Attackers can spread their malicious program by infecting the removable media (such as a USB drive). An attacker can take advantage of Autorun features (or exploit the vulnerability in Autorun) to automatically infect other systems, when the infected media is plugged in to it. This technique typically involves copying files or modifying the existing files stored on the removable media. Once malware copies the malicious file to removable media, it can use various tricks to make that file look like a legitimate file to trick the user into executing it when the USB is plugged in to a different system. The technique of infecting removable media allows an attacker to spread their malware on disconnected or air-gapped networks.
In the following example, malware calls GetLogicalDriveStringsA() to obtain the details of the valid drives on the computer. After the call to GetLogicDriveStringsA(), the list of available drives is stored in the output buffer RootPathName, which is passed as the second argument to GetLogicalDriveStringsA(). The following screenshot shows three drives, C:, D:, and E:, after the call to GetLogicDriveStringsA(), where E: is the USB drive. Once it determines the list of drives, it iterates through each drive to determine if it is a removable drive. It does that by comparing the return value of GetDriveTypeA() with DRIVE_REMOVABLE (constant value 2):

If a removable media is detected, the malware copies itself (executable) into the removable media (USB drive) using the CopyFileA() API. To hide the file on removable media, it calls the SetFileAttributesA() API and passes it a constant value FILE_ATTRIBUTE_HIDDEN:

After copying the malicious file to removable media, the attacker can wait for the user to double-click on the copied file or can take advantage of Autorun features. Before Windows Vista, malware, apart from copying the executable file, also copied the autorun.inf file containing Autorun commands into the removable media. These Autorun commands allowed the attacker to start programs automatically (without user intervention) when the media was inserted into the system. Starting with Windows Vista, executing malicious binaries via Autorun is not possible by default, so an attacker has to use a different technique (such as modifying the registry entries) or exploit a vulnerability which could allow the malicious binary to execute automatically.
Some malware programs rely on tricking the user to execute the malicious binary instead of taking advantage of Autorun features. Andromeda is an example of one such malware. To demonstrate the tricks used by Andromeda, consider the following screenshot, which shows the content of the 2 GB clean USB drive before plugging it into the system infected with Andromeda. The root directory of the USB consists of a file called test.txt and a folder named testdir:

Once the clean USB drive is inserted into the Andromeda-infected computer, it performs the following steps to infect the USB drive:
- It determines the list of all the drives on the system by calling GetLogicalDriveStrings().
- The malware iterates through each drive and determines whether any drive is a removable media, using the GetDriveType() API.
- Once it finds the removable media, it calls the CreateDirectoryW() API to create a folder (directory) and passes an extended ASCII code xA0 (á) as the first parameter (directory name). This creates a folder called E:á in the removable media, and due to the use of extended ASCII code, the folder is displayed with no name. The following screenshot shows the creation of the E:á directory. From now on, I will refer to this directory created by the malware as the unnamed directory (folder):

The following screenshot shows the unnamed folder. This is the folder with the extended ascii code of xA0 that was created in the previous step:
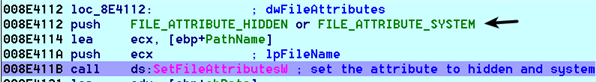
- It then sets the attributes of the unnamed folder to hidden and makes it a protected operating system folder by calling the SetFileAttributesW() API. This hides the folder on the removable media:
- Malware decrypts the executable content from the registry. It then creates a file in the unnamed folder. The created file name has the convention <randomfilename>.1 and it writes the PE executable content (malicious DLL) to this file (using the CreateFile() and WriteFile() APIs). As a result, a DLL is created with the name <randomfilename>.1 inside the unnamed folder, as shown here:

- The malware then creates a desktop.ini file inside the unnamed folder and writes icon information to assign a custom icon to the unnamed folder. The content of desktop.ini is shown here:

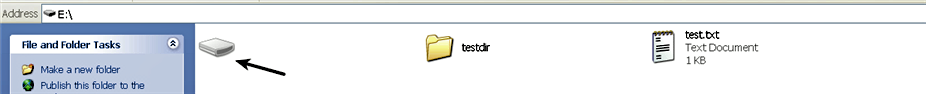
The following screenshot displays the icon of the unnamed folder which has been changed to the drive icon. Also, note that the unnamed folder is now hidden. In other words, this folder will only be visible when the folder options are configured to show hidden and protected operating system files:
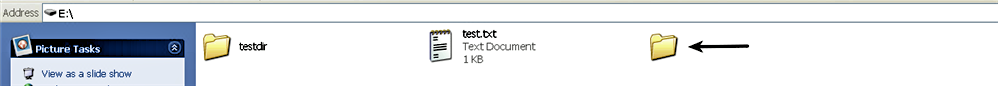
- The malware then calls the MoveFile() API to move all the files and folders (in this case, test.txt and testdir) from the root directory to the unnamed hidden folder. After copying the user's files and folders, the root directory of the USB drive looks like the one shown here:

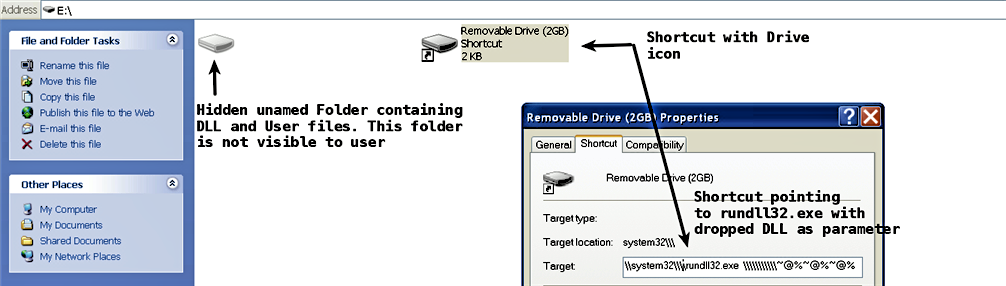
- The malware then creates a shortcut link that points to rundll32.exe, and the parameter to rundll32.exe is the <randomfile>.1 file (which was the DLL dropped in the unnamed folder earlier). The following screenshot displays the appearance of the shortcut file, and the properties showing the way a malicious DLL is loaded via rundll32.exe. In other words, when the shortcut file is double-clicked, the malicious DLL gets loaded via rundll32.exe, thereby executing the malicious code:
Using the aforementioned operations, Andromeda plays a psychological trick. Now, let's understand what happens when the user plugs in the infected USB drive on a clean system. The following screenshot shows the contents of the infected USB drive, which is displayed to the normal user (with default folder options). Notice that the unnamed folder is not visible to the user, and the user's files/folders (in our case, test.txt and testdir) are missing from the root drive. The malware is tricking the user into believing that the shortcut file is a drive:
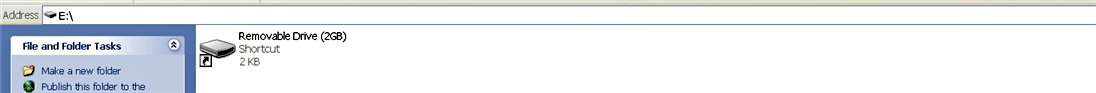
When the user finds all the important files and folders missing from the USB root drive, the user is very likely to double-click on the shortcut file (thinking that it is a drive) to look for the missing files. As a result of double clicking the shortcut, rundll32.exe will load the malicious DLL from the unnamed hidden folder (not visible to the user) and infect the system.
