Let's learn how to discover these kinds of vulnerabilities. The method is very similar to SQL injection. First, you browse through your target and try to inject into any textbox or URL that looks similar. Whenever you see a URL with parameters, try to inject something=something as parameters, or try to inject into textboxes. Let's have a look at a reflected XSS example. These are the non-persistent, non-stored vulnerabilities where we have to actually send the code to the target, and once the target runs the code, it will be executed on their machine.
Let's have a look at our DVWA website and log into it. Inside the DVWA Security tab on the left-hand side of the following screenshot, we are going to set the Script Security to low:

As we can see in the following screenshot, we can enter your name in the textbox, and it's just going to say Hello zaid:
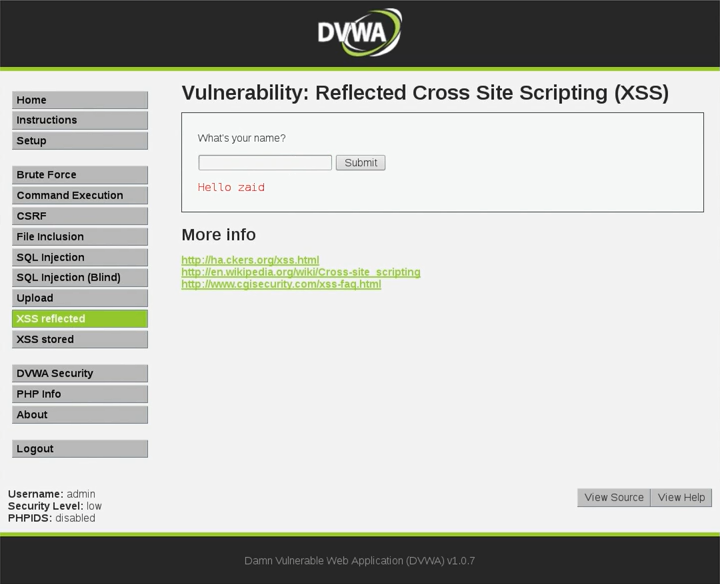
This is obviously just an example, but the idea is that you can inject into textboxes. Also, if we have a look at the URL 10.0.2.15/dvwa/vulnerabilities/xss-r/?name=zaid, we can see that it is using the GET method, so we can inject into the URL as well. Let us start the D-pad and try to inject XSS code on it and see whether the JavaScript code will be executed. We are using a very simple script, the <script></script> tag. There are a lot of ways of discovering these kinds of vulnerabilities and a lot of ways to bypass filters, but for now, we're just having a look at a basic example where we can inject a normal script and write <script>alert("XSS")</script>—which is just a function that gives an alert—to give it a textbox. Then we are going to click on Submit and see whether this code will be executed.
As we can see in the following screenshot, instead of saying Hello zaid, it says Hello; and our code has been executed, and it produces a XSS popup:

If we have a look at the URL 10.0.2.15/dvwa/vulnerabilities/xss-r/?name=<script>alert("XSS")<%2fscripts>#, we can see that it actually already did it for us. But if we copy and paste this URL on a notepad, we can see the script in the name parameter, and some CSS scripting.
Obviously, all of the characters are just HTML escape characters, and if we send the URL to anybody, then the code will be executed on the machine of whoever views the URL, and it's going to display a popup saying XSS. Let's see how we can also inject through the URL. Just to show the whole idea, we will use the URL 10.0.2.15/dvwa/vulnerabilities/xss-r/?name=<script>alert("XSS")</scripts>#. If we press Enter, the code will be executed. We can copy the URL and send it to a certain person, and once they run that code, the code will be executed on their machine.
