A new feature introduced in vSphere 6.5 is the encryption of VMs, that secures the VMDK virtual disks (also .vmx and swap files are encrypted), making the stored data unreadable.
To take benefit of encryption, you need to connect vCenter Server to a working Key Management Server (KMS) that provides the necessary keys to encrypt and decrypt VMs using the Key Management Interoperability Protocol (KMIP) protocol. To establish the connection between KMS and vCenter Server, the KMS performs a certificate exchange.
The components required to allow VM encryption features are the following:
- KMS: Generates and stores the keys passed to the vCenter Server to encrypt and decrypt the VMs.
- vCenter Server: This is the only component that can log in to the KMS to obtain the keys and push them to ESXi hosts. KMS keys are not stored in vCenter Server, which keeps a list of keys IDs only.
A KMS cluster configured in vCenter Server requires that all KMS instances added to the cluster are from the same vendor and must replicate keys. If you use different vendors in different environments, you can create a KMS cluster for each KMS specifying the default cluster. The first cluster added becomes the default cluster.
At the time of writing, there are three following KMS providers certified by VMware:
- HyTrust KeyControl: https://www.hytrust.com/
- Dell-EMC CloudLink: http://www.cloudlinktech.com/data-security-products/secure-vm/
- IBM Security Key Lifecycle Manager: http://www-03.ibm.com/software/products/en/key-lifecycle-manager
- Thales Vormetric Data Security Manager: https://www.thalesesecurity.it/products/data-encryption/vormetric-data-security-manager
- Gemalto SafeNet KeySecure: https://safenet.gemalto.com/data-encryption/enterprise-key-management/key-secure/
Additional vendors are going through certification.
A KMS is required to enable and use vSAN encryption. Multiple KMS vendors are compatible, including HyTrust, Gemalto (SafeNet), Thales e-Security, CloudLink, and Vormetric.
Access to the encrypted virtual disk requires a correct key owned only by the VM that manages the virtual disk. An unauthorized VM that tries to access the encrypted VMDK without the correct key will receive only meaningless data. No additional hardware is required for the encryption/decryption operation and performance is improved if the used processor supports the AES-NI instruction set because encryption is CPU-intensive. AES-NI should be enabled in your BIOS.
The encryption and decryption process of VMs is controlled by storage policies and the VM needs to be powered off before proceeding.
To encrypt VMs, you first need to configure a KMS in vCenter Server:
- From the vSphere Web Client, select vCenter Server in the inventory and select the Configure tab. Expand More and select Key Management Servers to access the KMS management section.
- Click the Add KMS icon to add the KMS server (you must have one in your network). Specify the required parameters and click OK to save the configuration:

- Once the KMS server is successfully added to vCenter Server, the Connection Status column is displayed as Normal. Once you have configured the KMS server, you can start encrypting VMs:

Change the storage policy of a VM by following this procedure:
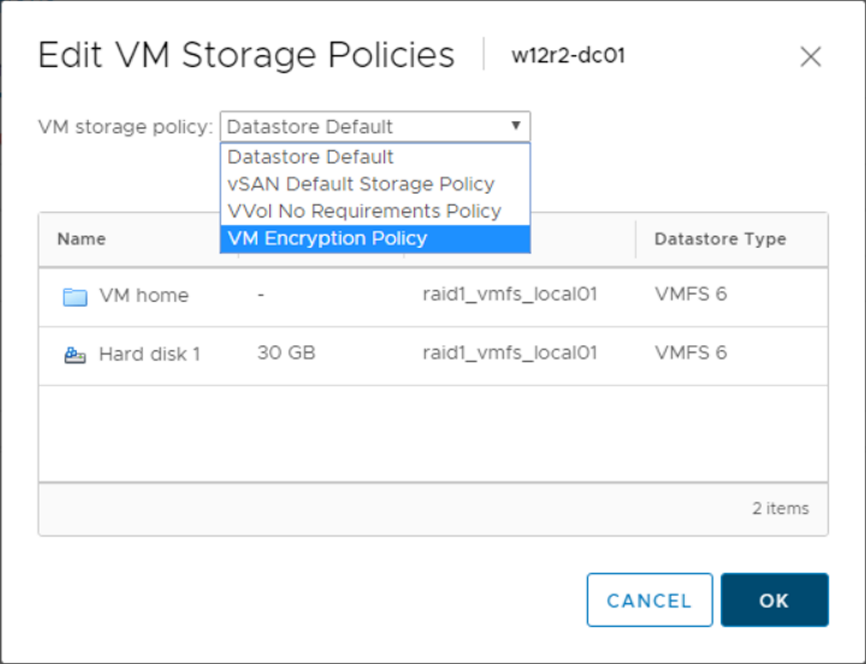
- From the vSphere Client, access vCenter Server and right-click the VM to encrypt. Select VM Policies | Edit VM Storage Policies.
- From the VM storage policy drop-down menu, select the VM Encryption Policy option to encrypt the VM and click OK:
- When the encryption process has completed, the VM Hardware area in the VMs Summary tab displays the Encryption field that indicates which components are encrypted:

Here are some recommendations for using encrypted VMs:
- PSC and vCenter Server VMs should not be encrypted.
- The support bundle used to decrypt a core dump is generated using the ESXi host key. If the host is rebooted, the host key may change and the support bundle can no longer be generated with a password or decrypt core dumps in the support bundle with the host key. For this reason, if the host crashes, you should retrieve the support bundle as soon as possible.
- Since .vmx files and .vmdk descriptor files contain the support bundle, do not edit these files, otherwise the VM becomes unrecoverable.
Encryption and decryption of a VM can also be performed using PowerCLI.
- To encrypt a VM, run the following command:
Get-VM -Name <vmname> | Enable VMencryption
- To decrypt a VM, use the following command:
Get-VM -Name <vmname> | Disable VMencryption
Also, you have to consider the following caveats:
- vSphere FT, vSphere Replication, and content library do not work with VM encryption.
- Snapshot operations have some limitations; for example, you cannot select the Snapshot the virtual machine's memory checkbox.
- Cloning an encrypted VM or performing a Storage vMotion operation and changing the disk format may not work. For example, if you clone a VM and attempt to change the disk format from lazy zeroed thick format to thin format, the VM disk keeps the lazy zeroed thick format.
- You cannot encrypt a VM and its disks by using the Edit Settings... menu. You have to use the storage policy.
- When you detach a disk from a VM, the storage policy information for the virtual disk is not retained.
- OVF export is not supported on an encrypted VM.
- You can use vSphere VM Encryption with IPv6 in mixed mode, but not in a pure IPv6 environment.
- The vCenter Server become more critical; only vCenter Server has the credentials for logging in to the KMS. Your ESXi hosts do not have those credentials. vCenter Server obtains keys from the KMS and pushes them to the ESXi hosts.
