In this section, we will learn how to target a person. We are going to start with just a person's name, and then see how we can gather information about that person and build up an attack strategy. As we do that, we're also going to look at more of Maltego's features and how to configure a few more settings. So, we are going to start a new graph by clicking on the plus sign, as shown in the following screenshot:

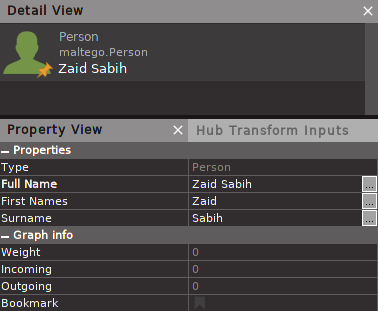
Inside the Entity Palette, search for a Person entity under the Personal section, and then drag and drop the Person entity to the workspace. We are going to assume that we have a target and we know their name, so the first name is Zaid and the surname is Sabih. We're going to go to the Property View tab and set the First Names property; just double-click it. We are going to set it to Zaid, and then we are going to set the Surname property to Sabih, as shown in the following screenshot:
Now, let's see what information can we gather about the entity created. Again, all we have to do is right-click the entity and see what we can get. So, we click on the PATERVA CTAS category, and we are going to go to All Transforms; we can get associated emails, we can try to get a phone number, and we can try to get a Twitter account; we can try all of these. For now, we are going to try to get a website, or websites, for this person:

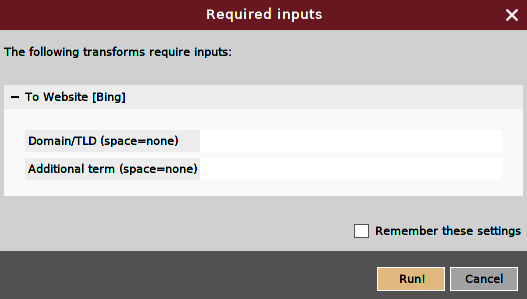
Now, it will ask us whether we want to look for a specific domain name. We are going to assume that we know nothing, so we are just going to put a space between two websites, in both entries. That just means looking for any websites that are associated with this person:
After clicking Run!, we should get a number of websites, and all of the websites are associated with Zaid Sabih:
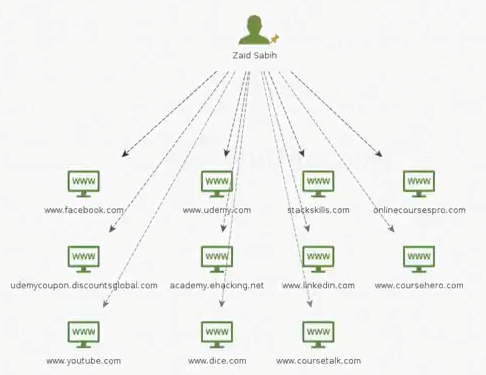
Now, that doesn't really mean that these websites are actually associated with our target, because there could be another person named Zaid Sabih, so we will have to go to each one and see which are actually related to that person. For example, we will double-click on the Facebook website to see the associated information. In Properties, we will see that we have the Facebook URLs that are associated with that particular name:
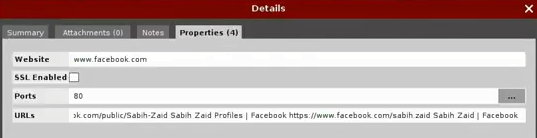
We can even copy the URL to a text file to read it better, and we can see in the following screenshot that we have three profiles:
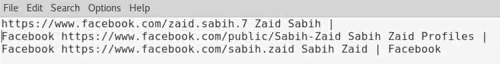
Now, in a real-life situation, we should go into each of these profiles and see which one is actually related to our person. In this example, we are not going to do that because three of them are actually not related to Zaid at all, so this is really not useful. In this case, we will just come back, move to the next entity, and see what's useful.
For our example, it's all related to our target. We can double-click each one of them, go to Properties, look for the URL, and open it in our browser. When we do that, we will get the information related to that person, and it will help us to form some sort of an attack strategy, or help us to get even more information. For now, because we have already looked at all of them, we are going to focus on one of them, which is the Udemy link, that is, the information related to our target on Udemy. We are going to double-click as we did before, go to Properties, get a URL, copy that URL, and open it in our browser. We can see that the URL is related to our target person, and we can see that it's leading us to a course taught by our target. Although this information is not really useful, we can now see that the target person is teaching online courses:

Go back and look at the other two URLs. If we browse the second URL, we can see it is showing us the profile for the target person:

By browsing the URL, we can gather information about the person. We can check all the websites to gather more information about them. Now, we need to keep in mind that we are setting our target—which is me, a person with knowledge of computers and information technology. When we are targeting normal companies or normal people, it will be easier to get effective information. If we look at their YouTube, LinkedIn, and Facebook profiles, we really won't get much. Even if we click on their Facebook profile, we will see that Facebook won't lead us to anything, we need to log in, and even after logging in, we won't get too much useful information. What's useful is if we go to their blog and go to the ABOUT section; what's useful here is that we have the email address of the target person, and we have their Twitter account:
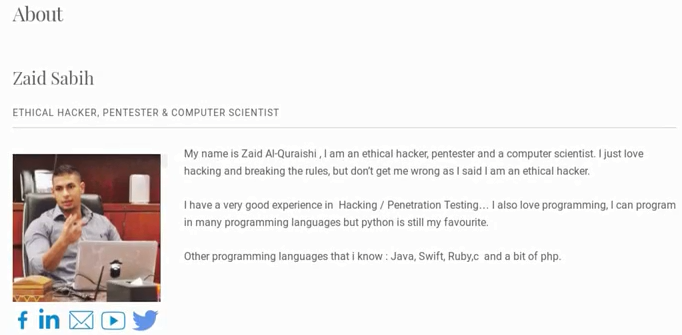
This information was not included on Udemy, and now we have two really useful pieces of information. In the next section, we'll see how we can use this information to gather even more info about our target, and hopefully be able to build up an attack strategy.
