In this section, we are going to see how we can gain full control and get a Meterpreter session from the target computer. So, again, go to the Commands tab, and then Social Engineering. There are a number of ways that we can get a reverse shell. Now, it all depends on how we want to perform our social-engineering attack. We're going to use a notification bar, Fake Notification Bar (Firefox)—we're choosing Firefox because our target runs a Firefox browser:

Basically, it will display a notification bar telling the user that there is a new update or a plugin that they need to install. Once they install the plugin, they'll actually install a backdoor and we will gain full access to their computer. We'll implement it by using the same backdoor that we created and have been using throughout this book.
We have stored the backdoor in our web server in /var/www/html and named it update.exe, but it's the same backdoor, the same reverse-HTTP Meterpreter that we used before. Provide the full address of the backdoor inside the Plugin URL textbox, which is http://10.0.2.15/update.exe, change the Notification text to Critical update for Firefox, click here to install, as shown in the following screenshot, and hit the Execute button:

At the target, we can see that they're getting a message telling them that there is a new update for Firefox:
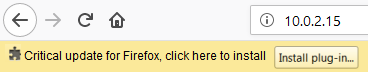
Once the target downloads and installs it, they'll have a backdoor downloaded onto their machine. Once they try to run this backdoor to install the update, they'll actually run a backdoor that will give us full access to their computer. Before we run the backdoor, we need to listen on the port, exactly as we did before. Open a msfconsole Terminal and run show options. Use the Metasploit multi-handler, the same way we've done throughout this book to listen on ports. Use meterpreter/reverse/http, we have our IP and the port. So, we are just going to run exploit, and we are listening for the connections now. Let's run the update we just downloaded. If we go on the target, we will see that we got full control over it using a Meterpreter session.
