Now let's have a look at a stored XSS example. Stored XSS is very similar to reflected XSS—it allows you to inject JavaScript code into the browser. The code is executed on the users that visit the page. The only difference is that, with reflected XSS, we have to send the URL to our target, so the target has to actually click on a URL for the exploit to run. With stored XSS, the code will be stored into the database—that is, into the page—so that every time a person runs that page, they will see our code and our code will be executed, so we won't need to interact with any users or send them anything. Therefore, this could be much more dangerous than reflected XSS.
So, let's have a look at this. Click on the XSS stored tab on the left. We will see a page, as shown in the following screenshot:
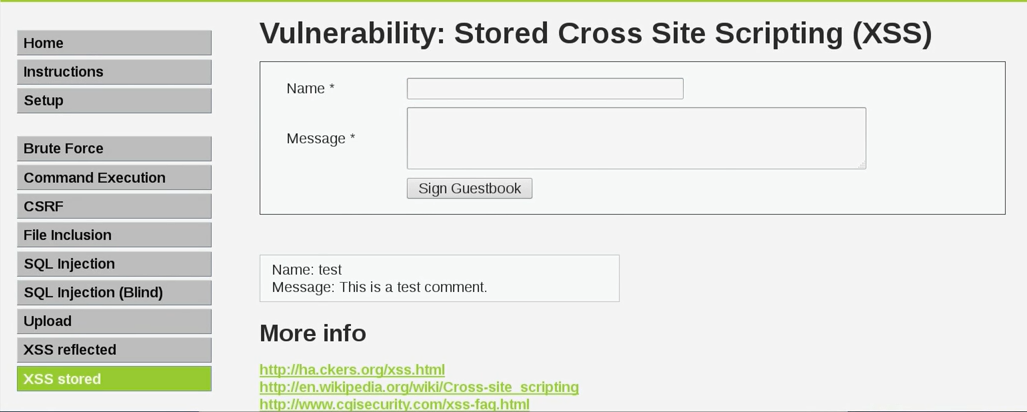
The page only allows us to add a message to the system. Now we are going to enter zaid in the Name textbox. We're just going to do a normal test to begin with. We're going to enter message body in the Message textbox, and then we are going to click on the Sign Guestbook button. We can see in the following screenshot that zaid added a message called message body:
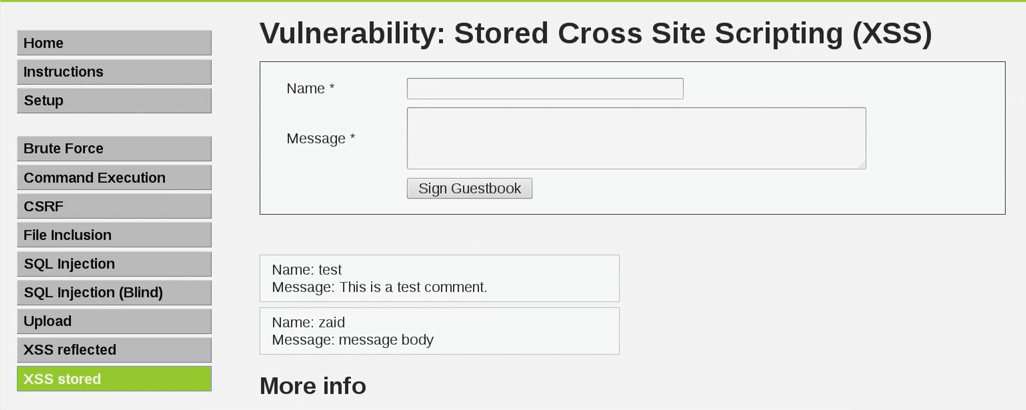
So, if we switch to a different DVWA machine in a different place and go to the XSS stored tab, we will be able see that there are two entries. The entries will be loaded from the database, and they contain the entries in that database. If we managed to inject code instead of a message, then the code will run on the machine of whoever runs this page without us even needing to send that person any code.
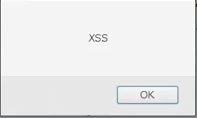
Let's try to inject into the DVWA that is running in the Kali environment. Let's enter the Name as zaid. We are going to try to enter our code in the Message textbox. We will enter it as <script>, and we are going to use the exact same test code that we used in the previous section, just a message saying XSS. Again, very basic code, but it serves for the purposes of this attack. We're going to make the code say alert("XSS"), and then we are going to click on Sign Guestbook button. So the code is as follows:
<script>alert("XSS")</script>
We will see that we get XSS displayed in the pop-up alert, but the real magic happens when a normal person accesses the page:
Let's assume that DVWA is just a normal website and people are just coming to browse it. Once they go to the XSS stored tab on the website, the JavaScript code will be executed on their system from the website. The code will come from the website and will be executed on each user that visits the page. Again, we're just implementing a proof-of-concept here; in the next sections, we'll see how to further exploit this kind of vulnerability.
