In this part, we will describe how to add, edit, and configure vSS and vDS. Working with GUI is easy, but you can use CLI of course. First, we will be working with a vSS switch. We show how it is easy to configure a new vSS.
We use first a host client direct on the ESXi host. This situation is good to know when you don't have already a vCenter Server. In this case, you need to prepare a first VM port group for the first VM. This happens typically before the deployment of vCSA (or the VM that will host the vCenter Server).
The following screenshot shows you the GUI host client where you click on Networking | Virtual switches | Add standard virtual switch:

When you create a new standard virtual switch, you have a lot of details, the vSwitch name (note that it's possible to give them a name only from the ESXi UI), the MTU, the used uplinks, the link discovery protocol (on vSS only CDP is supported), the security settings, and so on:

You can change your setting of vSS through the Edit settings option:
We created vSS with the name Mastering_New_vSS, but at the moment, it is not possible to connect virtual network interface cards (vNIC) from a VM to vSS. Why? We need to configure the VM port group.
So, you click only on the next left side from the Virtual switches option and click on the Port groups option, and here you find the Add port group button as follows:
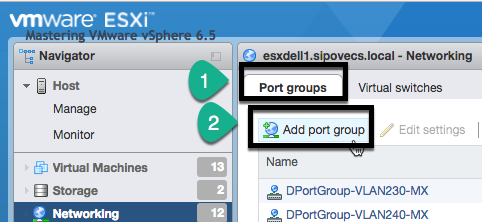
Under the Add port group option, you specify a name for port group, VLAN ID tag, and the correct vSS in our case as Mastering_New_vSS:

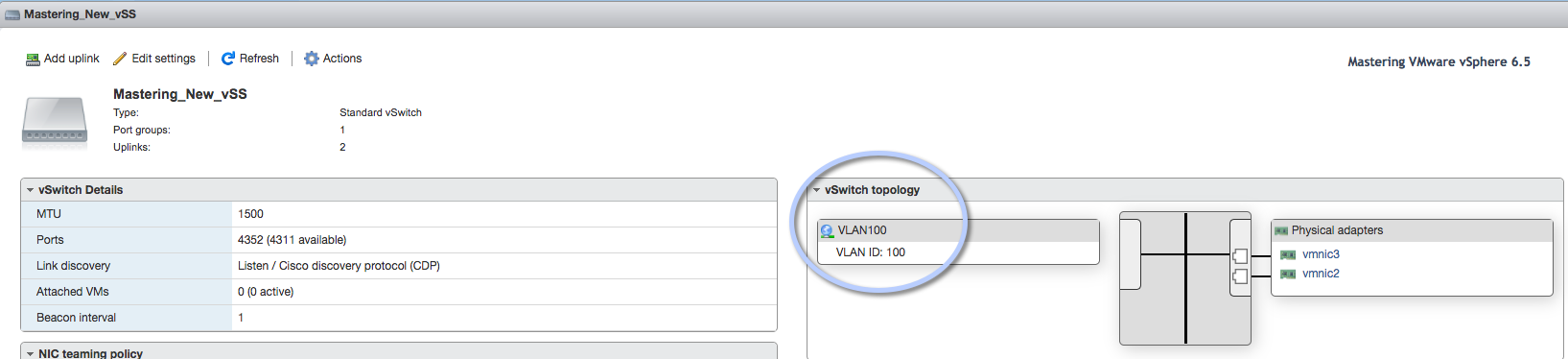
Yes, we have completed the configuration of vSS with VM port group, so we can add vNIC to this VLAN100 port group:
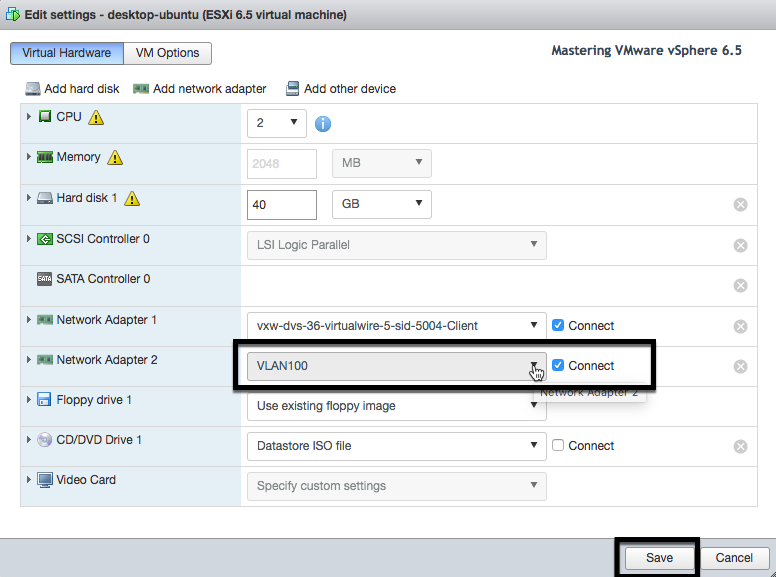
If you need to, it's very easy to change a VM port group, for example, to move a VM from one network to another network. On the VM, just choose the Edit settings option. You have to look at the virtual network card part of VM properties and define a new port group (or also distributed port group). In the following example, the Network Adapter 2 will be connected to the VLAN100 port group:
Now, we have a ready network for deploying the vCenter appliance. After deployment, we change GUI and connect to the vCenter server through vSphere Client (HTML 5) or vSphere Web Client.
After connecting to your vCenter Server, you can select one ESXi host and then choose the Configure tab. Then click on Networking | Virtual switches and you will see something like the following screenshot:
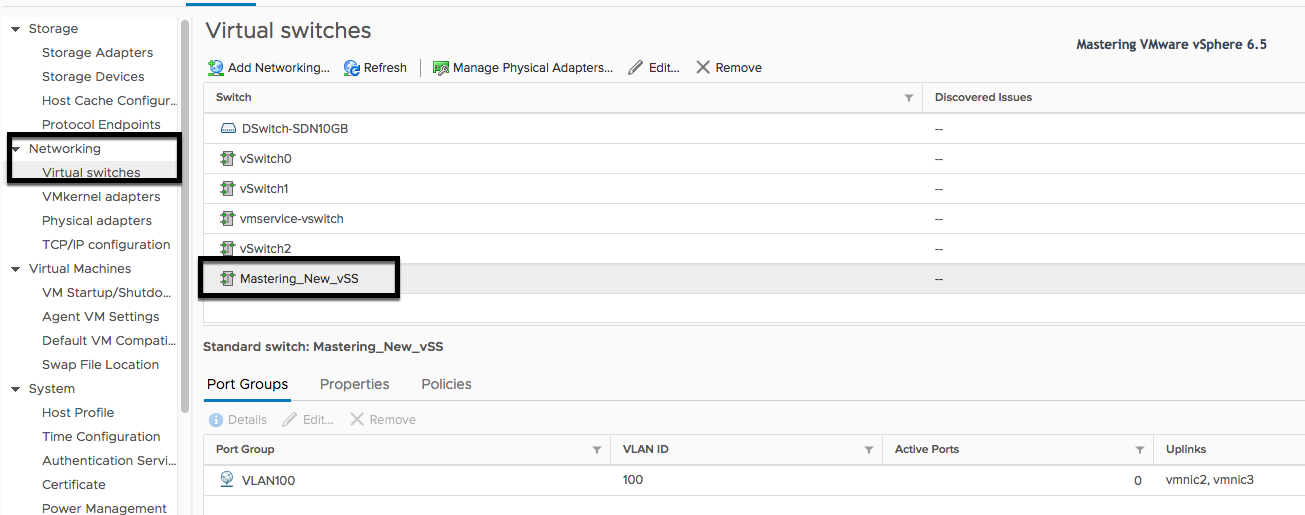
What is the possible configuration and change after creating vSS? Here is the detail after clicking on the Edit settings option:
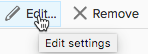
We can change settings in four tabs—Properties, Security, Traffic shaping, and Teaming and failover. The description of these tabs is as follows:
- Properties: Here, it is possible to change only one setting in MTU. The MTU can improve the networking efficiency. You can enable jumbo frames, and the MTU can be greater than 1,500, but you can't set the MTU size greater than 9,000 bytes. The number of ports is from vSphere 5.5 and later dynamically scaled up and down. So, it is not possible to get the vSS changed. In Elastic port allocation, the default number of ports is 8. When all ports are assigned, a new set of 8 ports is created:

- Security: This is an easy tab because here you can change three settings:
-
- Promiscuous mode: The options in this mode are as follows:
-
- Reject: This is the default option. Guest OS does not result in receiving frames for another VM.
- Accept: All frames passed on the virtual switch that is allowed under the VLAN policy for port group. This can be useful to detect and monitor traffic or sniffer traffic analyzer.
- MAC address changes: This provides for the following options:
-
- Reject: Guest OS changes the MAC address of the adapter to a value different from the address in the .vmx configuration file. The switch will block the port.
- Accept: This is the default option. Guest OS can change the MAC address of a network adapter, the adapter receives frames to its new address.
- Forged transmits: This is very similar to a MAC address changes option, but for outbound traffic. This provides for the following options:
-
- Reject: The switch drops any outbound frame with a source MAC address that is different from the one in the .vmx configuration file.
- Accept: The switch does not perform filtering and permits all outbound frames:

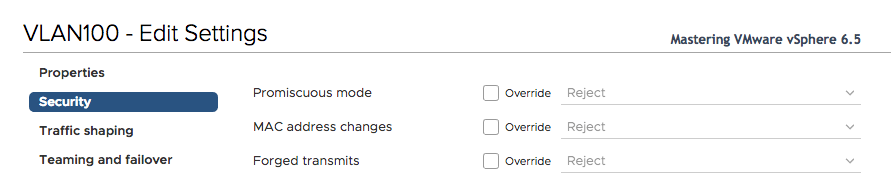
- Traffic shaping: When you need to shape traffic but with vSS, it is possible only on outbound network traffic. When you need bidirectional control, you must use vDS inbound and outbound traffic. This option is disabled by default.
When you enable the status you can set:
-
- Average bandwidth (kbit/s): Establish the number of bits per second to allow across a port, averaged over time. This number is the allowed average load.
- Peak bandwidth (kbit/s): The maximum number of kilobits per second to allow across a port when it is sending a burst of traffic. This number tops the bandwidth that is used by a port whenever the port is using its burst bonus.
- Burst size (KB): The maximum number of kilobytes to allow in a burst. This is useful if you want a permit whenever bandwidth peaks (bigger than the average bandwidth) for a limited time. Note that the burst is not expressed in time, but in size.

- Teaming and failover: This is the important part of vSS settings and it's composed of several options as follows:
- Load balancing: This option determines how network traffic is distributed between the network adapters in a NIC team, according to one of these algorithm:
-
- Route based on originating virtual port (default): The virtual switch selects uplinks based on the VM port IDs on the vSS or vDS. This method is without extra configuration on the physical switch and has low overhead.
- Route based on source MAC hash: The virtual switch selects an uplink for a VM based on the VM MAC address. To calculate an uplink for a VM, the virtual switch uses the VM MAC address and the number of uplinks in the NIC team. This method is a support for all physical switches and has low overhead.
- Route based on IP hash: The virtual switch select uplinks for VMs based on the source and destination IP address of each packet. The IP-based method requires 802.3ad link aggregation support or EtherChannel.
- Use Explicit Failover: No actual use load balancing with this policy. The virtual switch always uses the first uplink that is in the active adapter list. If not possible, one of the other active adapters will be used instead of the standby adapter.
- Network failure detection: This option is how you understand that one link is not usable. You can specify two methods for failover detection:
-
- Link status only: This is the default option. Detect failures on a link as a removed cables problem on the physical switch.
- Beacon probing: When you want to use this detection mode, you must have as a minimal for beacon probing, three or more NICs in the team. How does it work? It sends out and listens for Ethernet broadcast frames that physical NICs send to detect a link failure in all physical NICs in a team. ESXi hosts send beacon packets every second.
-
- Notify switches: This option is a single option (by default it's enabled) used to speed the change of the network topology at the physical switches level. When the physical port used for the VM traffic must be re-routed to a different physical port (for example, due to link failure), then the virtual switch sends notifications over the network to update the lookup tables on the physical switch. The same happens during vSphere vMotion migration.
-
- Failback: This option is another single option (again, by default it's enabled) that determines how a physical adapter is returned to active duty after recovering from a failure. By default, the adapter returns to active duty immediately.
- Failover order: This option specifies how the different uplinks (the physical NICs) are used:
-
- Active adapters: This continues to use the uplink when it is up as active
- Standby adapters: If there are no active adapters that are up, then the next uplink from the standby adapters list will be used
- Unused adapters: Never use this uplink
So, we now have a basic idea about setting vSS:

We have a ready vSS. We know settings on the vSS level, but we check edit settings on the Port Group level. Once more, it is very easy and click on the Edit... button on the port group VLAN100, as shown in the following screenshot:

You will see the very same settings as on the vSS level. The different tabs on the port group level are as follows:
- Properties: Here it is possible to change the name of the port group and change VLAN ID, as shown in the following screenshot:

- Security: Like the security settings described at the switch level. For each port group, it's possible to override the virtual switch configuration and have some settings that are more specific:
-
Traffic shaping: Like the traffic shaping settings described at the switch level. For each port group, it's possible to override the virtual switch configuration and have some more specific settings. Useful if you need to limit bandwidth only for the specific VMs group:
-
Teaming and failover: Like the teaming settings described at the switch level. For each port group, it's possible to override the virtual switch configuration with some settings that are more specific. Used, for example to change the active uplink for a specific port group and define a different network path (at layer 2) for different VMs or different VMkernel interfaces:

All these settings are possible to list through CLI. I would like to show you some esxcli commands that can be useful for you in practical life. For example, consider the following two commands:
- The first command lists the details for vSS Mastering_New_vSS. You can try the next command, esxcli, as it is very easy to use in the everyday life of administrating vSphere:
[root@esxi1:~] esxcli network vswitch standard list -v Mastering_New_vSS
Mastering_New_vSS
Name: Mastering_New_vSS
Class: etherswitch
Num Ports: 4352
Used Ports: 5
Configured Ports: 1024
MTU: 1500
CDP Status: listen
Beacon Enabled: false
Beacon Interval: 1
Beacon Threshold: 3
Beacon Required By:
Uplinks: vmnic3, vmnic2
Portgroups: VLAN100
- The second command gets information about policy settings on vSS Mastering_New_vSS:
[root@esxi1:~] esxcli network vswitch standard policy security get -v Mastering_New_vSS
Allow Promiscuous: false
Allow MAC Address Change: false
Allow Forged Transmits: false
When you write the esxcli network command and click on Enter, you will see all possible commands for the network:
[root@esxi1:~] esxcli network
Usage: esxcli network {cmd} [cmd options]
Available Namespaces:
firewall A set of commands for firewall related operations
ip Operations that can be performed on vmknics
multicast Operations having to do with multicast
nic Operations having to do with the configuration of Network Interface Card and getting and updating the NIC settings.
port Commands to get information about a port
sriovnic Operations having to do with the configuration of SRIOV enabled Network Interface Card and getting and updating the NIC settings.
vm A set of commands for VM related operations
vswitch Commands to list and manipulate Virtual Switches on an ESX host.
diag Operations pertaining to network diagnostics
In the next part, we will be describing and working with the VMkernel port.
