 Windows event log monitoring
by Andrea Vacche, Patrik Uytterhoeven, Rihards Olups
Zabbix: Enterprise Network Monitoring Made Easy
Windows event log monitoring
by Andrea Vacche, Patrik Uytterhoeven, Rihards Olups
Zabbix: Enterprise Network Monitoring Made Easy
- Zabbix: Enterprise Network Monitoring Made Easy
- Table of Contents
- Zabbix: Enterprise Network Monitoring Made Easy
- Zabbix: Enterprise Network Monitoring Made Easy
- Credits
- Preface
- I. Module 1
- 1. Getting Started with Zabbix
- The first steps in monitoring
- Zabbix features and architecture
- Installation
- Summary
- 2. Getting Your First Notification
- 3. Monitoring with Zabbix Agents and Basic Protocols
- 4. Monitoring SNMP Devices
- 5. Managing Hosts, Users, and Permissions
- 6. Detecting Problems with Triggers
- 7. Acting upon Monitored Conditions
- 8. Simplifying Complex Configurations with Templates
- 9. Visualizing Data with Graphs and Maps
- 10. Visualizing Data with Screens and Slideshows
- 11. Advanced Item Monitoring
- 12. Automating Configuration
- 13. Monitoring Web Pages
- 14. Monitoring Windows
- 15. High-Level Business Service Monitoring
- 16. Monitoring IPMI Devices
- 17. Monitoring Java Applications
- 18. Monitoring VMware
- 19. Using Proxies to Monitor Remote Locations
- 20. Encrypting Zabbix Traffic
- 21. Working Closely with Data
- 22. Zabbix Maintenance
- A. Troubleshooting
- B. Being Part of the Community
- 1. Getting Started with Zabbix
- II. Module 2
- 1. Zabbix Configuration
- 2. Getting Around in Zabbix
- 3. Groups, Users, and Permissions
- 4. Monitoring with Zabbix
- Introduction
- Active agents
- Passive agents
- Extending agents
- SNMP checks
- Internal checks
- Zabbix trapper
- IPMI checks
- JMX checks
- Aggregate checks
- External checks
- Database monitoring
- Checks with SSH
- Checks with Telnet
- Calculated checks
- Building web scenarios
- Monitoring web scenarios
- Some advanced monitoring tricks
- Autoinventory
- 5. Testing with Triggers in Zabbix
- 6. Working with Templates
- 7. Data Visualization and Reporting in Zabbix
- 8. Monitoring VMware and Proxies
- 9. Autodiscovery
- 10. Zabbix Maintenance and API
- C. Upgrading and Troubleshooting Zabbix
- III. Module 3
- 1. Deploying Zabbix
- 2. Distributed Monitoring
- 3. High Availability and Failover
- Understanding high availability
- Understanding the levels of IT service
- Some considerations about high availability
- Implementing high availability on a web server
- Configuring the Zabbix server for high availability
- Implementing high availability for a database
- Summary
- 4. Collecting Data
- 5. Visualizing Data
- 6. Managing Alerts
- 7. Managing Templates
- 8. Handling External Scripts
- 9. Extending Zabbix
- 10. Integrating Zabbix
- D. Bibliography
- Index
Zabbix supports log file monitoring on Windows as well—the topics we discussed in Chapter 11, Advanced Item Monitoring still apply. But on Windows there is also a specialized logging subsystem, and Zabbix does offer built-in event log system support. Windows has various event log categories, and we could monitor the Security event log. Other common logs are System and Application, and there will be more logs in recent versions of Windows. For now, let's head to Configuration | Hosts, click on Items next to Windows host, and click on Create item. Fill in the following:
- Name:
Windows $1 log - Type: Zabbix agent (active)
- Key:
eventlog[Security,,,,,,skip] - Type of information: Log
- Update interval:
1
That's six commas in the item key. When done, click on the Add button at the bottom. The last parameter we specified here, skip, will prevent the agent from reading all of the security log—a pretty good idea for systems that have been around for some time. Visit Monitoring | Latest data and click on History for the Windows Security log item:
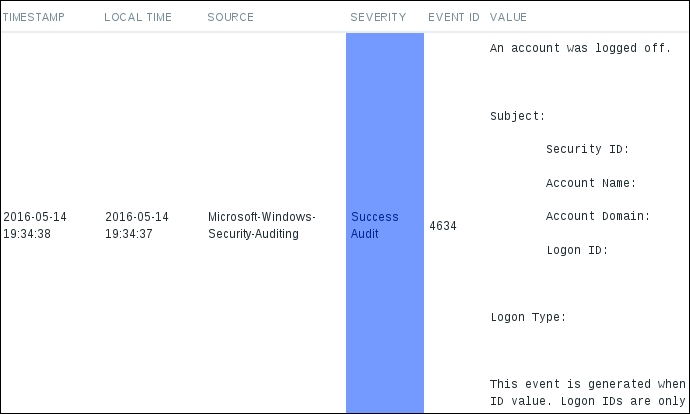
A few notable differences, compared to normal log file monitoring, include automatic data population in the LOCAL TIME column, as well as source, severity, and the event ID being stored. Actually, we can filter by some of these already at the agent level; we don't have to send all entries to the server. Let's discuss some of the item key parameters in a bit more detail. The general key syntax is this:
eventlog[name,<regexp>,<severity>,<source>,<eventid>,<maxlines>,<mode>]
The second parameter, regexp, operates the same as in normal log file monitoring—it matches a regular expression against the log entry. The maxlines and mode parameters work the same as they do for log and logrt item keys. The severity, source, and eventid parameters are specific to the eventlog key, and they are all regular expressions to be matched against the corresponding field. This way, we can filter the eventlog quite extensively on the agent side, but people make a somewhat common mistake sometimes—they forget that these are regular expressions, not exact match strings. What does that mean? Well, the following item key would not only match events with the ID of 13, as follows:
eventlog[Security,,,,13]
It would also match events with IDs of 133, 1333, and 913. To match 13, and 13 only, we'd have to anchor the regular expression:
eventlog[Security,,,,^13$]
-
No Comment