Through the previous section, we know that to crack a WEP key, all we have to do is sniff packets from the target network and gather as many IVs as possible. Once we have done that, aircrack-ng will be able to use statistical attacks to determine the key stream and the WEP key for the target network. Obviously, when we have more than two packets, the method is going to work better, and our chances of breaking the key will be higher—we're going to try to gather as many IVs as possible.
Let's look at the most basic case of cracking a WEP key. Wi-Fi card must be in monitor mode, and the first thing we're going to try to do is see all of the networks that are within our Wi-Fi range; then, we're going to target one of those networks. We're going to run airodump-ng wlan0, very basic command, where wlan0 stands for the interface. Following will be displayed as a output:
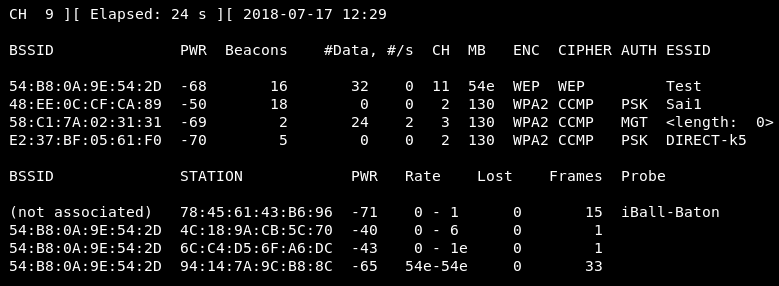
The first network that has come up is Test; this is the network that we're going to perform our attacks on. We're going to launch airodump against Test network by using the following command:
airodump-ng --bssid 54:B8:0A:9E:54:2D --channel 11 --write basic-test-ap wlan0
Here, we enter the --bssid and launch an airodump against Test AP. We include the --channel, number 11, and we add --write to store all of the packets that we capture into a file, which is basic-test-ap. As we run the preceding command, we will be able to see the output in the following screenshot, the target network that we have as the data we gathered it is quite a busy one, also the data and the frames are going:

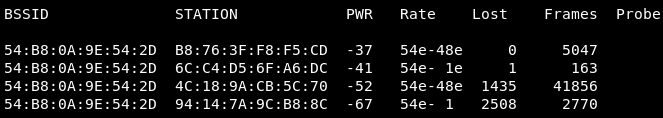
It is a busy network; the following is the section where we can see the clients:
All we have to do now is launch aircrack-ng, which is part of the aircrack suite, against the file that airodump has created for us. We can launch aircrack against it even if we didn't stop airodump; it will keep reading the file, and it will read the new packets that airodump is capturing. The command to use is as follows:
aircrack-ng basic-test-ap-01.cap
When we use aircrack-ng, we will put in the filename basic-test-ap-01.cap. While the file is still being created, getting larger and larger with the inclusion of new packets, we can run aircrack-ng, and it will keep getting updated, eventually giving us the password we need for cracking. If aircrack fails to determine the key, aircrack waits until it reaches 5,000 IVs, and then tries again.
The number of IVs actually depends on the type of WEP encryption. There are two types of WEP encryption: 128-bit and 64-bit. The only difference is the length of the key; obviously, 64-bit requires a lower number of IVs than 128-bit. Remember that when we discussed aircrack, we indicated that the more packets we get without unique IVs, the higher our chances of cracking the WEP key are.
Now, we basically wait until aircrack can successfully crack the WEP key. Once it decrypts the key, we can press Ctrl + C. As we can see in the following screenshot, aircrack has successfully managed to get the key within data packets; this is because the target AP uses a 64-bit key:

Let's look at how we can use this key to connect to the network. We are going to copy the key and use the key too connect. We can then connect to the target network:

As you can see, our connection has been established; we successfully recovered the WEP key from the target network. We can go ahead and confirm by pinging Google:

