As vSphere is one of the most critical infrastructure components, it is critical to use strong passwords that are not easily guessed, and that is difficult for password generators. Password strength and complexity rules apply to all passwords, including hosts users (such as root).
ESXi uses the pam_passwdqc.so plugin to set the strength and the complexity of the host's passwords. You can define the password quality using the host's advanced system settings, called Security.PasswordQualityControl.
ESXi 6.0 has presented another lockout feature; a limit of 10 failed logins is permitted before the account is locked. The account is unlocked after two minutes by default. In the host's events, you will see the following row:
Remote access to ESXi local user account 'LOGINNAME' has been locked for 120 seconds after ### failed login attempts.
Account locking works for access through SSH and the vSphere web services SDK. It does not apply to the DCUI and ESXi Shell.
If you are using a local SSO domain, you can enforce password and lockout policies to force the users to use complex passwords with specific requirements:

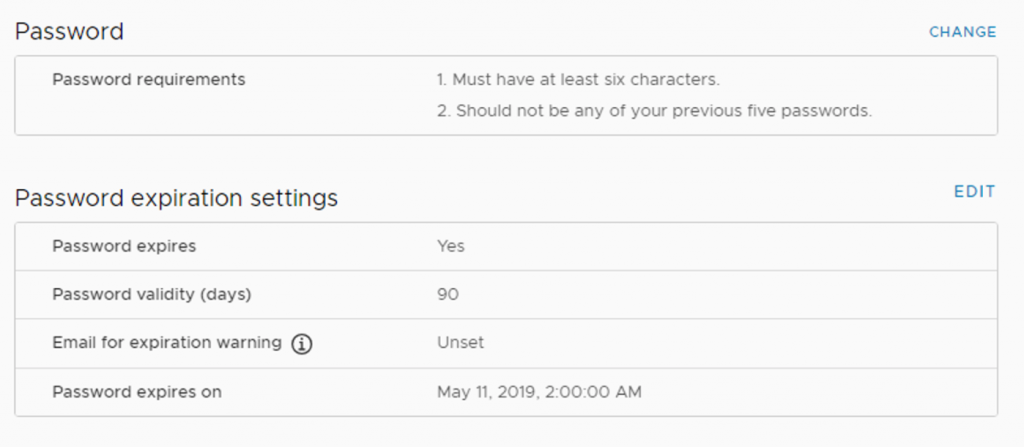
There are also password expiration rules for the virtual appliance local users, in case you are using vCSA for vCenter and/or the PSC components. Be sure also to check those settings:
- Log in to the VAMI interface of the vCSA
- Select the Administration tab from the navigator
- Configure the desired options related to the password policy, as shown in the following screenshot: