In this section, we're going to talk about a tool called Wireshark. Wireshark is a network protocol analyzer. It's not designed for hackers, and it's not designed for hacking and spying on other people on the network. It's designed for network administrators so that they can see what's happening in their network and make sure that everything is working properly, and that nobody is doing anything bad or suspicious on the network. The way that Wireshark works is it allows you to select an interface and then logs all the packets, or all the traffic, that flows through that interface. So, we are selecting an interface (it could be a wireless card, or it could be a wired card on our current computer), and then it'll start logging all the information that flows through that interface. It also has a really nice graphical interface that allows us to analyze this traffic, so it allows us to filter these packets based on the protocol used in them, such as HTTP or TCP. It also allows us to look for certain things, such as cookies or POST or GET requests, and it also allows us to search through these packets. We can search through the information that's stored in the packets, and find the things that we are looking for. This tool has a vast number of applications, and we might need a entire book to cover them all, so in this book we're actually going to use it in just a few sections, just covering the basics and the things that are related to us.
The main idea here is that Wireshark is not a hacking tool. It only allows us to capture the traffic that flows through our own computer, or interface. So, we are just going to go to Kali, and we're going to start Wireshark. We can run the wireshark command from the Terminal. First of all, you can actually just go to File | Open, and in here you can open a file that we've already captured. For example, you may have captured packets using a different sniffer, such as Airodump, MITMf, or TShark, which is the Terminal part of Wireshark.
If we captured packets using any of these programs and you stored it in a file, we can just come in here, open it, and start analyzing that file:
This is really handy because sometimes we don't really want to analyze the traffic on the fly. Sometimes we just want to capture traffic from a small laptop, or from our phone, and we may not even be at home. We may be somewhere else doing our pen test, and then we go back home and then we want to analyze what we captured. In such cases, we can store that in a file and then just open Wireshark and open the file that we want to analyze. The main idea here is that Wireshark is not a hacking tool, it's not going to capture things happening in another device. It will only capture things that flow through our own interface.
So, we can see in the following screenshot that we have all the interfaces in our computer. We can see that we have eth0, and we have all the other ones, some of which are created by VirtualBox:
The main one in the preceding screenshot is eth0, which is the virtual interface connected to our NAT network.
Now, open a browser and go to a normal website, such as Google. Now, as we can see in the following screenshot, we can see the traffic in the eth0 interface graph is spiking, so there was some traffic generated through that interface:
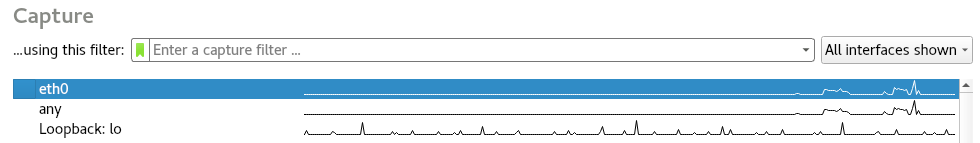
So, if we're sniffing on eth0, we will be able to capture the packets that were sent.
Now, go to our Windows machine just to prove that point; browse to the website, and we will see that eth0 will not be affected. The traffic that's generated on this Windows machine, which is in the same network as the Kali machine, will not be captured by the Kali machine.
So, why is Wireshark so useful, why are we even talking about it if we can only see things that go through our own computer? Why are we talking about it? Well, we're talking about it because we've seen that there are many ways that we can become the MITM.
Now, we talked about two methods of becoming the MITM. We talked about doing it using ARP spoofing, and if we create a fake access point then we'll naturally be the MITM because all the requests will be going through the fake access point and start sniffing on the interface that's used to become the MITM. We'll be able to capture all the traffic generated by the people that we're targeting in our MITM attack. So, if we start a fake access point, we can start sniffing on the interface that's broadcasting the signal, and we can capture all the packets sent to or received by anyone who is connected to that fake access point. If we become the MITM using ARP spoofing, then just select the interface that we used when we launched our ARP spoofing attack. We are going to perform this with ARP spoofing because it's quicker and easier than generating a fake access point, but again, this works on both ways. It even works if we manage to become the MITM using a different method. Just make sure we select the interface that's used to launch that attack.
So, we are going to look at ARP spoofing. We can do it using arpspoof, or you can you do it using MITMf. We're going to do it using MITMf, and our command is going to be mitmf --arp --spoof -i, which is going to be eth0, then we're going to specify the --gateway, 10.0.2.1, and then the --target, which is 10.0.2.5. So, we performed this command before. It will just put us as the MITM. It'll redirect the traffic from the computer that has the IP 10.0.2.5 to our computer, placing us in the middle. Run the attack using the following command:
mitmf --arp --spoof -i eth0 --gateway 10.0.2.1 --target 10.0.2.5
Go to the Windows machine. If we do any browsing here, it is going to affect the traffic in eth0. We'll see whether Wireshark will be able to capture traffic generated by this Windows machine. Browse to Google, or a different website, and if we come back to the tool, in the following screenshot you will see that we have traffic being generated here. We can see that eth0 is actually capturing packets in a completely different device, a device that's not even connected to our network:
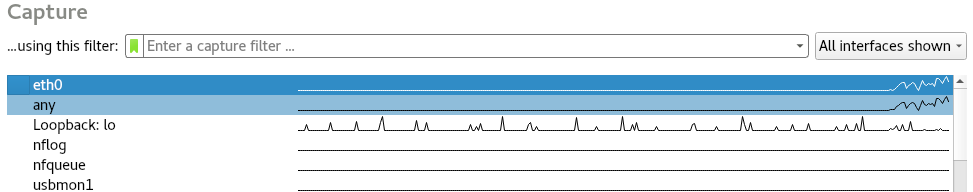
This is happening because when we are the MITM and all the packets that are generated by the Windows device are actually being redirected to our Kali device, and then Wireshark is sniffing them from the Kali machine, it's sniffing it from own local machine. It's not sniffing it from the network, it's not sniffing it from the target computer, it's only listening on current interface, which is eth0, and it can capture packets that are flowing through eth0 because MITMf has redirected the traffic of the Windows machine to flow through the Kali machine.
So, again, if an attack is performed with the fake access point, then just listen on the interface that we are broadcasting from. If we are performing this attack with a real wireless network, if we are connected to our home wireless network using wlan0, then we can perform it with wlan0. But with ARP spoofing, we have to first redirect the traffic. Then we can use Wireshark. Now, this is just to show what Wireshark is and how it works, and we just want to stress the idea that Wireshark is not a hacking tool. It's only a program that allows us to log packets flowing through a certain interface and then analyze these packets. So, in the next section, we'll see how we can sniff and analyze packets using Wireshark.
