In this section, we're going to be talking about how to inject code into the browser, into the target computer. Since we're the MITM and since everything flows through our device, when someone requests a page we can actually insert any type of code that we want into that page. Browsers can run two types of code; they can run HTML code, and they can run JavaScript code. HTML code is the code responsible for the way that the page looks, so it's the code for the buttons, for the text, for the images, all of that. It can't really be used to do anything that will allow us to gain any access to the target computer. JavaScript, on the other hand, is a programming language that can be used to do many things, and we'll see that in later sections. In this section, we'll see how to inject JavaScript code into the target browser. We can use the same method to inject HTML, but JavaScript is more useful. That's why we're going to use our example to inject JavaScript.
So, let's first of all run MITMf with the --help command, and it will show us what options we have with the --inject plugin, as shown in the following screenshot:
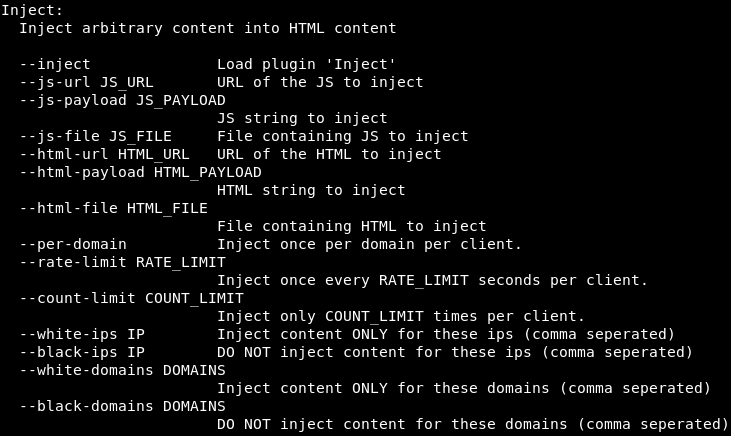
We're going to be using the same command that we always use. The only difference is we're going to insert the --inject plugin, and then we have different options for injection. There are three main options:
- We can have our code stored into a file, and we can use --js-file or --html-file to inject the code stored in the file that you specify.
- Code can be stored online, and it has a URL. We can use that URL using the --js-url or the --html-url options.
- We can actually supply the code itself through the command using the --js-payload or the --html-payload options.
We're going to be supplying the code through the command the first time, and then do it using a file. We're going to be using --inject payload, and then we're going to be doing --js-payload.
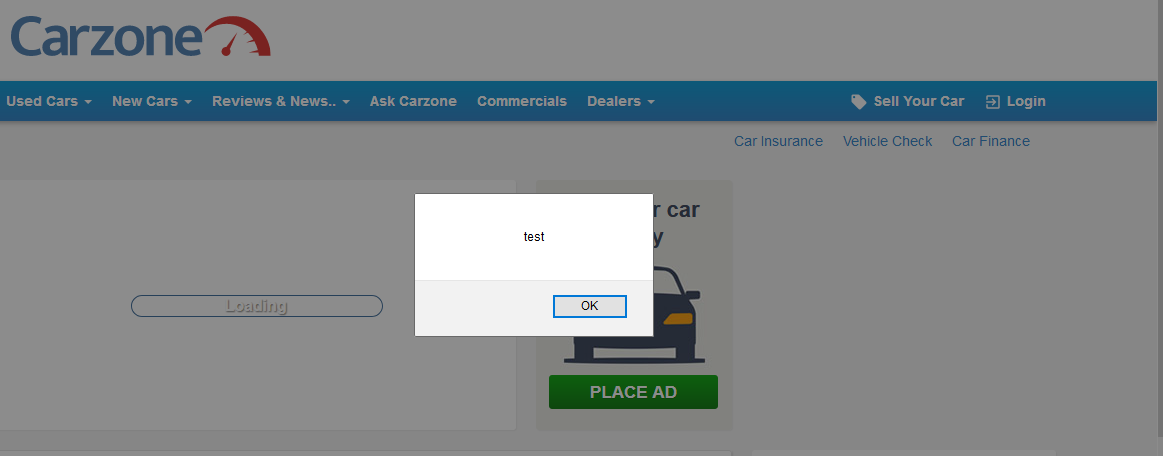
Our command is going to be the same as always, mitmf, and then we're going to add the option, the plugin, which is --inject, and then we're going to tell it that we want to specify the code through the command. We're going to use the --js-payload, as then we can put the JavaScript code after the --js-payload option. We are going to put in our JavaScript code, and we are going to use very simple code that will only display a message on the target computer. Our code is not going to try to hack anything; all it's going to do is just display a message box on the target computer, and in further sections we'll see how we can use this option to do more powerful attacks. So, basically, our code is going to do an alert() function in JavaScript, and the alert is just going to say test. So, our command is the same, it's mitmf --arp --spoof; our interface, -i; the --gateway; the --target; and then we loaded the --inject plugin; and we're telling it we're specifying the code through the command. The code that we want to run is alert('test'), and that's it. The command is as follows:
mitmf --arp --spoof -i eth0 --gateway 10.0.2.1 --target 10.0.2.5 --inject --js-payload "alert('test')"
We can check the result by going to the target system, browsing to a normal web page, and seeing what happens. We are just going to go to Carzone.ie, and as we can see in the following screenshot, the page displays a message box, and that message box says test:
So again, this is very simple code that doesn't really allow us to do anything on the target computer, but we can use it in further sections to do more powerful attacks.
Again, we can actually Google JavaScript codes and see codes that will be useful for us. For example, there are JavaScript keyloggers, there are codes that can take screenshots of the target computer, and there are a lot of other codes. You can redirect the target computer somewhere else, steal their cookies; you can do a lot of these powerful attacks.
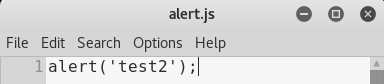
Another way to run an inject attack is by using a file. If we are using one of these more complicated codes, it's going to be hard to write it through the command, so we would be better off storing the code into a file and using the --js-file option. All we will have to do is open our Leafpad and get our code. We are actually just going to run leafpad, and we are going to write the same code that we did in the preceding example into a file. We are going to make an alert pop up, alert('test2');. We are going to save the file as alert.js, and we are going to store that in our /root directory:
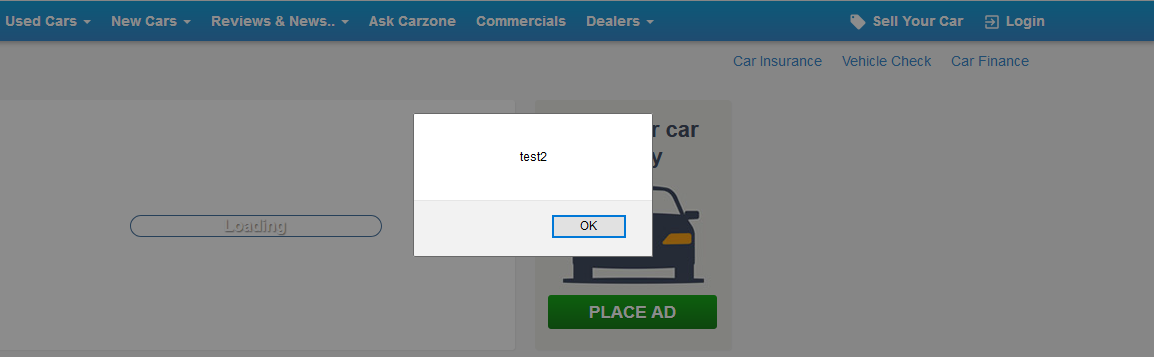
So again, if we are Googling or if we are using a more complicated code, we can have it all in this file, and then inject it. Run the command as we did before; the only difference is that instead of using the --js-payload, we're going to use --js-file, and we're going to specify the file, the full path to the file. We stored it in the /root directory as alert.js. If we download a file from the internet that contains a keylogger, for example, or a file that will redirect the target computer to some other site, then again we use the same command, but make sure we put --js-file and then the full path to where that file is stored. The command is as follows:
mitmf --arp --spoof -i eth0 --gateway 10.0.2.1 --target 10.0.2.5 --inject --js-file /root/alert.js
We will then launch this command, and MITMf will start the process. We are going to come back to the target. Let's browse for something. We will see that our code, the second code that we injected, which was called test2, was executed on the target machine. The result of the attack can be seen in the following screenshot:
Now, again, these are really simple codes just displaying a message box, but we can download or look for more complicated JavaScript codes, or just follow up in the further sections and see how we can use this feature to carry out more powerful attacks.
