In this section, we'll discuss a tool called the MANA Toolkit. The MANA Toolkit allows us to create fake APs. It is very easy to use, and it automatically creates fake APs for us, so that we don't have to manually type commands. The tool also has a few scripts, allowing us to run a number of tools to sniff traffic in the fake AP, bypass HTTPS, and even attempt to bypass HSTS.
The tool comes with three main scripts:
- start-noupstream.sh: Basically, this script will create a fake AP. This AP will not have an internet connection, so, when someone connects to this fake AP, they will not be able to connect to the internet.
- start-nat-simple.sh: This creates a fake AP with an internet connection. So, when someone connects to this AP, they will be able to access the internet, and all of the packets will be flowing through our device (because we are the router), so we'll be able to analyze, capture, and read the packets.
- start-nat-full.sh: This script will create an AP with an internet connection, and it will also automatically start sniffing and recording the packets that are flowing through the fake AP; it will attempt to bypass HTTPS and HSTS.
We are not going to use the start-nat-full.sh script, because it actually fails a lot of the time. We're only going to use the start-nat-simple.sh script, for creating an AP with an internet connection. In the future, we'll see how to capture and analyze the packets.
Before getting into more detail, let's take a look at the settings for the Kali machine. Go to Settings | Network, and make sure that you're using a NAT network. This is exactly what we saw in Chapter 3, Linux Basics.
Run the following command to install the MANA Toolkit:
apt-get install mana-toolkit
If it is already installed, it will tell us that it is, along with its version. If we use ifconfig, we'll see that we have an interface called eth0; this interface is actually used by VirtualBox in the NAT network, so it's a virtual interface that is connected to that network:
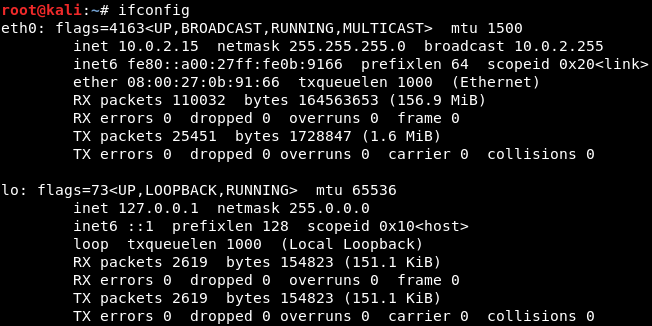
It's supplying an internet connection to the machine. At the moment, we don't have a wireless card connected to it. If we use iwconfig, we will see that the internet connection comes from eth0:

If we try to ping using the ping www.google.com -c 5 command, we will get responses back from Google, which means that the machine has an internet connection:

We will now connect the wireless card to the Kali machine; go to Devices | USB, and pick our card. The card should now show up when we run iwconfig:
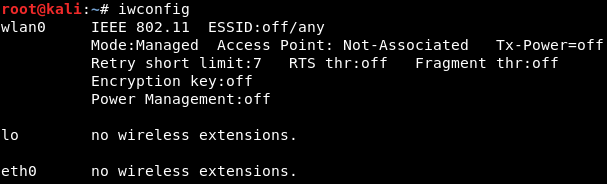
So, the wlan0 card is only used to broadcast the signal; it's not used to provide the internet connection. This card is in the managed mode, and it's not connected to any network.
Now, we're going to set up MANA's configuration and start the fake AP:
- First, we need to modify the hostapd-mana.conf file, which is located at /etc/mana-toolkit, using Leafpad editor. We are using Leafpad because this is the editor that we want to modify the file with. We will type the location where the file is located:
leafpad /etc/mana-toolkit/hostapd-mana.conf
- Here, we can modify the settings of the fake AP that we're using. The most important thing is the interface that we're going to use to broadcast the signal; for us, it was called wlan0. Remember that when we run iwconfig, wlan0 is our wireless card that's going to broadcast the signal, and it's not connected to anything. Now, we can modify the MAC address (or the name of the network); the name of the network, in our case, is going to be Internet, and the channel is going to be set to 6. We will not be modifying anything else; this was just to illustrate how to check the name:

- The other file that we want to modify is the start-nat-simple.sh script; this is the file that will launch the AP. Again, we're going to use Leafpad, and the command is as follows:
leafpad /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
- The first thing to do is make sure that you correctly set phy parameter; this will be your wireless card. We already know that the wireless card was called wlan0. Next, the upstream parameter is very important; we should specify the card that has an internet connection. In our case, it was called eth0, the virtual card made by VirtualBox. Again, if everything is set up correctly, we will not modify anything. Save the file:
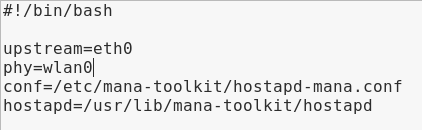
- Our last step will be to run MANA, and it will be running the start-nat-simple.sh script. Instead of using leafpad, this time, we're going to use bash, in order to execute the file. Our command will be as follows:
bash /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
Sometimes, we will get an error that says it cannot configure the file; in this case, just run the command again, and it should work the second time, as shown in the following screenshot:
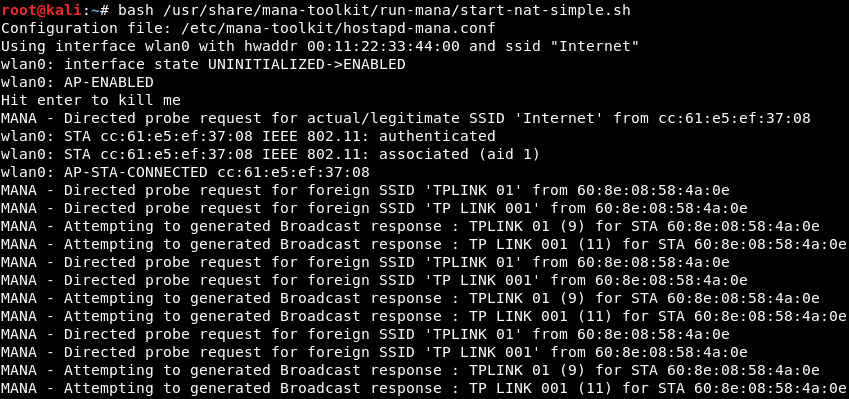
After this AP is running, we will go to our Windows machine and try to connect from it. We will be using another wireless card for the Windows machine, because the Windows machine will be a virtual machine as well. We can try to connect from our phone or from another laptop; do not connect from the host machine, because it will not have an internet connection (it is hosting the internet connection for everything). Either test the connection from your phone, from a separate laptop, or from a virtual Windows machine, but make sure to use a different wireless card.
- Going back to our Windows device, we are going to search for networks to connect to. As we can see in the following screenshot, we have an extra network, called Internet, and it has no password:
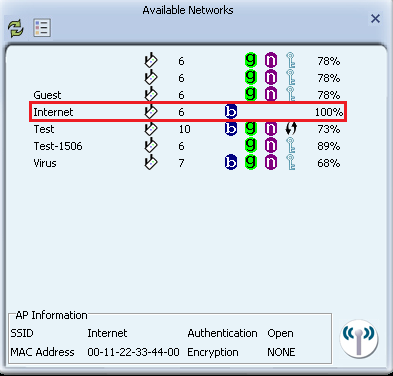
- We're going to try to connect to this network. Once we have successfully connected, we will see that we have an internet connection through the fake AP, and all packets are now flowing through this device:

The device is the AP, so it's like the router. We can actually use Wireshark (or any other tool), tcpdump, or TShark, to capture and analyze the packets.
