was delivered via powerpoint, as described in this link: https://securingtomorrow.mcafee.com/mcafee-labs/threat-actors-use-encrypted-office-binary-format-evade-detection/.
The DLL (SearchCache.dll) consists of an export function, _flushfile@16, whose functionality is to delete a file. This export function accepts an argument, which is the file to delete:
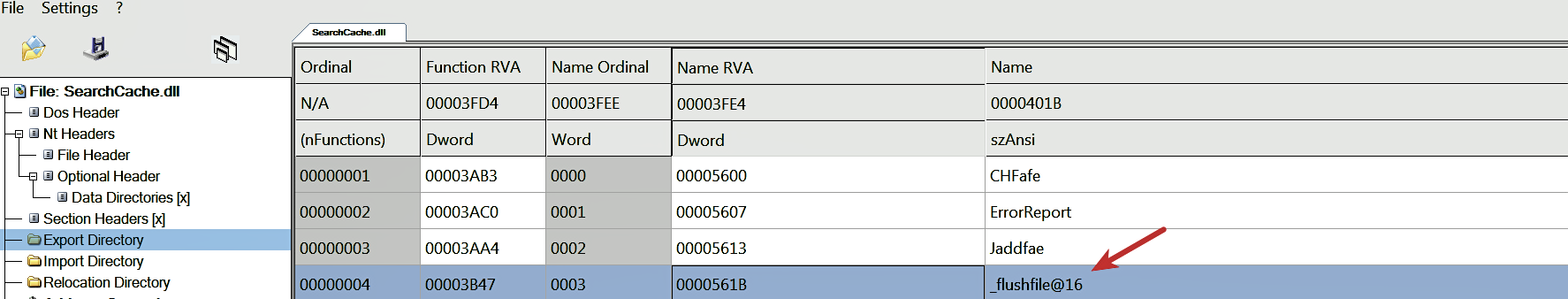
To demonstrate the delete functionality, a test file (file_to_delete.txt) was created, and the monitoring tools were launched. The test file was passed an argument to the export function _flushfile@16 using the following command. After running the following command, the test file was deleted from the disk:
rundll32.exe c:samplesSearchCache.dll,_flushfile@16 C:samplesfile_to_delete.txt
The following is the output from the Noriben logs showing rundll32.exe deleting the file (file_to_delete.txt):
Processes Created:
[CreateProcess] cmd.exe:1100 > "rundll32.exe c:samplesSearchCache.dll,_flushfile@16 C:samplesfile_to_delete.txt" [Child PID: 3348]
File Activity:
[DeleteFile] rundll32.exe:3348 > C:samplesfile_to_delete.txt
