So far, we've seen how we can capture passwords from any computer that is on our network, and we've seen how we can even bypass HTTPS to capture passwords from famous websites that try to use encryption. What if the target person never actually entered their password? What if they use the Remember Me feature, so when they go to the website they already get logged in into that website? That way, they never enter the password, the password is never sent to the server, and therefore we'll never be able to capture the password because it's not even sent. So, let's have a look at that.
So, we are on our target Windows computer. If we go to Dailymotion, we have already logged in there before and we clicked on the Remember Me feature. So, if we go to that website, https://www.dailymotion.com/ie, we will see that we will already be logged in to our account without having entered our password. In this case, the users actually get authenticated based on their cookies. The cookies are stored in the browser, and every time the person tries to go to the website they will be authenticated to the website based on the cookies. What we can do is sniff out these cookies and inject them into our browser, and therefore we'll be able to log into the account without entering the password, exactly the same way that the target person is being authenticated to their account.
To do that, we're going to use a tool called ferret, and ferret doesn't come installed with Kali. To install it, we are going to have to run apt-get install ferret-sidejack. Once we have that, first of all we're going to become the MITM using the same command that we've been using in the previous sections, using MITMf. Now, we can become the MITM any way we want, using arpspoof or any other tool.
Once we are the MITM, we're going to use ferret to capture the cookies. There is a ferret plugin that comes in with MITMf, but we are going to do it on the command line just to see how the whole process works together with another tool called hamster. We are going to run ferret, and running ferret is very simple. All we have to do is just type in ferret, and then we put our interface, which is eth0 in our case. Again, if we are using our wireless card, then put as the interface the name of our wireless card. The command is as follows:
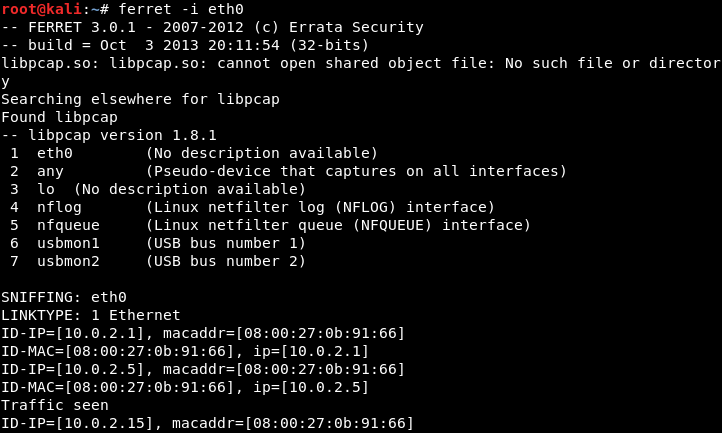
ferret -i eth0
Ferret is running now and it's ready to capture cookies. In fact, it's already capturing cookies:
We're also going to start a graphical interface, a web GUI, that will allow us, to inject the cookies and navigate into our system's session. To do that, we're going to use a tool called hamster, and running hamster is even simpler than ferret. All we have to do is just run hamster, and we're ready to go:

So, everything is ready now. We are going to go into our target and log in to our account. So, we are just going to pretend that we are browsing the internet. We're going to go to Udemy. We will just go to the website, and we'll authenticated automatically without having to enter anything such as a username or a password. Now, let's come back to the Terminal, and as we can see, we have managed to capture the cookies:

We are going to copy the proxy link that hamster gave us, which is http://127.0.0.1:1234, and we are going to go to our browser. Now, we need to modify our proxy settings to use hamster, so in our Kali browser we're going to go to Preferences | Advanced | Network | Settings, and we're going to set it to use a manual configuration, and we're going to set the port to 1234.
So, we're using 127.0.0.1, which is our local address, and the port is 1234:

Click OK, and then we're going to navigate to the URL given to us by ferret, which is 127.0.0.1:1234:
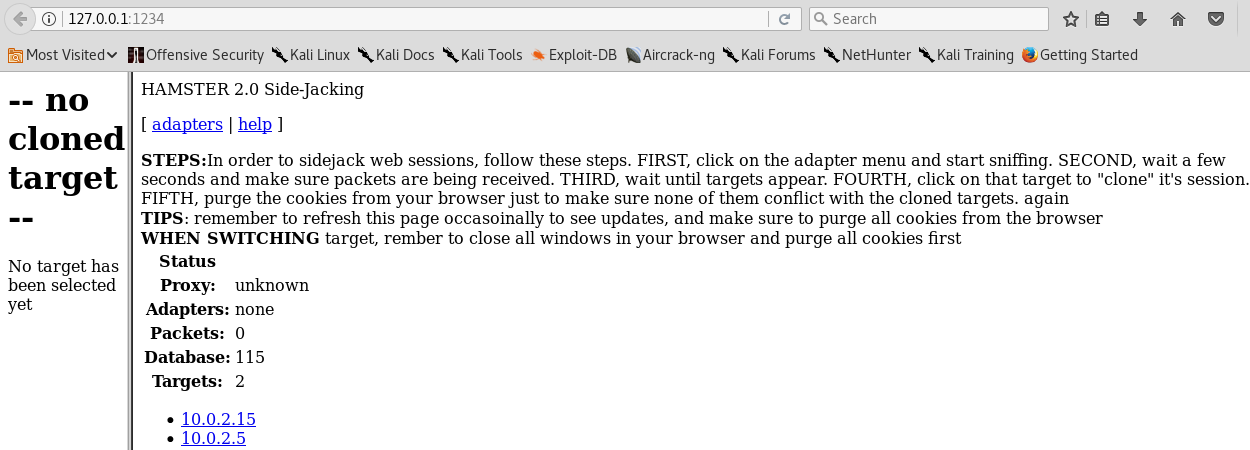
We go and select our adapter by going into adapters and entering eth0. Then, click Submit Query:

We can see that here we have two targets:

Our target is 10.0.2.5; that's our target IP. We are going to click on it, and as we can see in the following screenshot, on the left we have all the URLs that contain cookies related to our target:

Obviously, a lot of URLs listed are ad websites or ad URLs, but we can see that one of the URLs is for Udemy.com, and if we click on it, we will be actually logged in without having to enter a username or password. So, we can go into the channel and do anything that the target person is able to do without using the username and the password, and this is all possible because we stole the cookies that the person actually used to authenticate themselves with the website.
