To extract strings from a suspect binary, you can use the strings utility on Linux systems. The strings command, by default, extracts the ASCII strings that are at least four characters long. With the -a option it is possible to extract strings from the entire file. The following ASCII strings extracted from the malicious binary show reference to an IP address. This indicates that when this malware is executed, it probably establishes a connection with that IP address:
$ strings -a log.exe
!This program cannot be run in DOS mode.
Rich
.text
`.rdata
@.data
L$"%
h4z@
128.91.34.188
%04d-%02d-%02d %02d:%02d:%02d %s
In the following example, the ASCII strings extracted from a malware called Spybot give an indication of its DOS and Key logging capabilities:
$ strings -a spybot.exe
!This program cannot be run in DOS mode.
.text
`.bss
.data
.idata
.rsrc
]_^[
keylog.txt
%s (Changed window
Keylogger Started
HH:mm:ss]
[dd:MMM:yyyy,
SynFlooding: %s port: %i delay: %i times:%i.
bla bla blaaaasdasd
Portscanner startip: %s port: %i delay: %ssec.
Portscanner startip: %s port: %i delay: %ssec. logging to: %s
kuang
sub7
%i.%i.%i.0
scan
redirect %s:%i > %s:%i)
Keylogger logging to %s
Keylogger active output to: DCC chat
Keylogger active output to: %s
error already logging keys to %s use "stopkeylogger" to stop
startkeylogger
passwords
Malware specimens also use Unicode (2 bytes per character) strings. To get useful information from the binary, sometimes you need to extract both ASCII and Unicode strings. To extract Unicode strings using the strings command, use the -el option.
In the following example, the malware sample did not reveal unusual ASCII strings, but extracting the Unicode strings showed references to the domain name, and the Run registry key (which is frequently used by malware to survive the reboot); and it also highlights a malware's possible capability to add a program to the firewall whitelist:
$ strings -a -el multi.exe
AppData
44859ba2c98feb83b5aab46a9af5fefc
haixxdrekt.dyndns.hu
True
SoftwareMicrosoftWindowsCurrentVersionRun
Software
.exe
SEE_MASK_NOZONECHECKS
netsh firewall add allowedprogram "
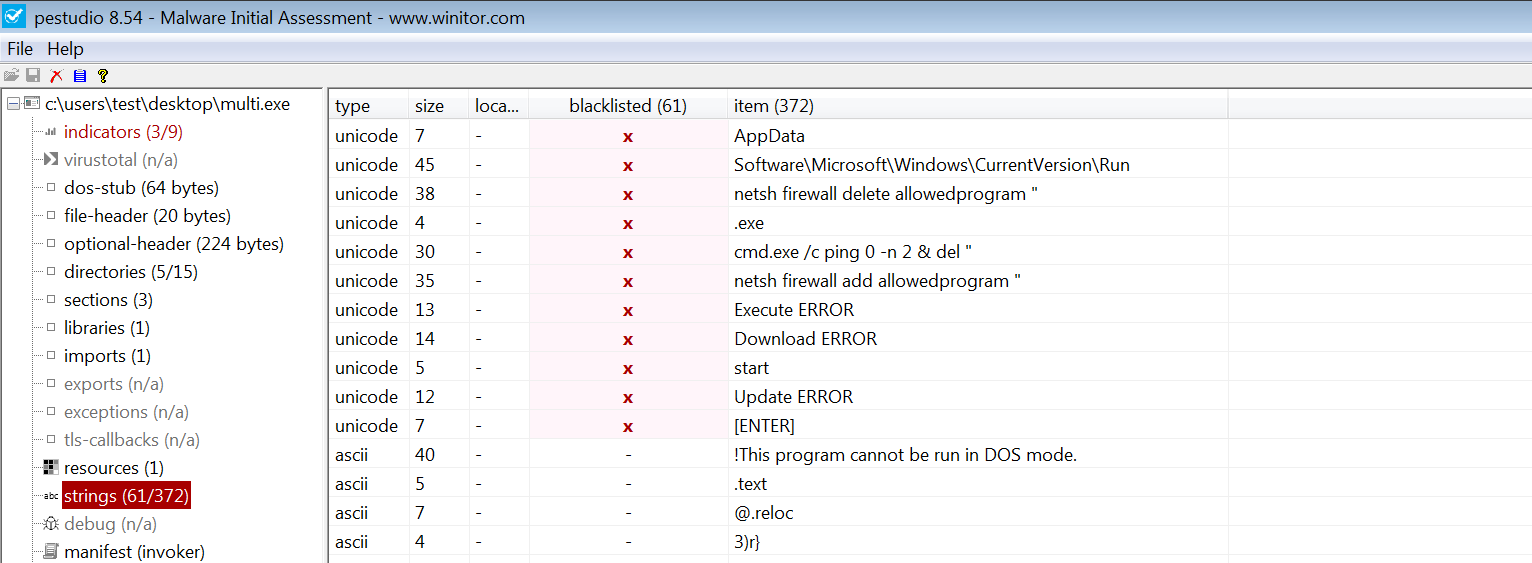
On Windows, pestudio (https://www.winitor.com) is a handy tool that displays both ASCII and Unicode strings. pestudio is an excellent PE analysis tool for performing initial malware assessment of a suspect binary, and is designed to retrieve various pieces of useful information from a PE executable. Various other features of this tool will be covered in subsequent sections.
The following screenshot shows some of the ASCII and Unicode strings listed by pestudio; it assists you by highlighting some of the notable strings in the blacklisted column, which allows you to focus on the interesting strings in the binary: