In order to prevent our network from preceding cracking methods explained throughout the chapter, we'll need to access the settings page for your router. Each router has a web page where user can modify the settings for the router, and it's usually at the IP of the router. First we're going get the IP of my computer or my device, and we are going to run ifconfig wlan0 command; as seen in the following screenshot, the highlighted part is the IP of the computer:
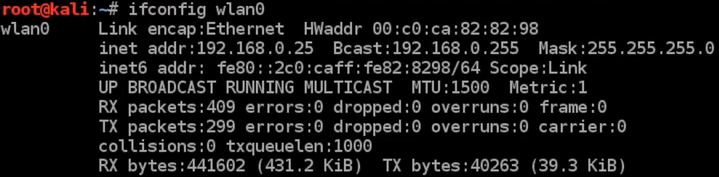
Now open the browser, and navigate to 192.168.0.1; for this example, the IP of the computer is 25. Usually, the IP of the router is the first IP of the subnet. At the moment, it's 192.168.0.0, and we are just going to add the number 1, because that's the first IP in the subnet, and that will take us to the router settings page. At the settings page, it'll asking to enter a username and a password. Routers come with a pre-specified username and password—we can check what the default username and password are; it's highly recommended to change them afterwards. It's usually written in the manual, so check the manual, see what the default username and password are, and then log in using those credentials.
Now, in some cases, the attacker might be doing a deauthentication attack against us, so the attacker might be preventing us from connecting to our network wirelessly. What we can do is connect to the router using an Ethernet cable; when we do that, the attacker cannot use a deauthentication attack to deauthenticate or disconnect us, and we will be able to access the router settings using the wire. We can modify our security settings and change the encryption, change the password, and do all of the things that are recommended in order to increase the security, so that the attacker will not be able to attack the network and get the key.
Now, the settings of each router are different; they depend on the manufacturer, and even the model of the router. But usually, the way that we change the settings is the same; in 90% of the cases, the router is always at the first IP of the subnet, all we have to do is get your IP using the ifconfig command, like we did at the start of this topic. We got the 192.168.0.25 IP, and then we changed the last 25 to the number 1 to the first IP, and that is the IP of our router.
Now, we are going to navigate to the WIRELESS settings. As we see, there are a lot of settings that we can change for our network, and we're concerned with the WIRELESS settings at the moment:

As we can see in the preceding screenshot, the wireless setting is Enabled, we can even change the name of the network under SSID; we can change the Channel and the Bandwidth, as well.
After going to the Security option, we can see in the following screenshot, we are using WPA encryption with WPA/WPA2 authentication, and the encryption uses AES+TKIP:
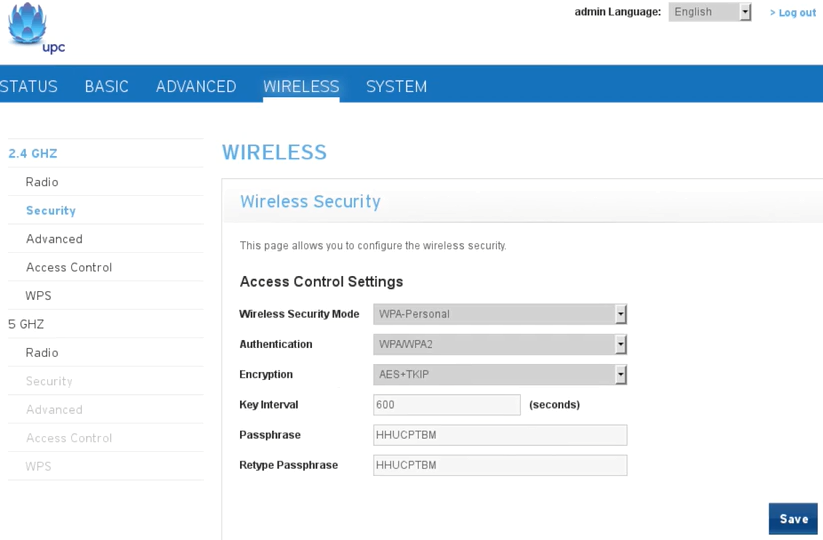
If we go on WPS, we can see that WPS is Disabled; we are not using WEP, so that attackers cannot use any of the attacks to crack WEP encryptions:

We are using WPA, which is much more secure, and we have disabled WPS, so that attacks cannot use reaver to determine the WPS PIN and then reverse-engineer the password. The only way that the hacker can access or get the password is by obtaining the handshake first, and then using a wordlist to find the password. The password is very random, even though it doesn't actually use numbers or digits, just letters; but it's very random, so there are very small chance of someone being able to guess it.
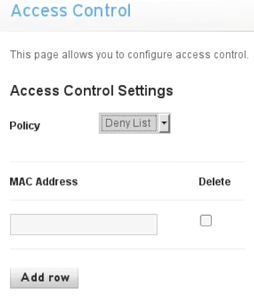
Now, there is also the Access Control; using this, we can add policies, such as an allow policy or a deny policy:

We can specify MAC addresses that we want to allow to connect to our network; we can also specify MAC addresses that we want to deny from our network. For example, if there are not many people or many visitors coming to your house, or if you are in a company with a specified number of computers and only want to allow a number of computers to connect to the network, you can obtain their MAC addresses (for the people that you want to allow) and add them onto an Allow List. Even if someone has the actual key, and they don't exist in the whitelist or in the Allow List, they will not be able to access the network. We can also add a Deny List when we want to deny a certain computer or a certain person that we think is suspicious; we can just add their MAC address onto the Deny List, and they will not be able to connect to your network:
The router settings page usually looks different for different routers; the names for options might be different, but the main point is that we should be able to access the router settings using the subnet IP and adding the number 1, which is the first IP, at the end. If you are being attacked and can't connect to your network at all, then just use a cable and modify the settings, like we discussed.
