Now we are going to look at another way to discover malicious files, by using a sandbox. A sandbox is basically a place where our file will be executed and analyzed. It will check whether any ports will be opened, if it's going to modify registry entries—basically, if it's going to do any suspicious stuff. It's not an antivirus program. Our Trojan might pass antivirus programs, our Trojan passed all antivirus programs, but the sandbox applications, or the sandbox environments, will run it in a controlled environment, see whether it does anything suspicious, and give us a report. We can Google sandbox online, and an example of it is a website called Hybrid Analysis (https://www.hybrid-analysis.com/).
Using the website is very simple: just go to the URL, select a file, and upload it. We can see the report in the following screenshot; analyzing the file and generating the report might take some time:
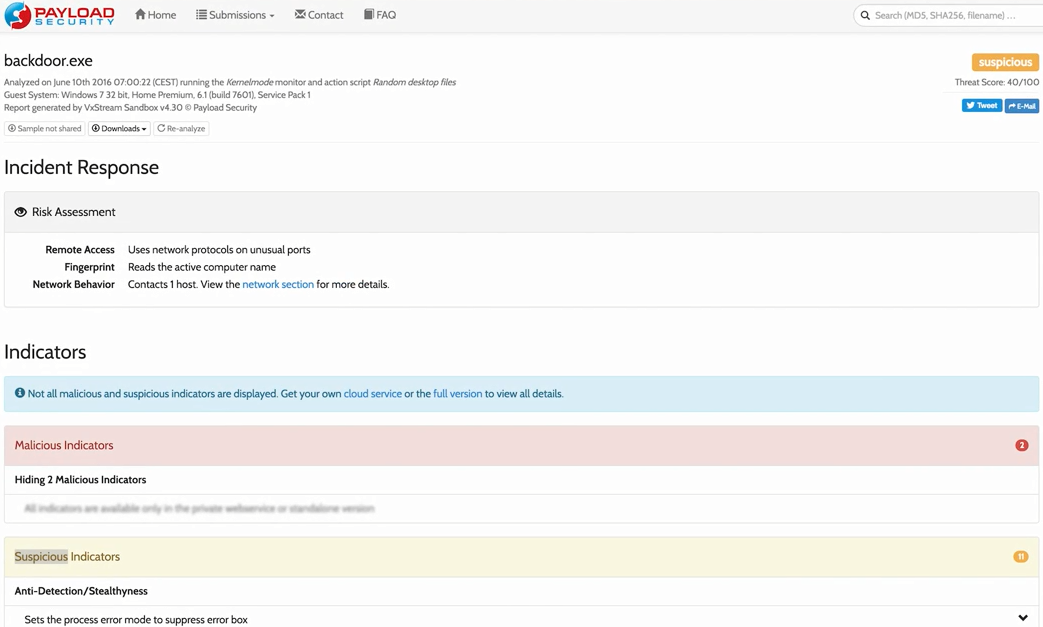
Once we get the report, we will see some basic information; we will see that Malicious Indicators have been found. They're hiding it from us and we have to use the full version to see them, but we don't really need to see them; if we read the whole report, we will know that this file is malicious and it's going to do something bad on our computer.
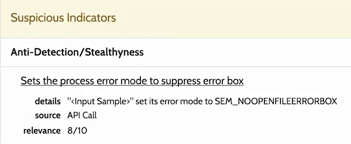
We can see that the file suppresses error boxes, so it doesn't display error boxes:
It also modifies the registry, and we can see the registry parameters in the following screenshot:
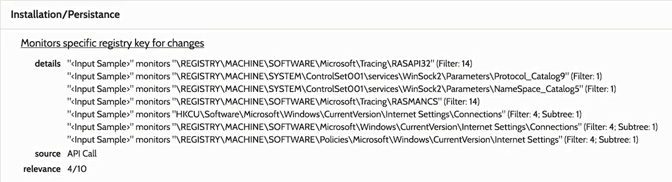
We can see, in the preceding screenshot, that it's playing with the Internet Settings and with the Connections. We can also see that it's using the Windows Sockets service, that is, WinSock2, so it's trying to create connections. We can also see that it's playing with the address of the process:

If we scroll down, we will see one of the most important indicators. There will be more information in the following screenshot on Network Analysis. It tries to connect to Host Address on Host Port 8080:
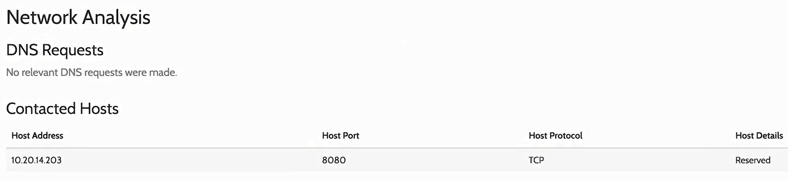
We can go on the 10.20.14.203 IP and do a reverse DNS lookup to check whether the IP is related to a website. Also, when we upload the payload, it's never going to be executed on our computer, it's going to be executed on their server in a sandbox environment. Now, obviously, for the method we have seen, we should always use it in a VirtualBox when we are executing it on Windows. Always perform it on a virtual machine; don't perform it on our main machine. Or we can upload it into a sandbox environment, it'll be analyzed for us, and then we can read the report.
