In this and the coming sections, we're going to have a look at a tool called BeEF. The Browser Exploitation Framework (BeEF) allows us to run a number of commands and attacks on a hooked target. A hooked target is basically a target that executes an URL or a JavaScript code given to us by BeEF. Once the target is hooked, we'll be able to run all the commands that BeEF allows us to.
The first thing we're going to have a look at is the main interface of BeEF, how to run it, and a very simple way to hook a target to BeEF. To run BeEF, we just have to click on the BeEF icon on the desktop. It'll automatically run the http://127.0.0.1:3000/ui/panel URL, which contains the browser interface or the web interface of the tool. It'll ask for a username and a password. The username is beef and the password is beef as well. Once logged in, on the left, we'll see the browsers that we have access to, in the Hooked Browsers pane:
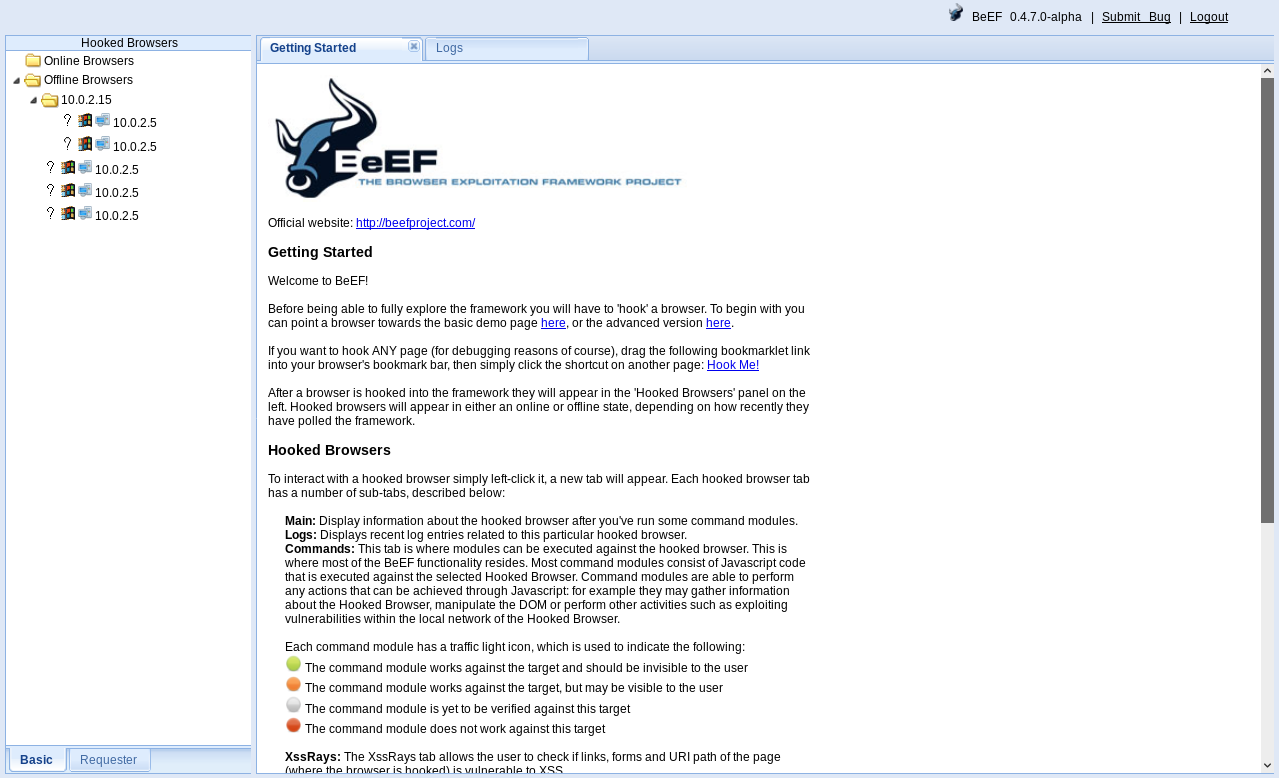
The Online Browsers are the browsers that we currently have access to, and the Offline Browsers are the ones that we had access to. At the moment, we can't run any commands on the browsers; we had access to these browsers before, but we can't currently do anything on them.
What interests us is the Online Browsers. There are a number of methods to get browsers or targets hooked to BeEF. If we just go back to the Terminal window, we can see that it's telling us the script URL that has to be executed on the target browser so that they get hooked to BeEF:
![]()
If we can find or think of a way to get the preceding piece of URL to be executed on the target computer, then that target will be hooked to BeEF, and then we will be able to run all types of commands on that computer.
We can use methods that we've already learned, we can use DNS-spoofing to spoof any request to any page or to a page containing the hook, or we can do ARP poisoning and inject the hook URL into any page that the target browses. We can use an XSS exploit, which we'll talk about in Chapter 21, Cross-Site Scripting Vulnerabilities. Or we could create a page and social engineer our target to open that page, a hook page. We are going to create a hook page and see how a target will be hooked. The hook page that we're going to create can be used with social engineering and DNS-spoofing.
The page that we are going to create is very simple. We can use any page we want and place the hook URL at the end of the page. We can go on any website, copy the source of that website, and then place the hook URL under that. We are going to be doing something simpler; we are just going to put it into our /var/www/html directory—that's where the web server files are stored. We are going to modify our index.html file, we'll delete everything, and put in the hook URL that was given to us by the tool. We also need to modify the IP and put in the IP of the attacking machine. So the IP of the Kali machine and our IP is 10.0.2.15:

Now we're good to go, and any person that browses the index.html page will be hooked to the BeEF browser, or to the BeEF framework. We also need to start the web server, Apache. To start it, we run the service apache2 start command. Now the Apache server should be running. Again, we can use social engineering or we can use DNS-spoofing to get our target person to browse to the index.html page. We can upload the same page onto a remote server and get access to it, or we can think of any other way we want.
At the moment, we are going to just browse to it on our Windows browser, enter the 10.0.2.15 IP, and hit Enter – a blank page should open up:
Our page doesn't really say anything, but if we go to our BeEF browser, we will see that we have a new IP in the Online Browsers, and if we click on that IP, we will see some basic details about the target computer:
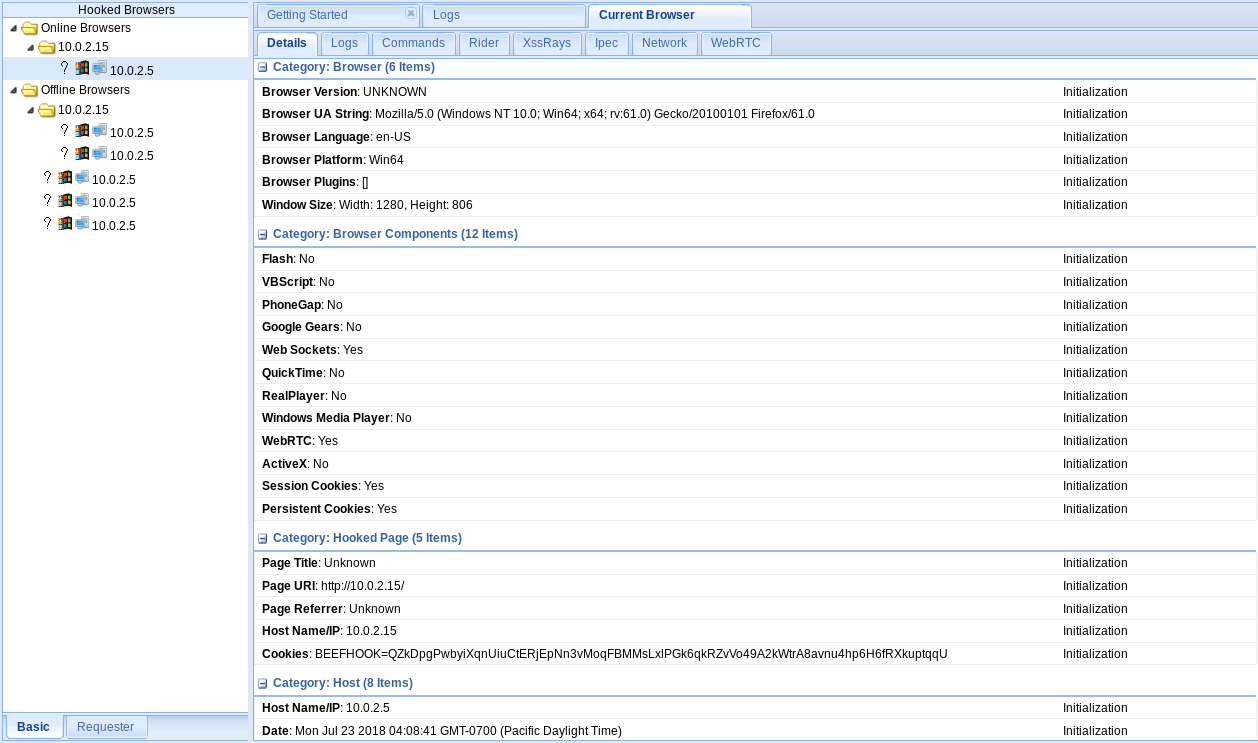
We can see that the target is using Mozilla/5.0 with Windows NT 10.0, it's Firefox/61.0. We can also see the installed Browser Plugins. These are very useful if we want to run buffer-overflow exploits on the target computer. We can also see the Page URL that we managed to get the hook from, and we can see the Cookies information at the bottom, as well and details about the date and the Window Size.
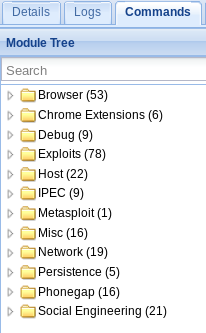
The Commands tab is the one we'll use the most. The following screenshot shows a large number of commands and attacks on the target computer—we'll be dealing with this later:
The Rider tab will allow us to see and create HTTP requests:
The XssRays tab will show us whether the target web page has any XSS vulnerabilities:
The Ipec tab is a BeEF Command Prompt, which will allow us to run BeEF commands from the Command Prompt instead of using the interface:

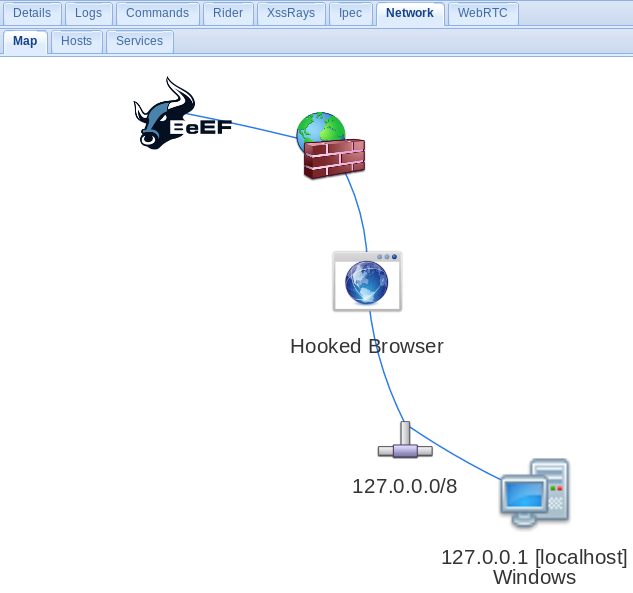
The Network tab will give us an overview of the current network:
Once we're done with everything, we can click on the Logout link and we will be logged out of the tool.
This is just a basic overview of BeEF, the main commands and the interface, and a really basic way of hooking a target. Again, we can get people to run the hook page by using social engineering, such as a URL-shortening service to make the link shorter and look nicer, or we can do DNS-spoofing and get the target person to redirect to our own web page where the BeEF framework is working.
