In this section, you will understand how adversaries use HTTP to communicate with the malicious program. The following is an example of a malware sample (WEBC2-DIV backdoor) used by the APT1 group (https://www.fireeye.com/content/dam/fireeye-www/services/pdfs/mandiant-apt1-report.pdf). The malicious binary makes use of the InternetOpen(), InternetOpenUrl(), and InternetReadFile() API functions to retrieve a web page from an attacker-controlled C2 server. It expects the web page to contain special HTML tags; the backdoor then decrypts the data within the tags and interprets it as a command. The following steps describe the manner in which the WEB2-DIV backdoor communicates with the C2 to receive commands:
- First, the malware calls the InternetOpenA() API to initialize the connection to the internet. The first argument specifies the User-Agent the malware will use for the HTTP communication. This backdoor generates the User-Agent by concatenating the host-name of the infected systems (which it gets by calling the GetComputerName() API) with a hardcoded string. Whenever you come across a hardcoded User-Agent string used in the binary, it can make an excellent network indicator:
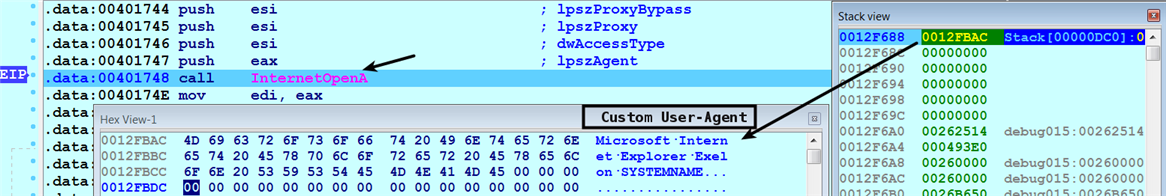
- It then calls InternetOpenUrlA() to connect to a URL. You can determine the name of URL it connects to by examining the second argument as follows:

- The following screenshot shows the network traffic generated after calling InternetOpenUrlA(). At this stage, the malware communicates with the C2 server to read the HTML content:

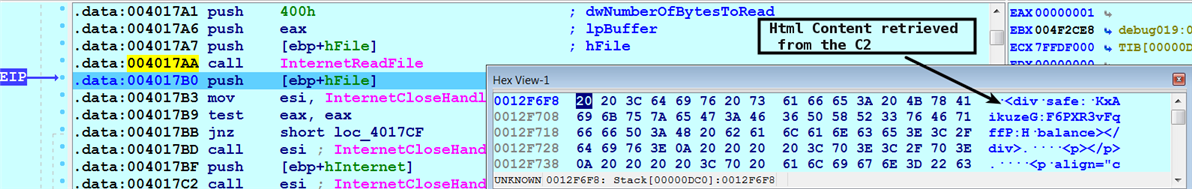
- It then retrieves the content of the web page using the InternetReadFile() API call. The second argument to this function specifies the pointer to the buffer that receives the data. The following screenshot shows the HTML content retrieved after calling InternetReadFile():
- From the retrieved HTML content, the backdoor looks for specific content within the <div> HTML tag . The code performing the check for the content within a div tag is shown in the following screenshot. If the required content is not present, the malware does nothing and keeps periodically checking for the content:
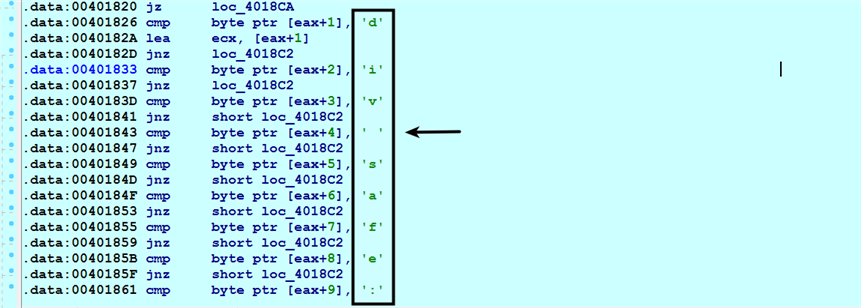
To be specific, the malware expects the content to be enclosed within the div tag in a specific format such as the one shown in the following code. If the following format is found in the retrieved HTML content, its extracts the encrypted string (KxAikuzeG:F6PXR3vFqffP:H), which is enclosed between <div safe: and balance></div>:
<div safe: KxAikuzeG:F6PXR3vFqffP:H balance></div>
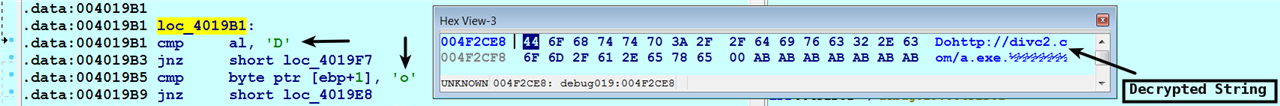
- The extracted encrypted string is then passed as the argument to a decryption function, which decrypts the string using a custom encryption algorithm. You will learn more about malware encryption techniques in Chapter 9, Malware Obfuscation Techniques. The following screenshot shows the decrypted string after calling decryption function. After decrypting the string, the backdoor checks if the first character of the decrypted string is J. If this condition is satisfied, then the malware calls the sleep() API to sleep for a specific period. In short, the first character of the decrypted string acts as a command code, which tells the backdoor to perform the sleep operation:

- If the first character of the decrypted string is D, then it checks if the second character is o, as shown here. If this condition is satisfied, then it extracts the URL starting from the third character and downloads an executable from that URL using UrlDownloadToFile(). It then executes the downloaded file using the CreateProcess() API. In this case, the first two characters, Do, act as the command code that tells the backdoor to download and execute the file:
Malware may also use APIs such as InternetOpen(), InternetConnect(), HttpOpenRequest(), HttpSendRequest(), and InternetReadFile() to communicate over HTTP. You can find analysis and reverse engineering of one such malware here: https://cysinfo.com/sx-2nd-meetup-reversing-and-decrypting-the-communications-of-apt-malware/.
In addition to using HTTP/HTTPS, adversaries may abuse social networks (https://threatpost.com/attackers-moving-social-networks-command-and-control-071910/74225/), legitimate sites such as Pastebin (https://cysinfo.com/uri-terror-attack-spear-phishing-emails-targeting-indian-embassies-and-indian-mea/), and cloud storage services such as Dropbox (https://www.fireeye.com/blog/threat-research/2015/11/china-based-threat.html) for their malware command and control. These techniques make it difficult to monitor and detect malicious communications, and they allow an attacker to bypass network-based security controls.
