The executable and DLL can export functions, which can be used by other programs. Typically, a DLL exports functions (exports) that are imported by the executable. A DLL cannot run on its own and depends on a host process for executing its code. An attacker often creates a DLL that exports functions containing malicious functionality. To run the malicious functions within the DLL, it is somehow made to be loaded by a process that calls these malicious functions. DLLs can also import functions from other libraries (DLLs) to perform system operations.
Inspecting the exported functions can give you a quick idea of the DLL's capabilities. In the following example, loading a DLL associated with malware called Ramnit in pestudio shows its exported functions, giving an indication of its capabilities. When a process loads this DLL, at some point, these functions will be called to perform malicious activities:
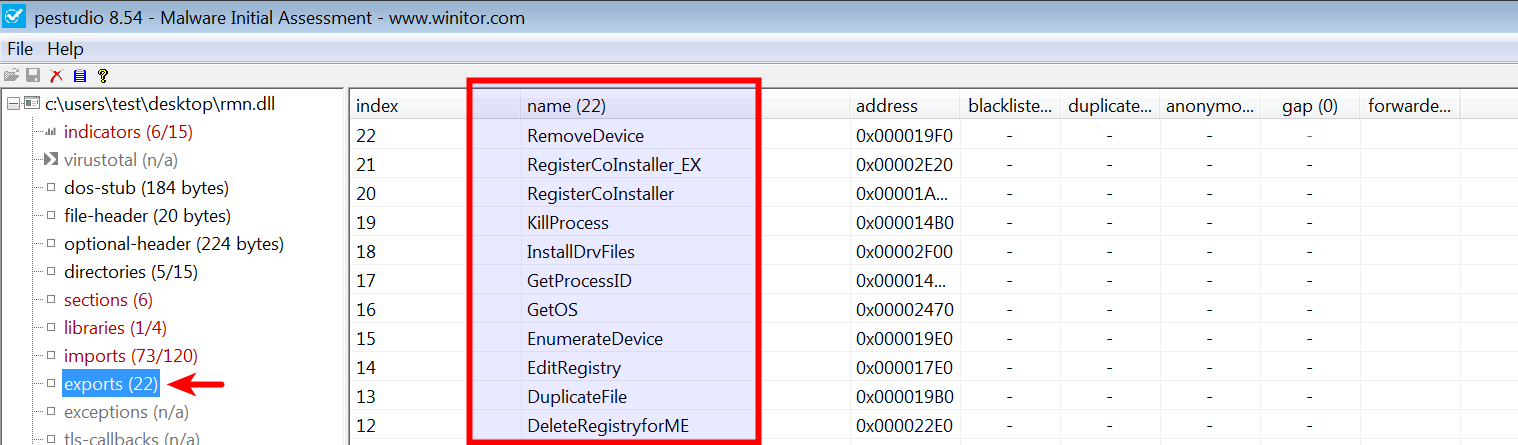
In Python, the exported functions can be enumerated using the pefile module, as shown here:
$ python
Python 2.7.12 (default, Nov 19 2016, 06:48:10)
>>> import pefile
>>> pe = pefile.PE("rmn.dll")
>>> if hasattr(pe, 'DIRECTORY_ENTRY_EXPORT'):
... for exp in pe.DIRECTORY_ENTRY_EXPORT.symbols:
... print "%s" % exp.name
...
AddDriverPath
AddRegistryforME
CleanupDevice
CleanupDevice_EX
CreateBridgeRegistryfor2K
CreateFolder
CreateKey
CreateRegistry
DeleteDriverPath
DeleteOemFile
DeleteOemInfFile
DeleteRegistryforME
DuplicateFile
EditRegistry
EnumerateDevice
GetOS
[.....REMOVED....]
