The first thing we do before we start trying to exploit or find any vulnerabilities is information gathering. Therefore, we try to gather as much information as possible about the target, and web applications are no different. We're going to start by trying to get as much information as we can about the target IP address, the domain name info, the technology that is used on the website, which programming language is used, what kind of server is installed on it, and what kind of database is being used. We're going to gather information about the company and its DNS records, and we'll also see if we can find any files that are not listed, or any subdomains that are not visible to other people. Now, we can use any of the information gathering tools that we used before; for example, we can use Maltego and just insert an entity as a website, and then start running actions. It's exactly the same as we did with a normal person, in Chapter 11, Client Side Attacks - Social Engineering. We can also use Nmap, or even Nexpose, and test the infrastructure of the website and see what information we can gather from that. Again, we won't be going over that because we've seen it in previous chapters. There is no difference between a website or a normal computer—as we know, a website is just another computer. So, what we are going to be focusing on are technologies that we will only see on websites, such as domain names, DNS records, and stuff like that, that we either won't be able to use or haven't seen before in the previous chapters.
Now, the first thing that we're going to have a look at is Whois Lookup. Whois Lookup is a protocol that's used to find the owners of internet resources, for example, a server, an IP address, or a domain. So, we're not actually hacking; we're literally just retrieving info from a database that contains information about owners of stuff on the internet. So, for example, when we sign up for a domain name, if we wanted to register a domain name, for example, za1d.com, when we do that, we have to supply information about the person who is signing in, the address, and then the domain name will be stored in our name and people will see that Zaid owns the domain name. That is all we're going to do.
If we google Whois Lookup, we will see a lot of websites providing the service, so we will use http://whois.domaintools.com/, enter our target domain name, isecurity.org, and press Search:
As we can see in the following screenshot, we get a lot of information about our target website:
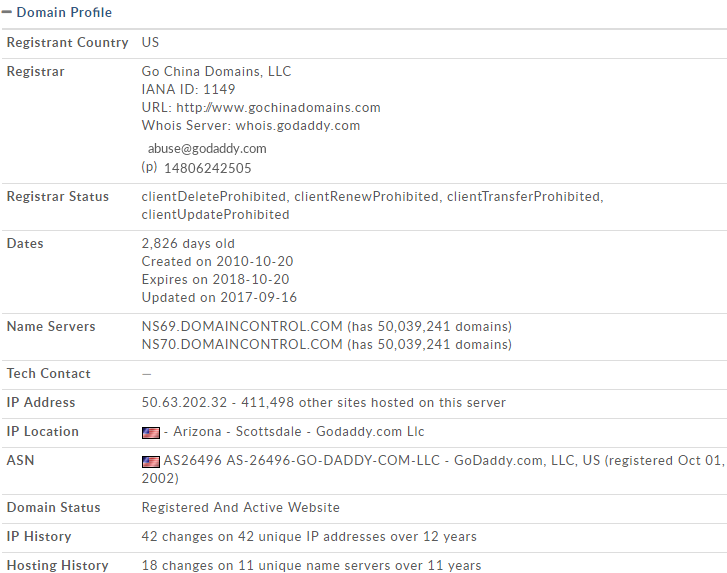
We can see the email address that we can use to contact the domain name info. Usually, we will be able to see the address of the company that has registered the domain name, but we can see that this company is using privacy on their domain; but if they haven't, that is, if they're not using privacy, we will be able to see their address and more information about the actual company.
We can see when the domain name was created, and we can see the IP Address of isecur1ty.org. If we ping the IP, we should get the same IP address as mentioned in the preceding screenshot.
If we run ping www.isecur1ty.org, the same IP address is returned:

We can see the IP Location, we can see the Domain Status, and we can also access the History, but we need to register for that. Now, again, we can use this information to find exploits.
In the following screenshot, in the Whois Record, we can find more information about the company that registered this domain:

This is basic information, but it's very helpful in the long run, just to know what our target is, what their IP is, and what services they are using. We can also see the name servers that are being used and we can see which company they are provided by.
